According to Microsoft 365 notification MC736438, Microsoft is getting tougher at enforcing the rules for Purview information protection licenses. In a nutshell, if administrators and end users don’t have premium licenses, features like automatic labeling policies or default sensitivity labels for document libraries won’t work. Users can still apply sensitivity labels manually.
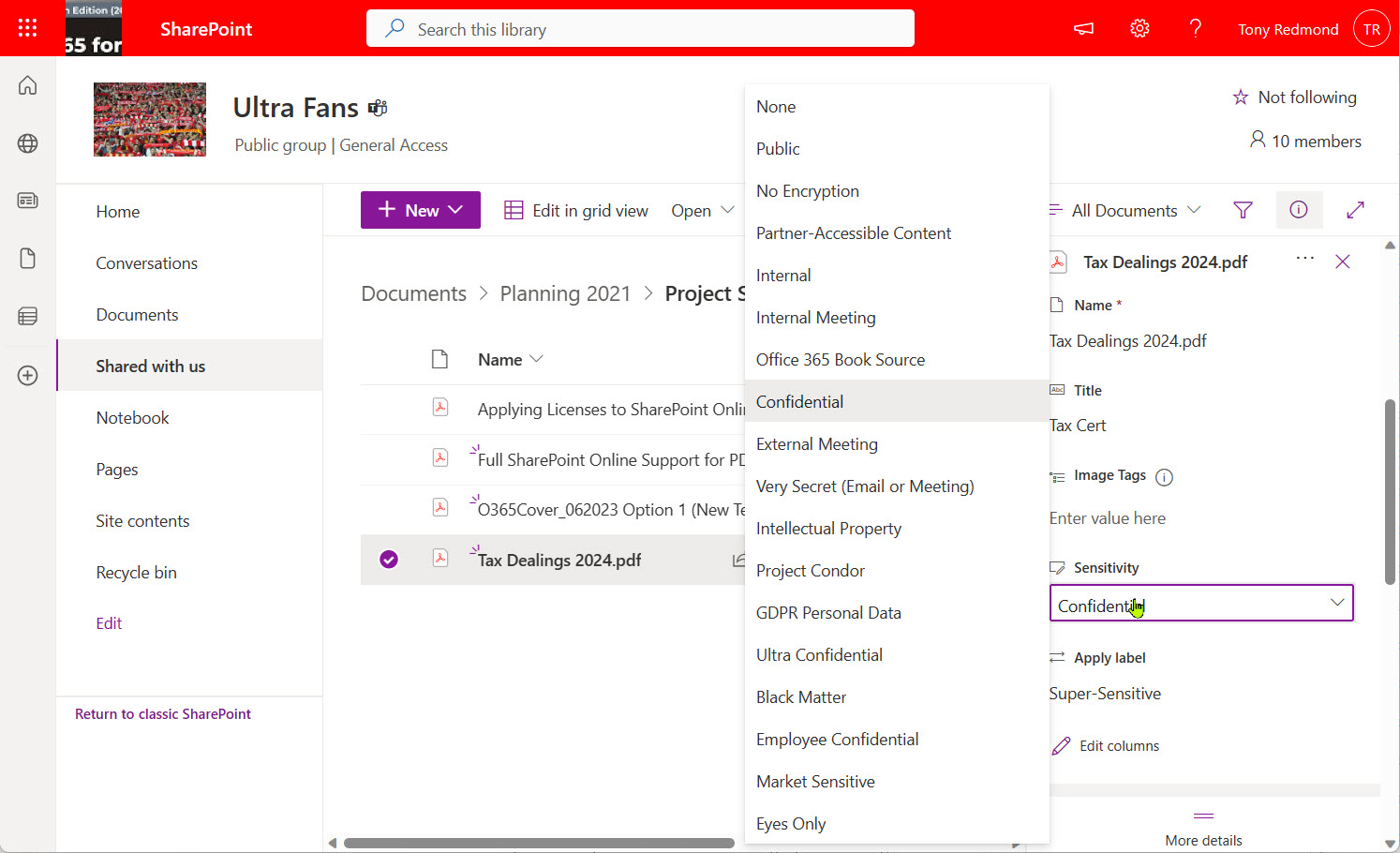
Sensitivity Label PDF support is now available in SharePoint Online and OneDrive for Business. In effect, this means that SharePoint can protect and process PDFs in the same way as it handles Office documents. Given the widespread use of PDFs in many organizations, this is an important step forward for those wishing to protect their most sensitive information.
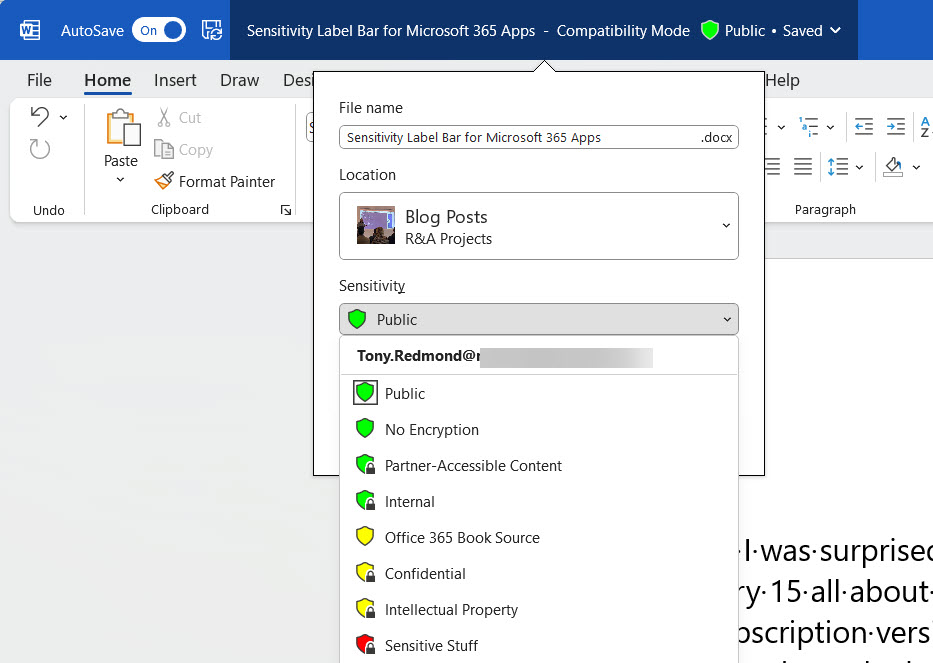
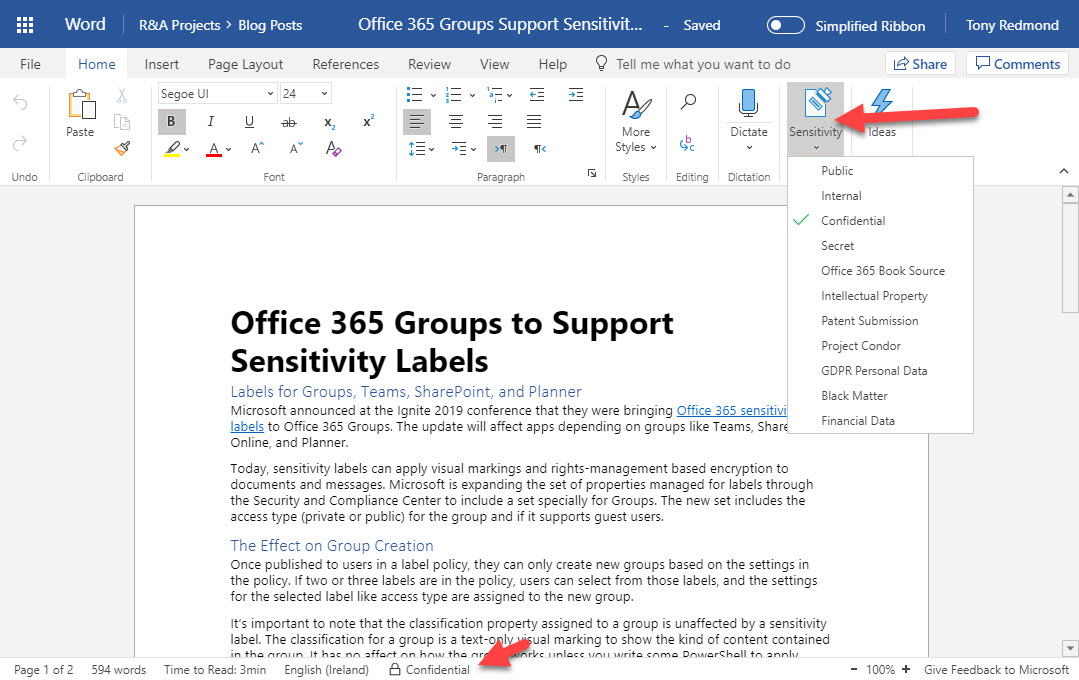
