The Maester tool is a community initiative to create a tool to help tenant administrators improve the security of their Entra ID tenants. It’s still in its early stages, but even so Maester shows signs that it will be a valuable asset for administrators who want to learn more about securing their tenant against possible external compromise.
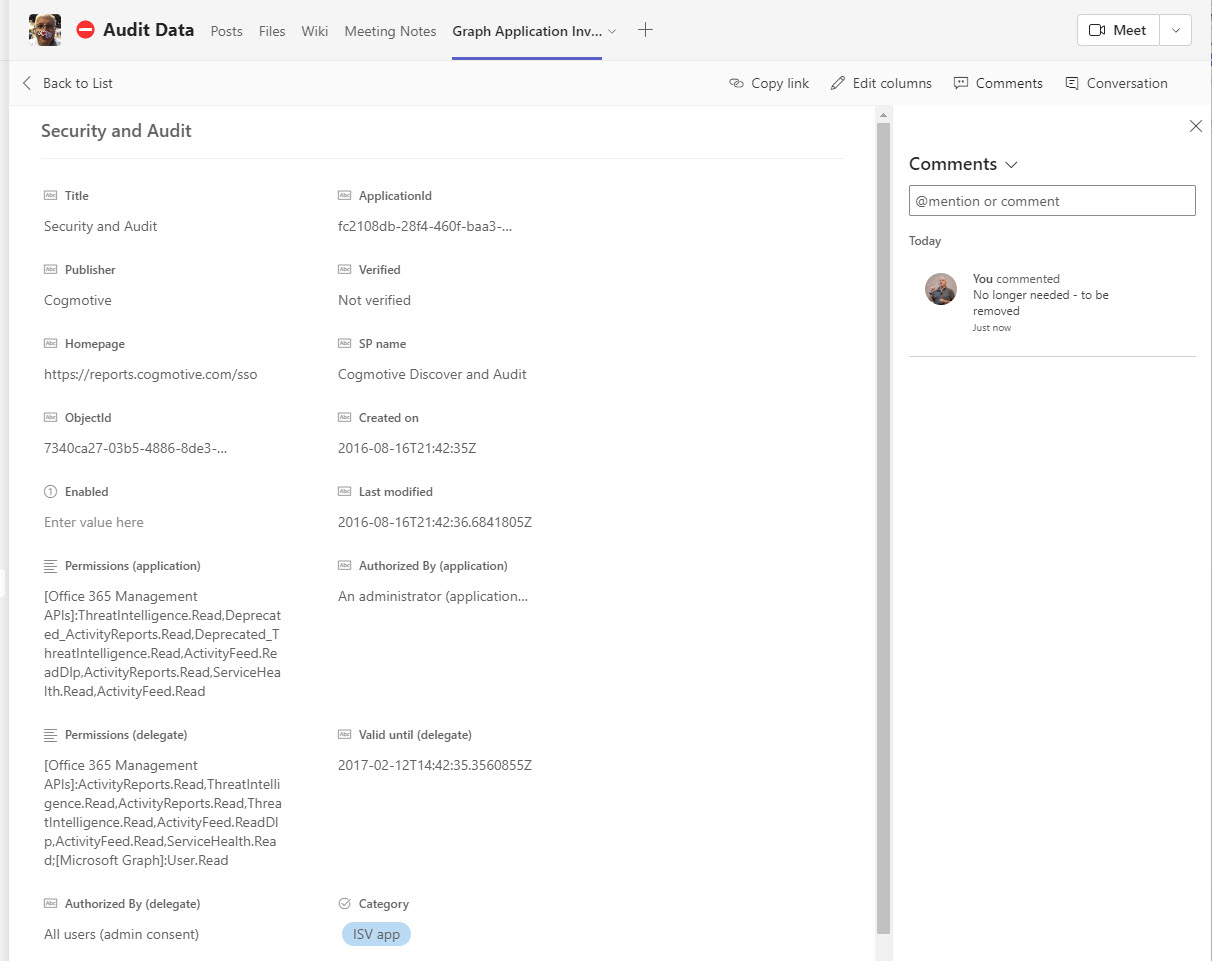
OAuth apps are a big part of the extensibility picture for Microsoft 365 tenants. As such, they are targeted by attackers as a good way to gain access to data. In a recent security blog, Microsoft recommends some steps to secure tenants. We’ve covered most of them in other articles, but it’s always good to pull the story together and rewrite a script to make it easier to report consent grants for apps.
