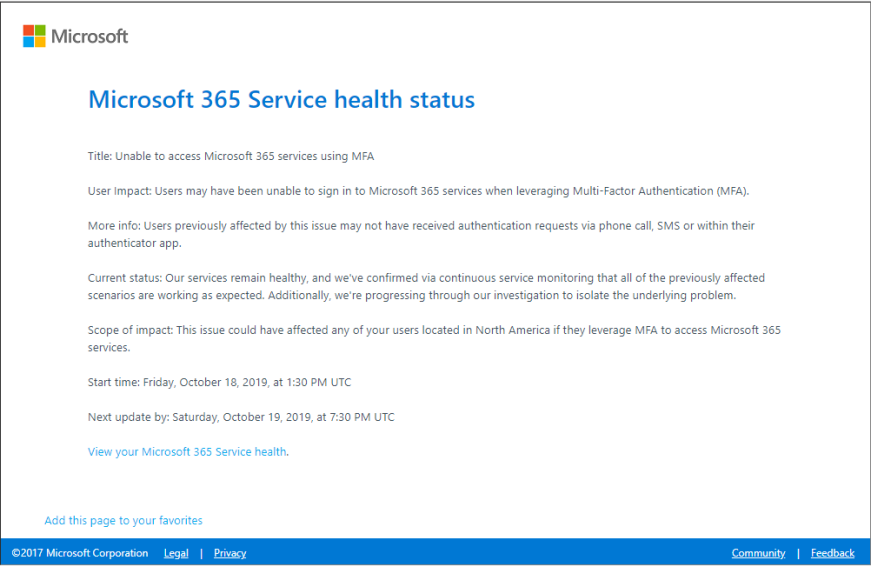
Most people reported that ‘they are unable to sign in to their Microsoft Office 365, Azure Active Directory and other services’. This issue is due to the multi-factor authentication issue (Microsoft MFA outage), which hit users in North America and left them unable to sign into their services.
Microsoft users faced Multi-Factor Authentication (MFA) issue for about 2.5 hours on October 18, 2019. Users are unable to receive the second layer of authentication like SMS, call or push notification to login to Microsoft.
Microsoft has confirmed the issue in the Azure status page as follows:
Summary of Impact: Between 13:30 UTC and 16:50 UTC on October 18, 2019, a subset of customers in North America may have experienced issues with completing MFA challenges.
Preliminary root cause: Engineers are continuing to investigate the root cause. A follow-up RCA will be provided in the coming days.
Mitigation: Engineers have taken corrective actions, and services have been largely recovered. Engineers will continue to monitor the environment to ensure it remains stable, and customer scenarios remain unaffected.
Next steps: Engineers will continue to investigate to establish the full root cause and prevent future occurrences, and additional details regarding mitigation will be provided in the RCA.
So far, there’s no apparent reason for the outage, and the company is still investigating the issue. Within the next few days, a root-cause analysis will be ready for release to the public.
Office 365 Outage History:
This kind of outage has happened twice already.
January 29,2019 – European users were unable to login to their Office 365 services.
November 19, 2018 – Office 365, Azure users are locked out after a global multi-factor authentication outage.
Microsoft Office 365 MFA Outage: No Failover?
Microsoft really amazes me sometimes why there was no failover method when such incidents happened, which causes wide consequences.
As a workaround, you can follow any one of the below failover methods.
- You can have an admin account with conditional access(Where MFA doesn’t apply) like a trusted network, trusted location, or a compliant device. Using that account, you can disable MFA for all users for outage duration.
- An organization needs to use an emergency access account. Emergency access accounts are highly privileged, and they are not assigned to specific individuals. These accounts are limited to an emergency scenario like MFA outage, where regular administrator accounts can’t be used.
Note: If you are a Microsoft partner, you must have MFA enabled and impossible to have an any workaround.
I hope you will take the necessary steps to stay out of these kinds of outages! If you are using any other methods, share with other admins and us in the comment section.