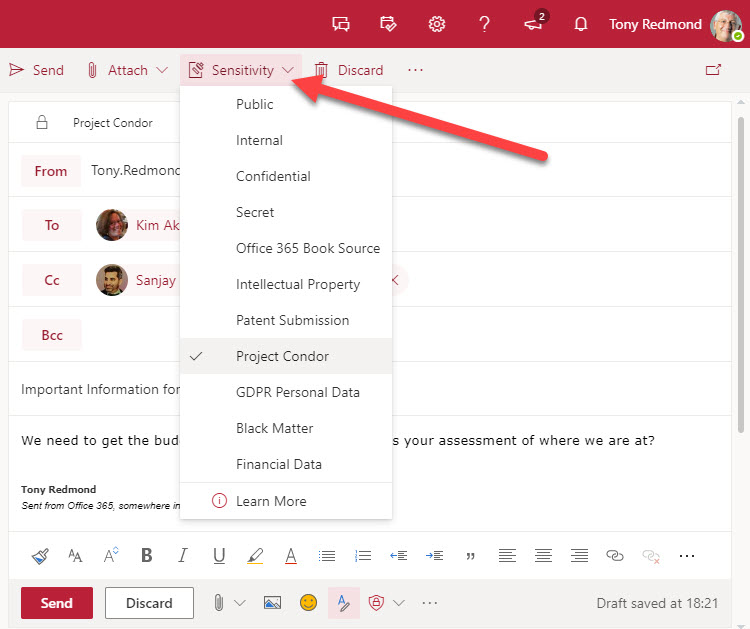
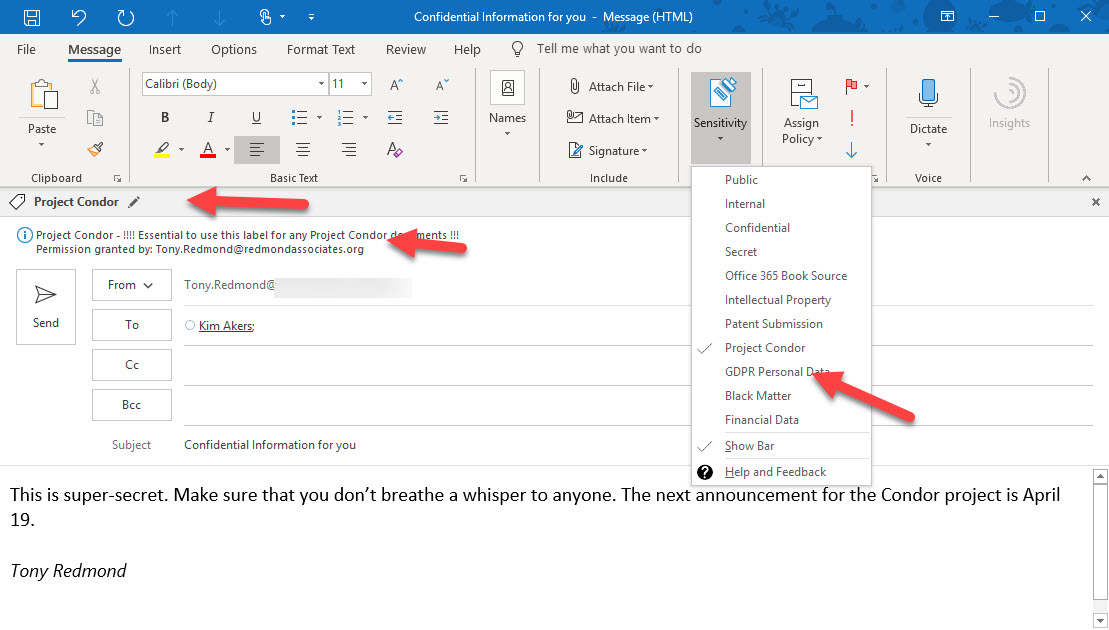
The subscription versions of the Office desktop apps now boast a sensitivity bar to show users what sensitivity label applies to the document they’re working on. It’s a good change because it means that people have full access to information about available labels. You can opt to hide the sensitivity bar, meaning that you hide the name of the sensitivity label rather than the complete bar.
Delegates often process Outlook email for others. It’s a feature that works well. That is, until protected email arrives. Delegates shouldn’t be able to read protected email in other peoples’ mailboxes. But some versions of Outlook allow this to happen. If you want to be sure that delegates can’t access protected email, maybe you should consider using a dual-mailbox approach.