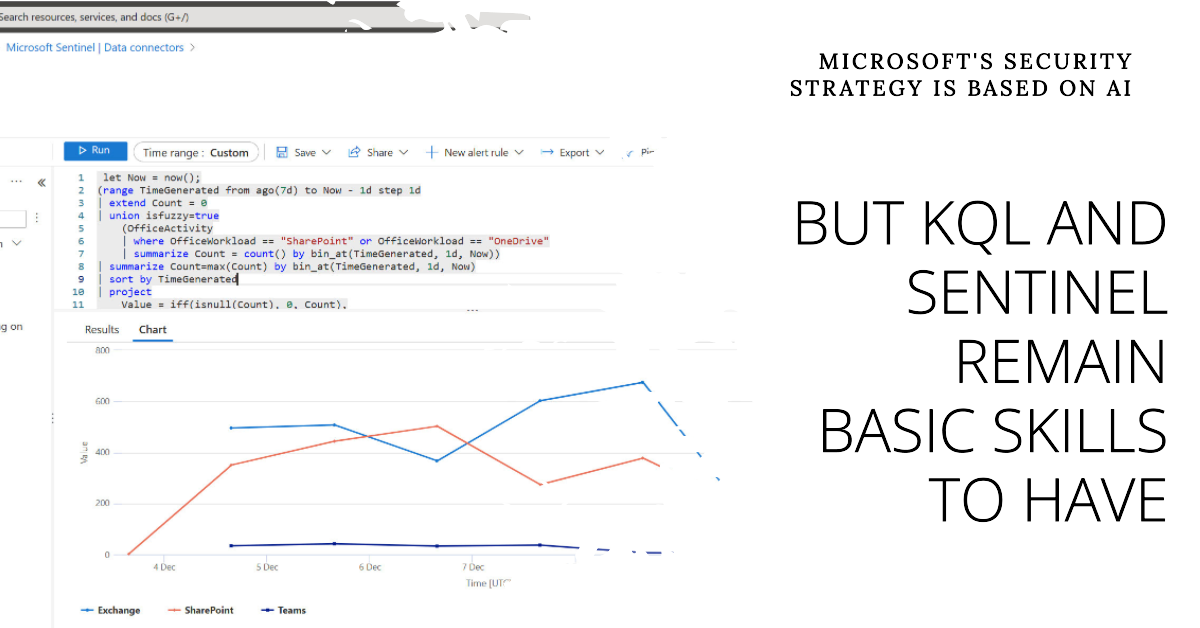
Microsoft’s security strategy is all about AI with Security Copilot leading the charge. Even in a world of AI tools, knowing how to use KQL and Sentinel is key. After all, AI might be able to identify potential problems and fix some of issues, but sorting out situations needs a certain level of basic knowledge to guide the AI to a successful conclusion.