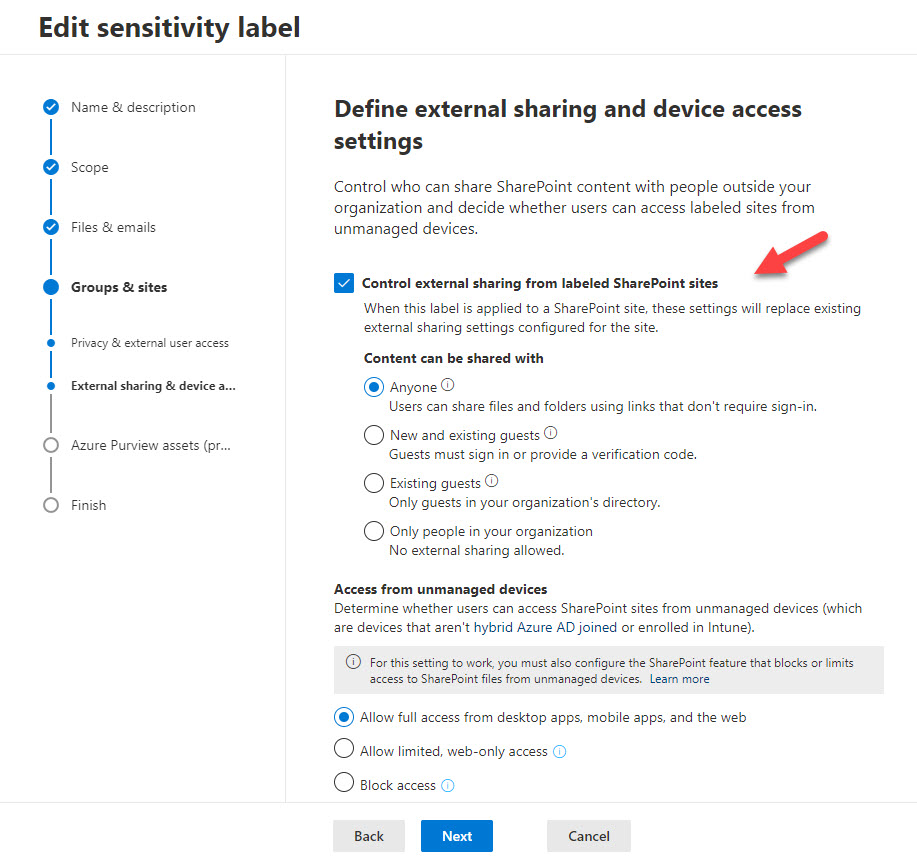
The latest update for sensitivity labels allows them to control the external sharing capability of SharePoint Online sites. It’s a powerful example of policy-based management in action and demonstrates just how useful sensitivity labels will be as Microsoft steadily builds out the set of controls available through labels.
The latest version of the Edge Chromium browser can read files protected by Office 365 sensitivity labels stored in SharePoint Online and Exchange Online. This might not be the feature that causes you to dump Chrome, but it’s very useful when your tenant uses sensitivity labels.
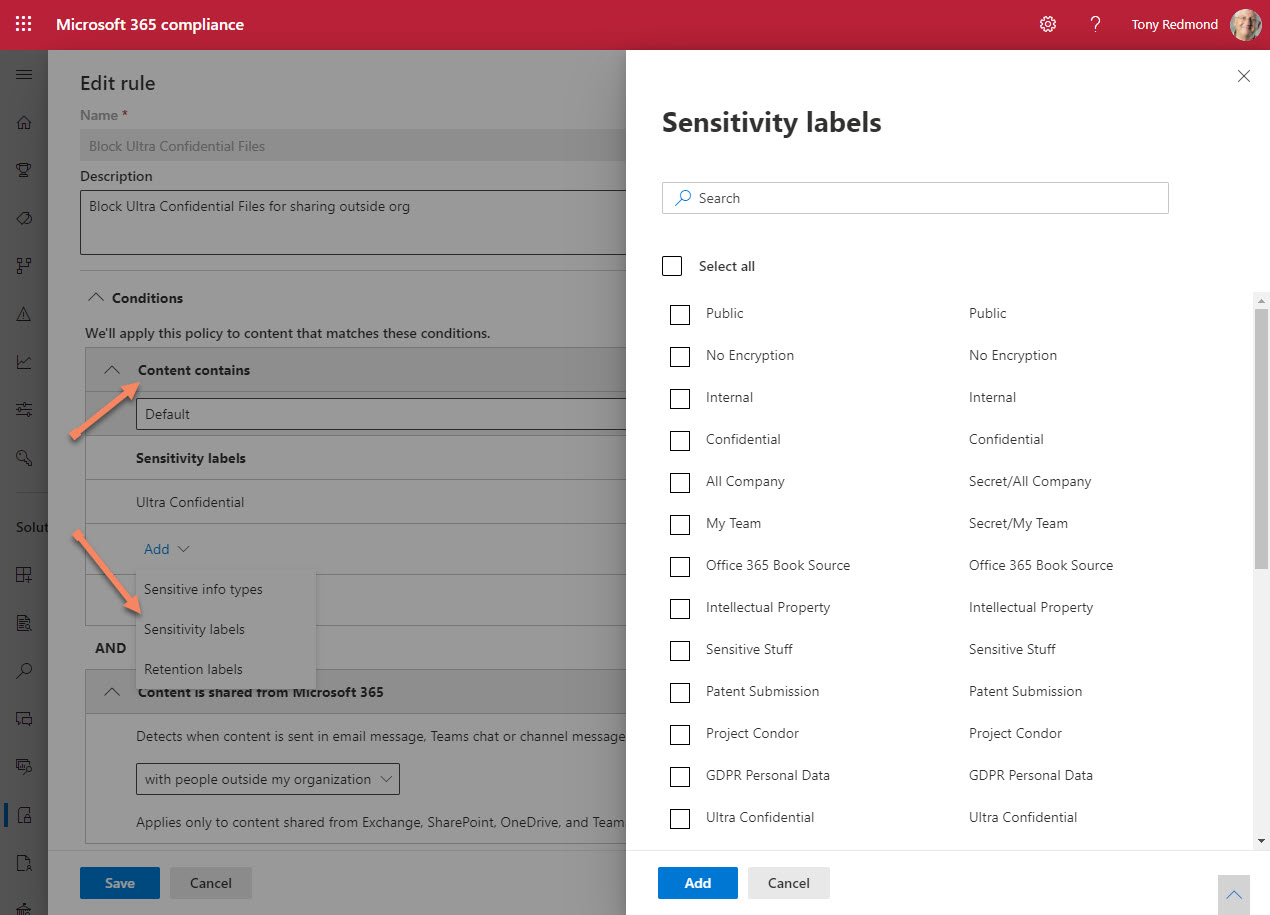
When you need to block external access to your most sensitive documents, Office 365 Data Loss Prevention policies and sensitivity labels combine to find and protect the documents. A really simple policy is enough to detect and block external access, and is covered by Office 365 E3 licenses. If you have E5 licenses, you can consider auto-label policies to find and protect sensitive documents at scale.
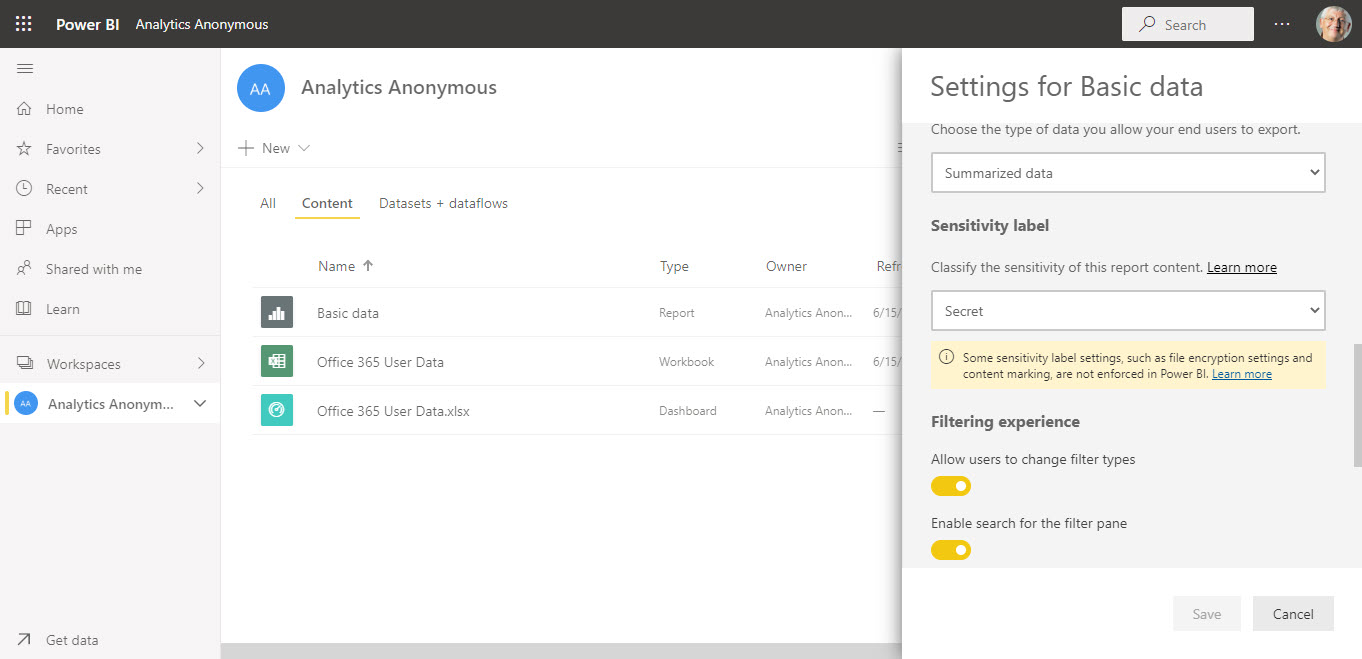
Power BI support for Office 365 sensitivity labels is now generally available. Inside Power BI, the labels are visual markers. Encryption is applied when Power BI objects are exported. The interesting thing is that the user who exports content doesn’t have the right to change the label.
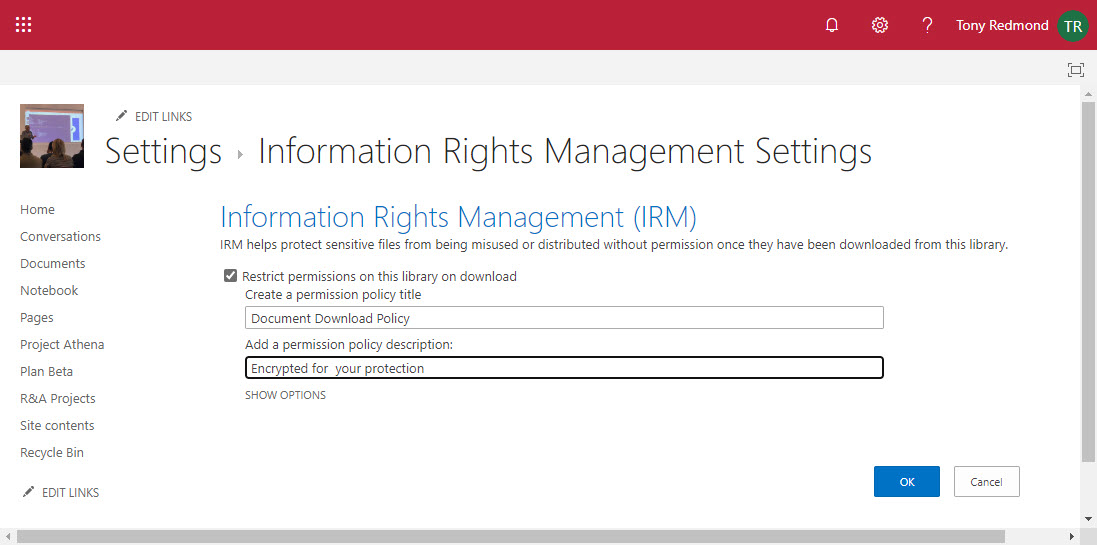
Now that SharePoint Online supports Office 365 Sensitivity Labels, it’s time to consider how to protect files stored in document libraries. When you compare the two approaches, there’s really only one winner. And there’s no surprise in saying that the winner is Office 365 Sensitivity Labels.
At the Microsoft Ignite 2019 conference, Microsoft described how SharePoint Online will use Office 365 compliance features such as sensitivity labels and information barrier policies to better protect information stored in SharePoint sites. The Office Online apps also gain support for sensitivity labels. The new features will enter a mixture of public and private previews starting November 20.
OWA now supports Office 365 Sensitivity Labels, which means that users can apply labels to mark and/or protect messages with encryption just like they can with Outlook. The update adds to the ways that sensitivity labels can be applied to Office 365 content, with the next step being to achieve the same support for the other online Office apps.