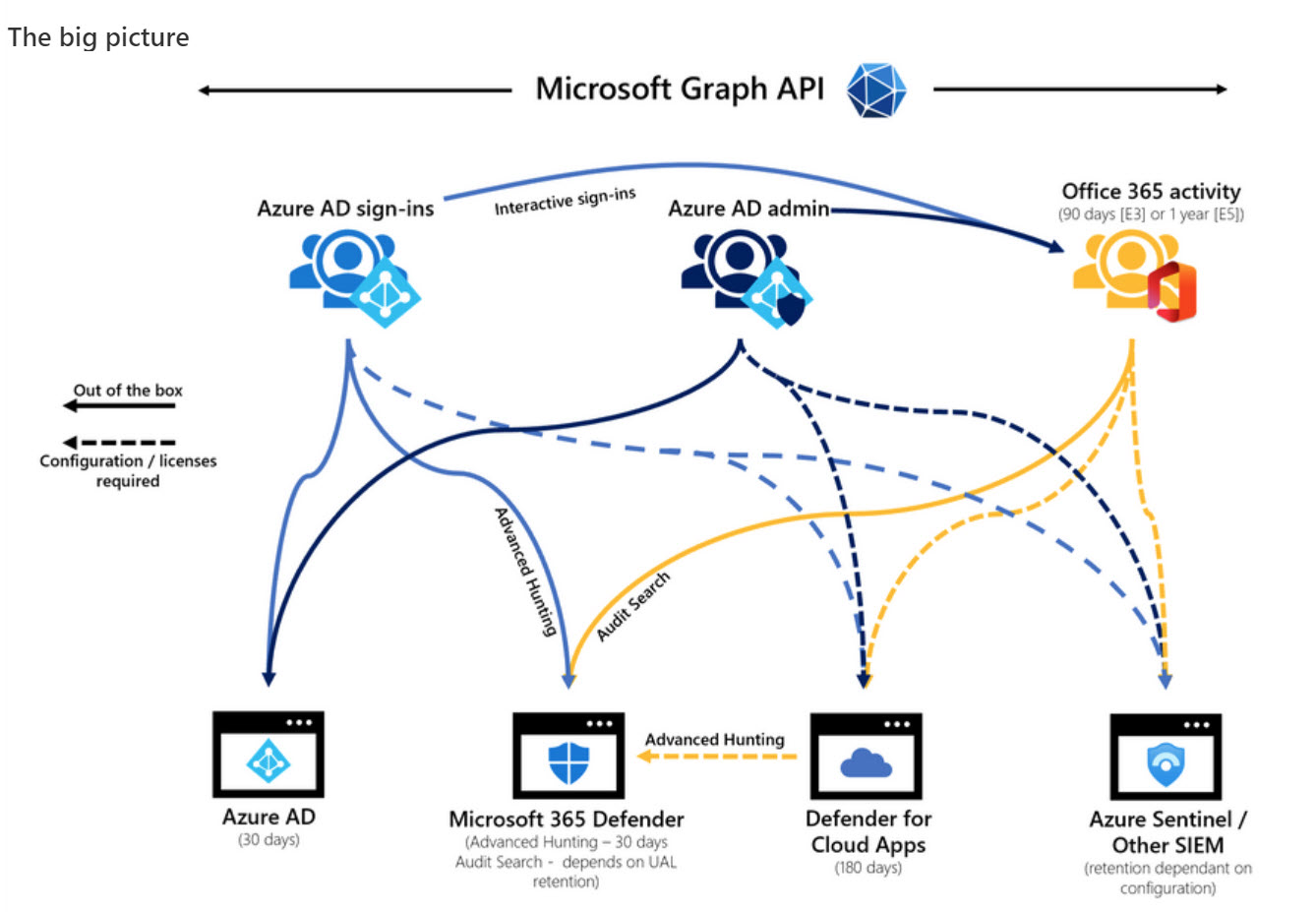
Microsoft DART (cybersecurity response team) published an interesting article about the essential sources of Microsoft 365 audit data used for forensic investigations. The Office 365 audit log gets a big mention and DART seems pretty impressed by the new audit log search that’s available in preview in the Purview Compliance portal. I’m not impressed by the performance of the new interface and will continue to use PowerShell. As it turns out, so will DART.
Some recent announcements will make it much easier to work with PDFs protected with sensitivity labels. Adobe is now bundling the MIP plug-in with the Acrobat installer and has plans to allow users to apply sensitivity labels within Acrobat. But the big news is the change in Office applications to generate protected PDFs when saving, exporting, or sharing protected documents, spreadsheets, and presentations.