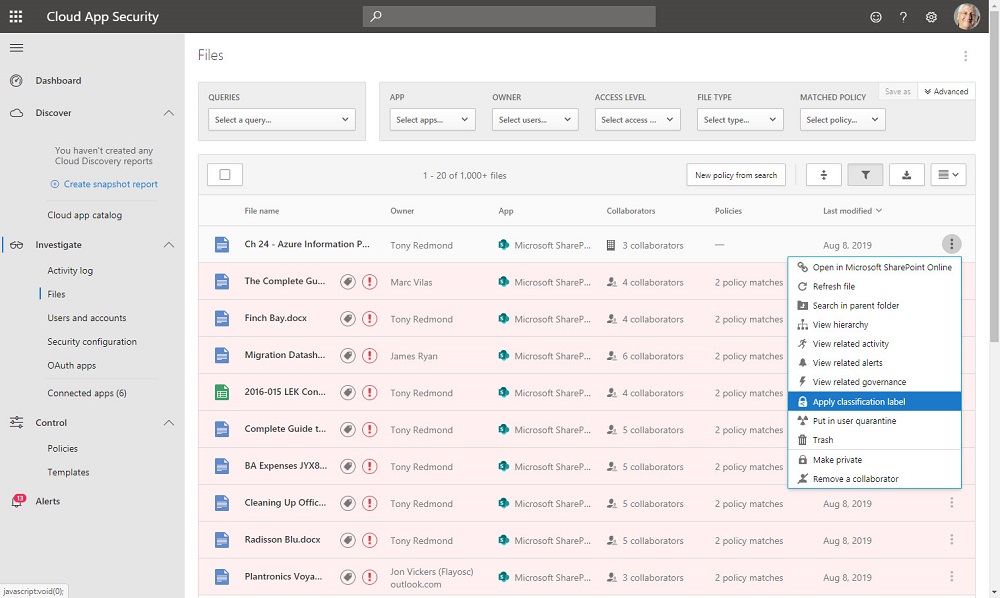
Microsoft Cloud App Security (MCAS) can integrate with Azure Information Protection to allow automated policy-driven application of Office 365 sensitivity labels to Office documents and PDFs. You can depend on users to apply labels manually as they create documents, but it’s easy for humans to forget to add protection where a computer won’t. You’ll pay extra for MCAS, but it could be worthwhile.
Microsoft has announced the deprecation of the PowerShell module for the Azure Active Directory Rights Management service (AADRM). But don’t worry; it’s replaced by the Azure Information Protection (AIPService) module. Deprecation happens in July 2020, so you’ve lots of time to revise any scripts that use AADRM cmdlets.
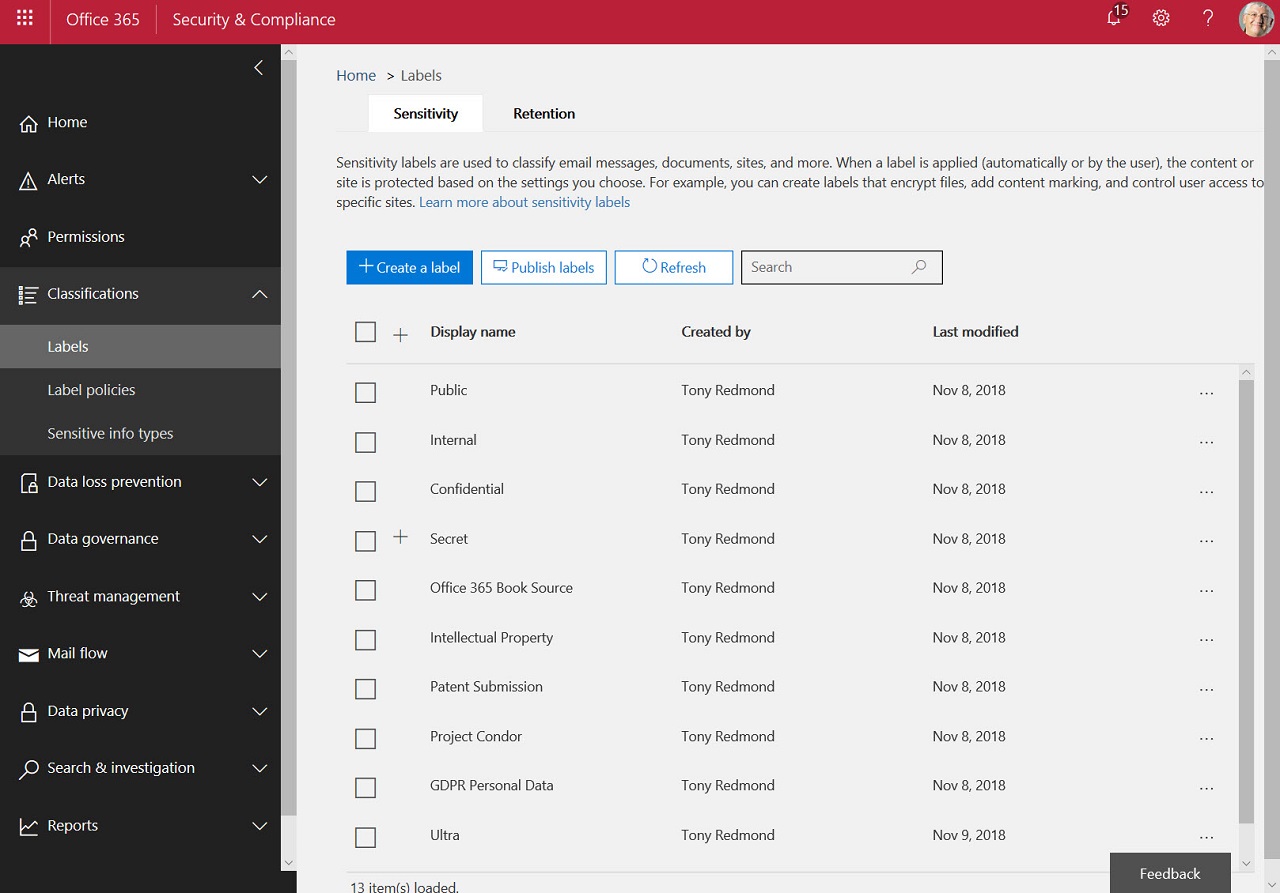
The process of introducing Office 365 sensitivity labels to a tenant can be long and complicated because of the need to plan how to manage encrypted content. As you go through the process, don’t delete labels if they’ve already been used to protect content. Instead, remove them from the label policies used to publish information to clients. The labels will then remain intact in documents and other files.
Microsoft has released the GA version of the Azure Information Protection client, which reads information about Office 365 sensitivity labels and policies from the Security and Compliance Center. It’s one more step along the path to making it easy for Office 365 tenants to protect their data. Work still has to be done, but at least we can see light at the end of the encryption tunnel.
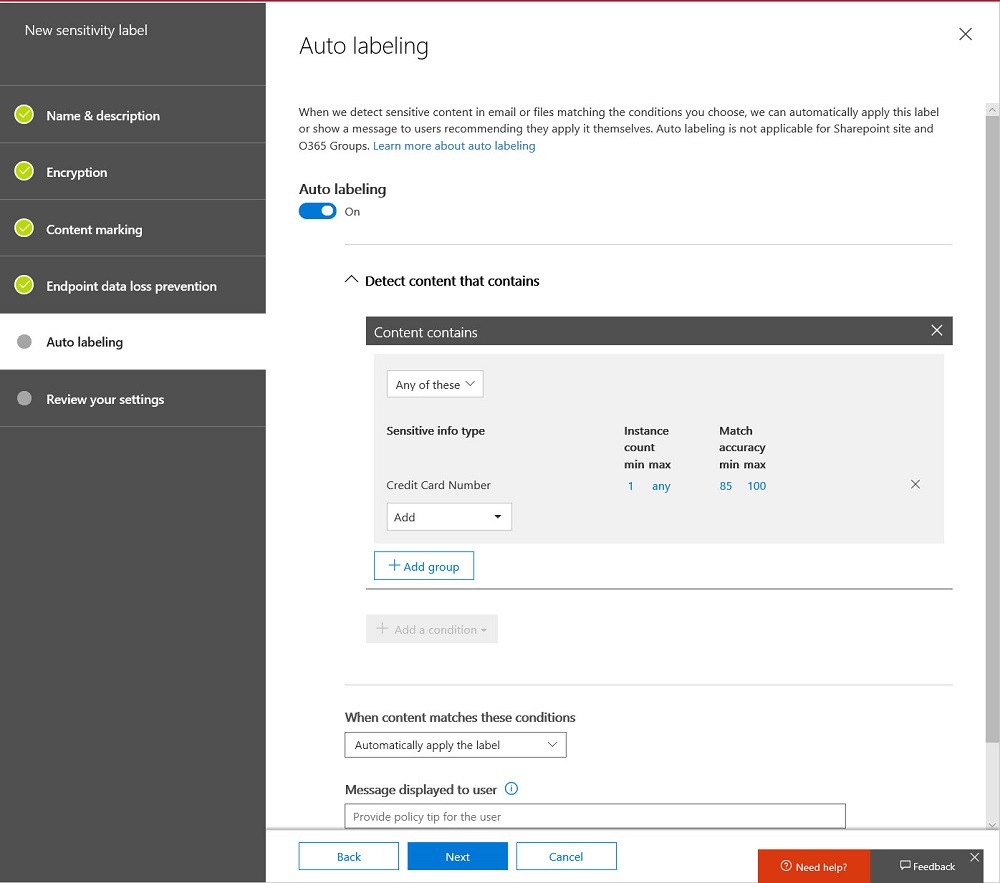
Microsoft released an update for the unified labeling version of the Azure Information Protection client needed for Office 365 sensitivity labels, which now boast auto-label support. Solid progress is being made to move sensitivity labels to the point where they are considered to be generally available, probably later this year. In the meantime, pay attention to the premium features like auto-label which require more expensive licenses.
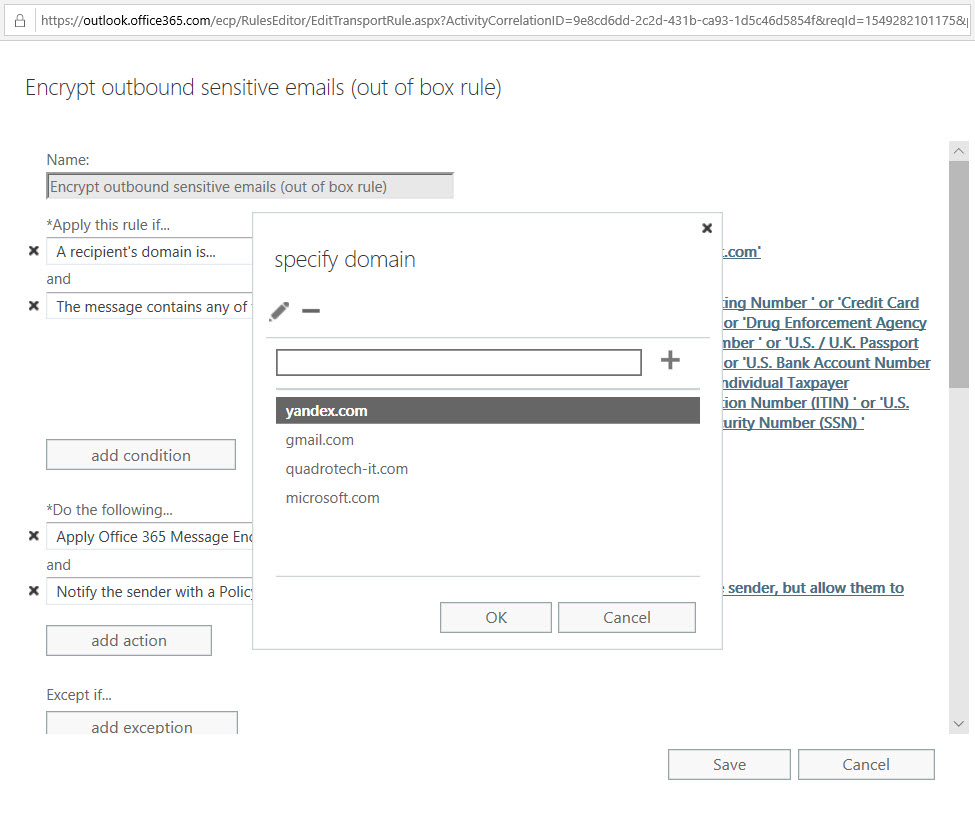
Microsoft has released details of an Exchange Online transport rule to encrypt outbound email containing sensitive data types like credit card numbers. The rule works (after fixing the PowerShell), but needs to be reviewed and possibly adjusted to meet the needs of Office 365 tenants.
Office 365 tenants can use Exchange transport rules to apply autosignatures to outbound email, including messages protected with encryption. You can even include some properties of the sender extracted from Azure Active Directory, and you can add an exception so that the autosignature isn’t applied to replies.