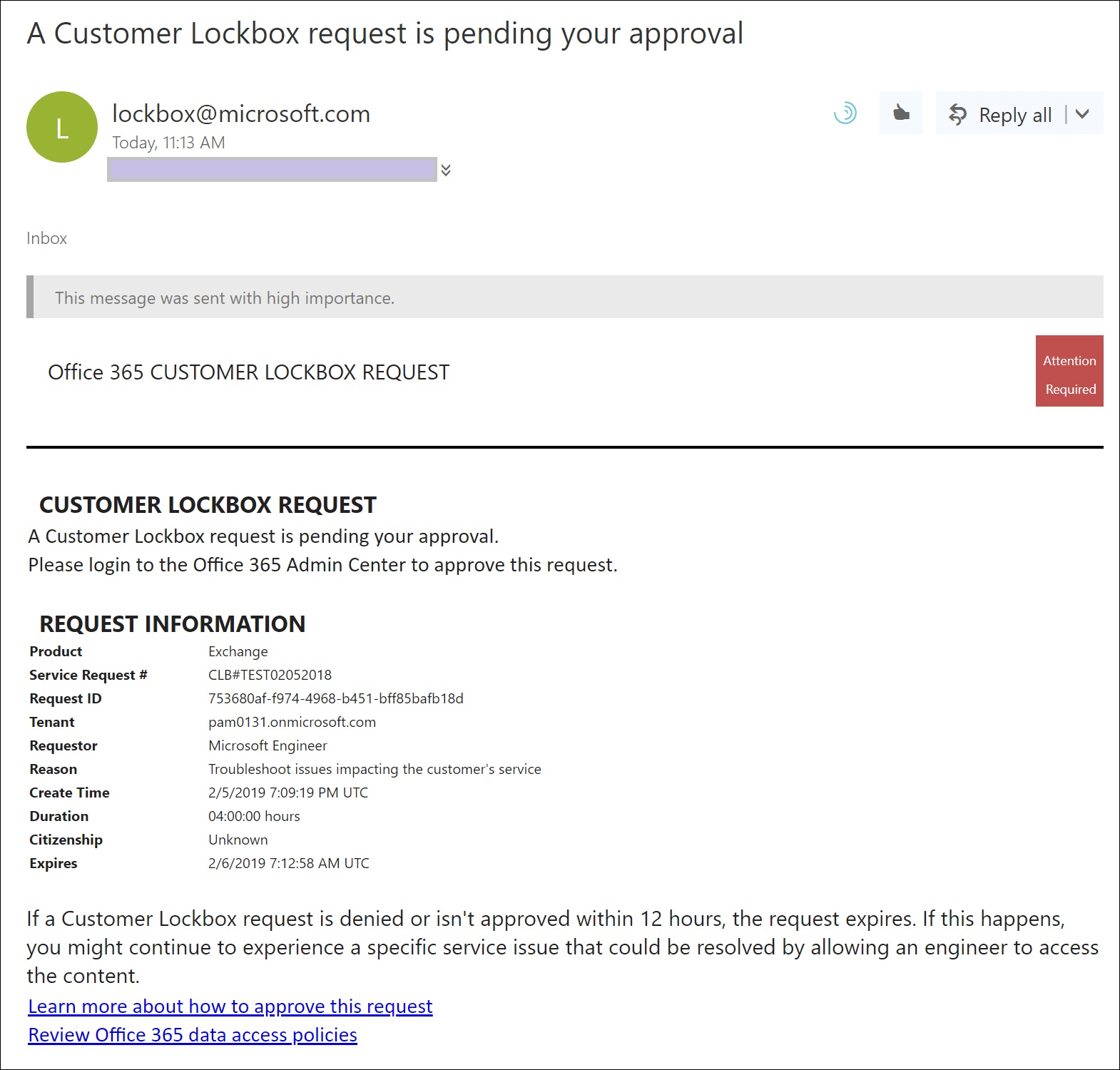
Microsoft is deploying an update to extend support for its customer lockbox feature to Teams user content, like chat or channel messages. Customer lockbox is part of the Office 365 and Microsoft 365 E5 products. It’s a useful control over the access Microsoft support personnel can get to user content, but it seems like this feature should be