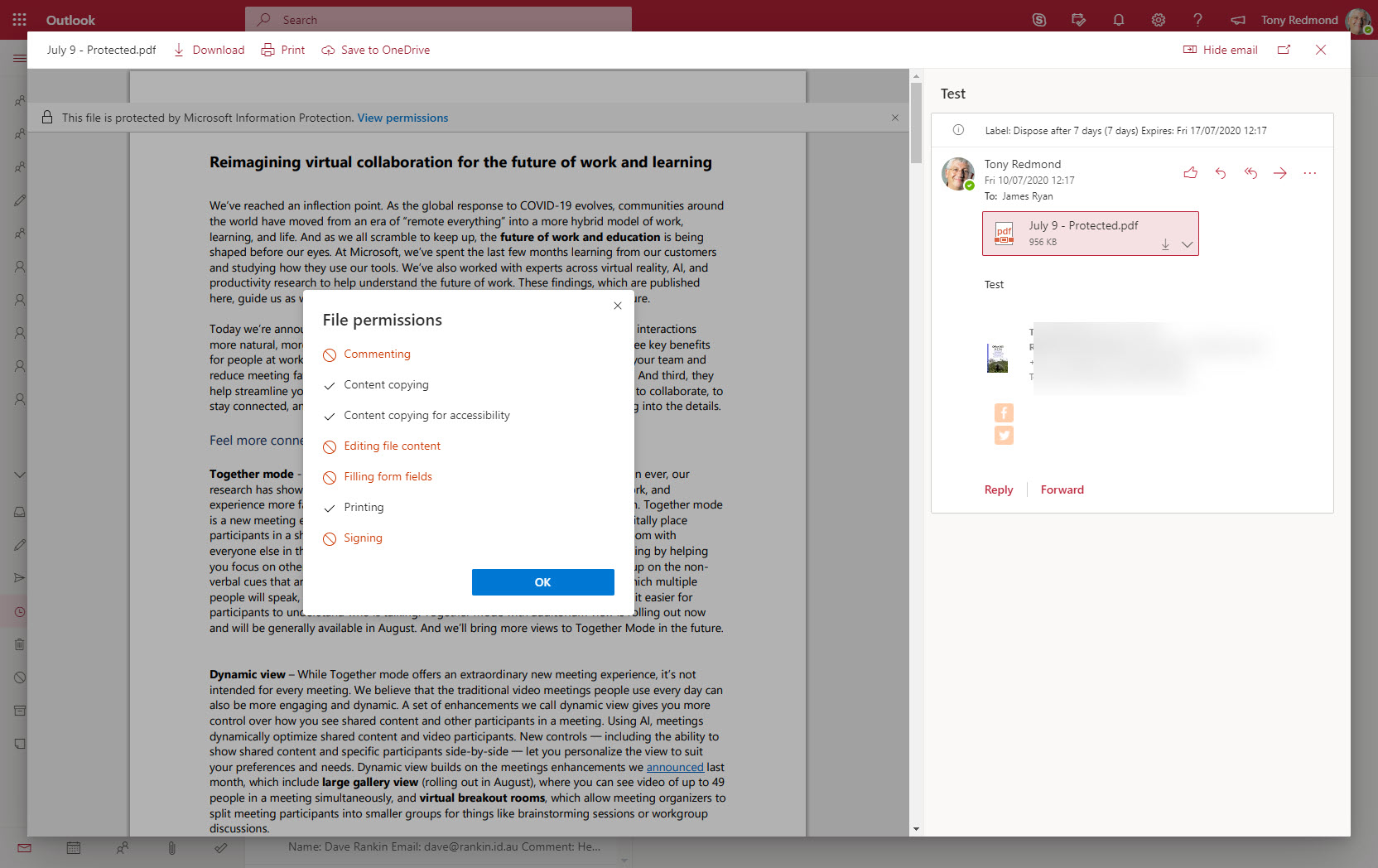
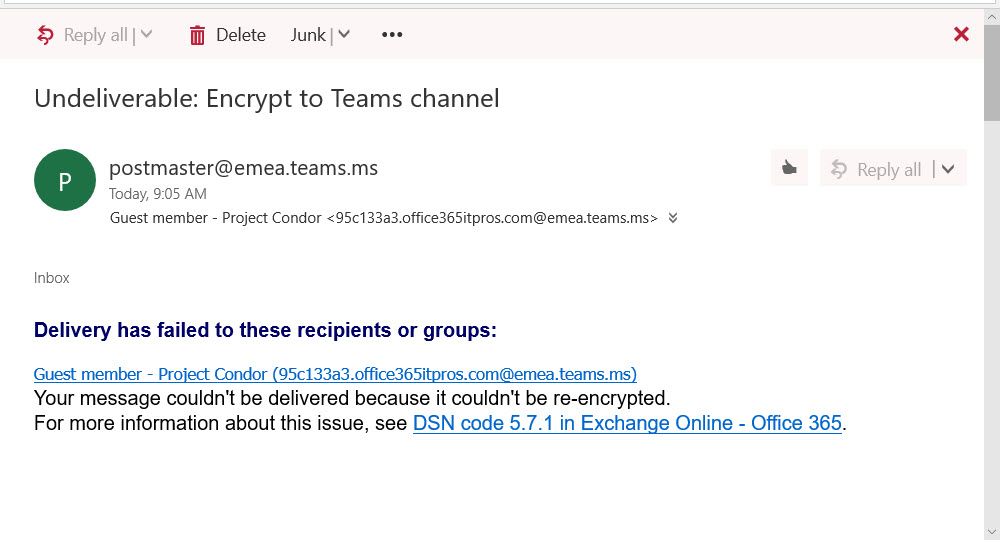
Encrypted email is becoming more common within Office 365. Things usually flow smoothly when sending protected messages to email recipients, but other Office 365 recipient types like Teams and Yammer might not be able to handle protected email.
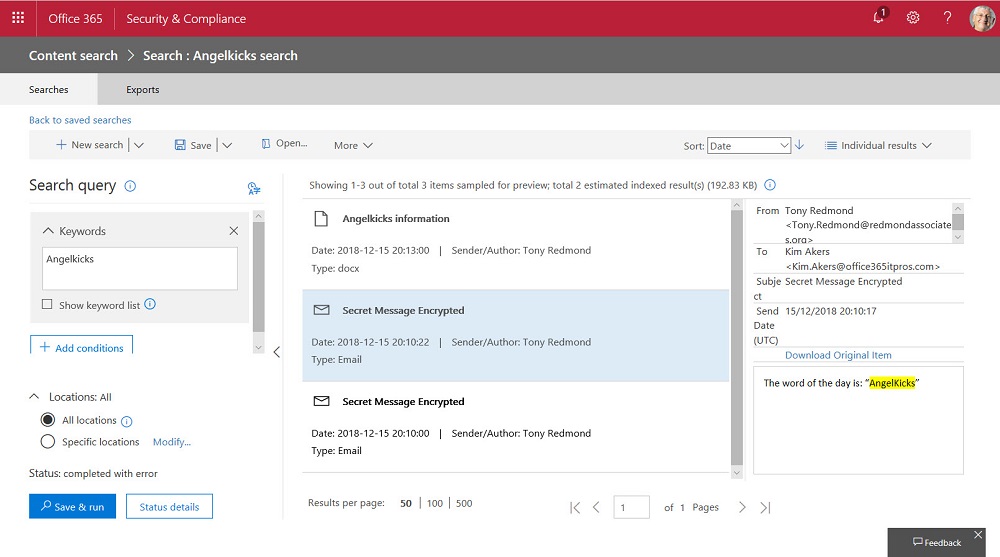
Making it easy to protect Office 365 content with encryption is great, but it has some downsides too. One of the obvious problems that we have is that encrypted documents in SharePoint and OneDrive for Business libraries can’t be found unless their metadata holds the search phrase.