included in lower-cost products like Office 365 E3. Not that this will happen…
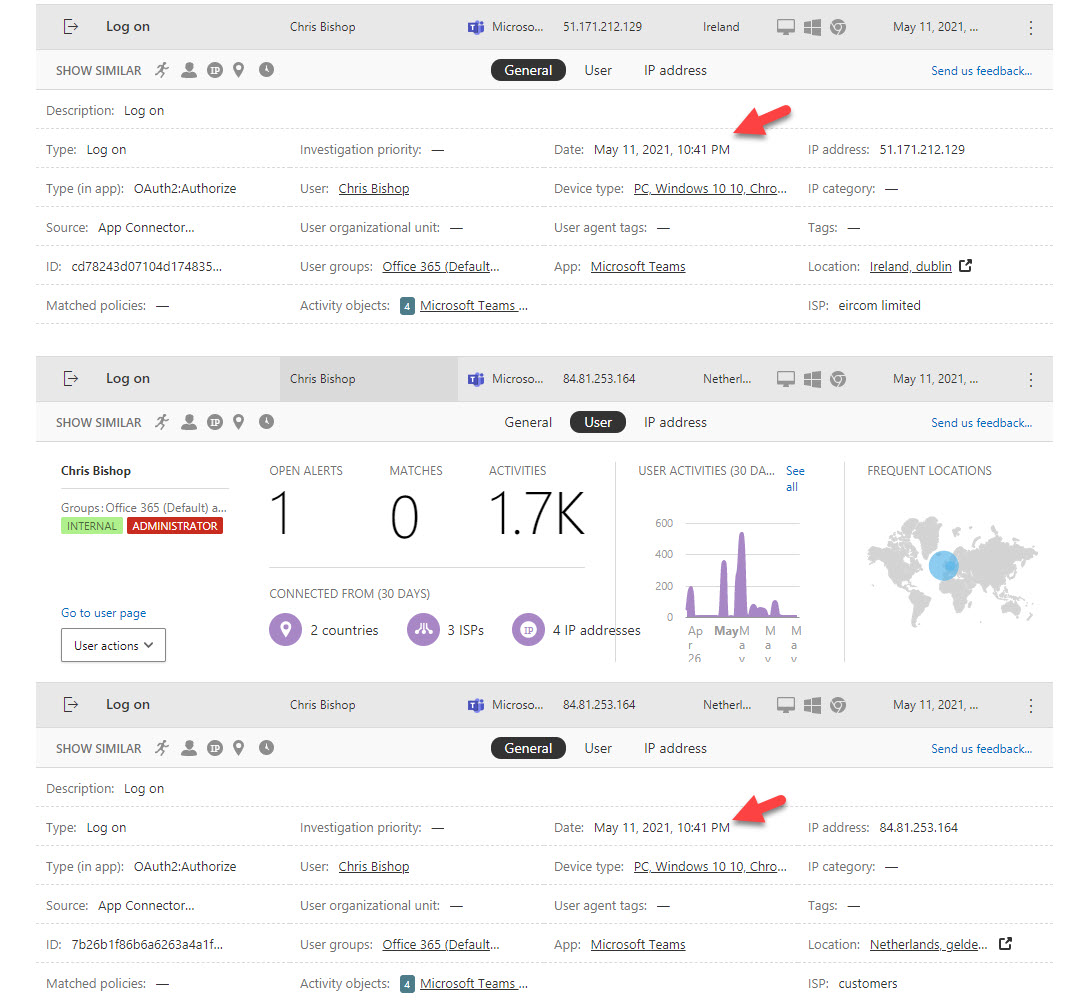
Service principal sign-in data from Entra ID is now accessible through a Microsoft Graph API. This means that you can analyze sign-in data to locate problem apps and remove old or unwanted service principals from your Microsoft 365 tenant. It’s time for spring cleaning!