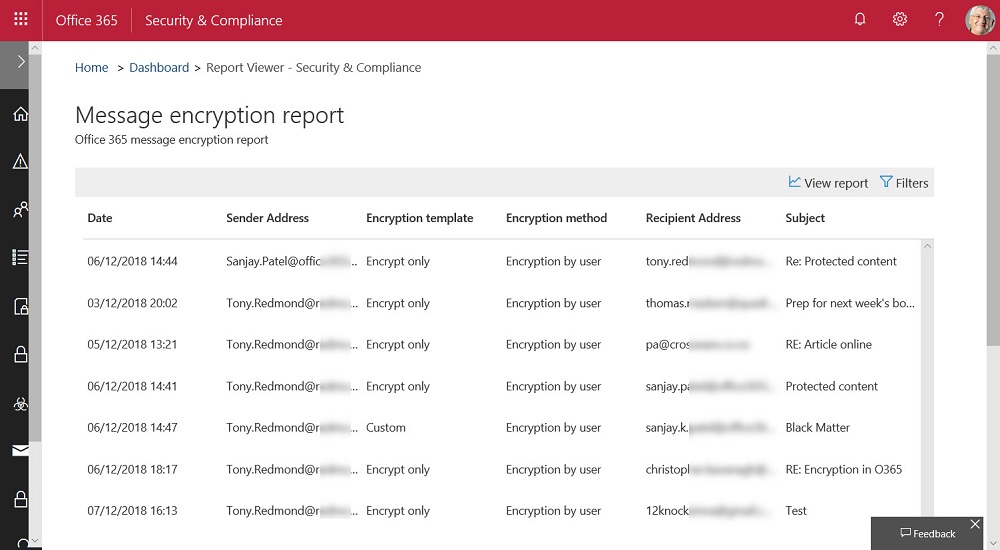
The Office 365 Security and Compliance Center includes a report to detail encrypted email. The report is in preview. It’s a nice insight into user activity, even if it has some glitches that need to be sorted out before it becomes generally available.
The latest version of the Azure Information Protection (AIP) client supports the ability to associate S/MIME protection with an AIP label. Although interesting, it’s a feature unlikely to be of much practical use to the majority of Office 365 tenants.
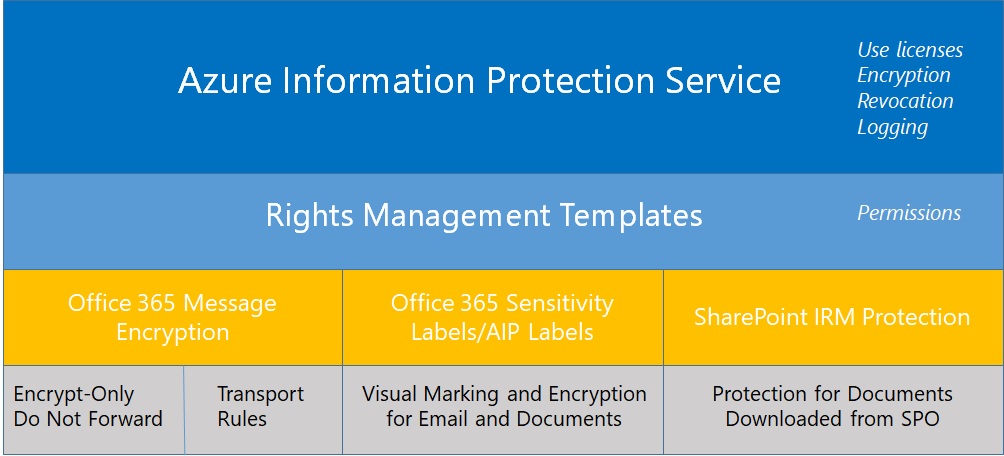
Rights management and encryption are likely to be a much more common Office 365 feature in the future. Sensitivity labels makes protection easy for users to apply through Office apps. The downside is that protection makes content harder to access for some Office 365 and ISV functionality.
The availability of Azure Information Protection and Office 365 sensitivity labels allow tenants to protect important and confidential files. That’s nice, but it’s even better when you know what files are protected. Here’s how to use PowerShell to create a report about those files.
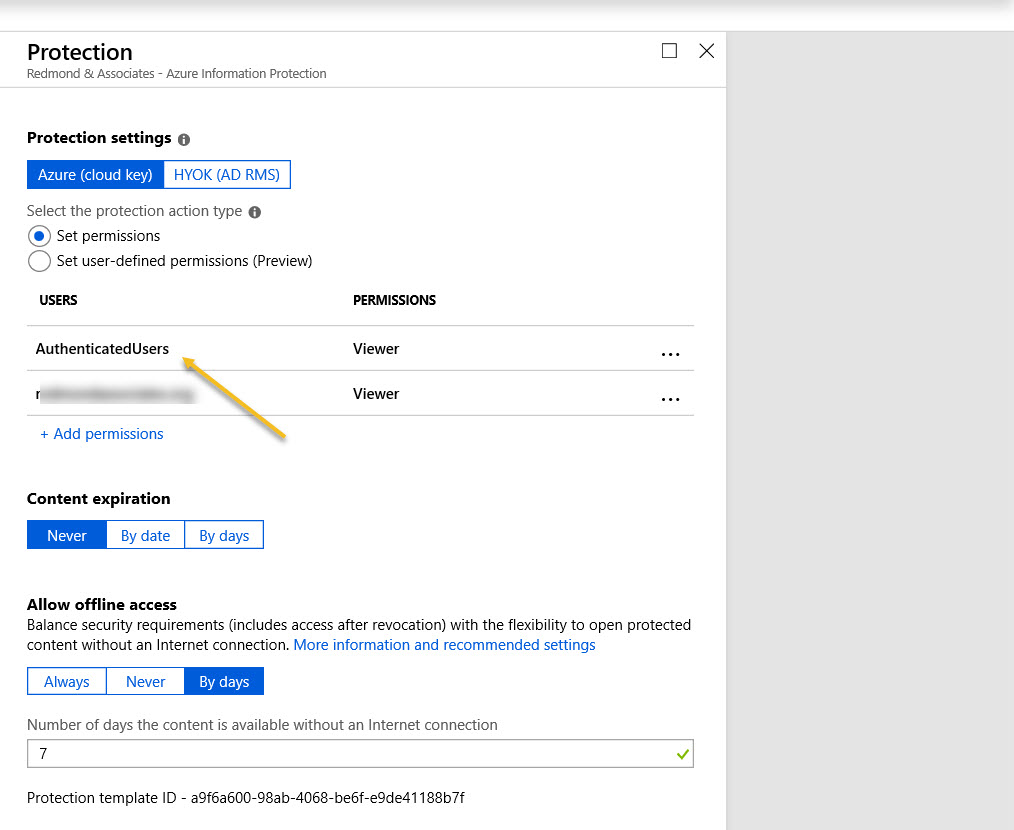
Azure Information Protection rights management templates now support the Any Authenticated Users permission to allow Office 365 users to share email and documents with anyone who can authenticate with Azure Active Directory or has an MSA account or uses a federated service.