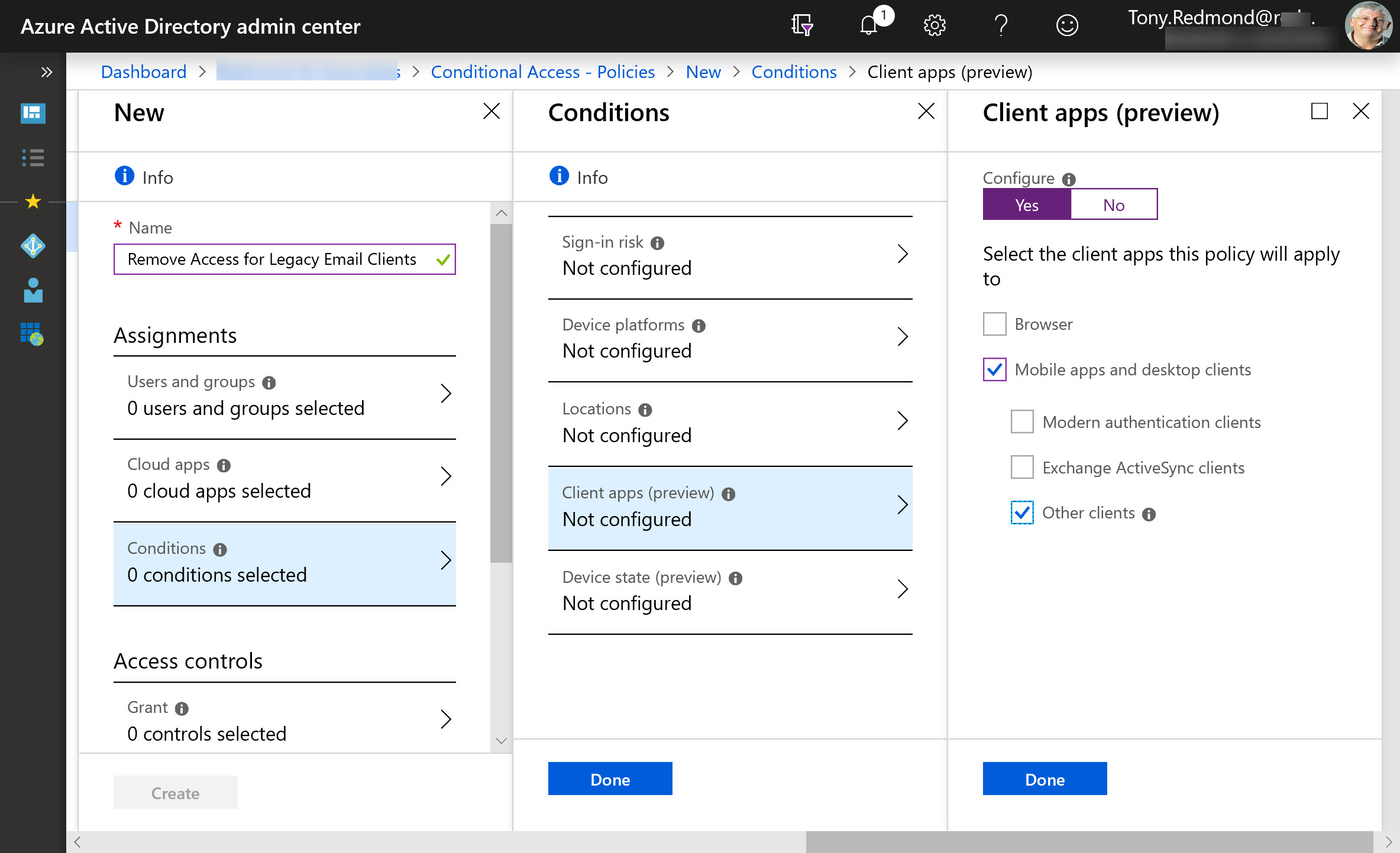
On January 10, Microsoft announced that the base Office 365 workloads support Continuous Access Evaluation (CAE) for critical Azure AD events like password changes or account deletions. Although you can take CAE even further with conditional access policies, giving Exchange Online, SharePoint Online, and Teams the ability to react to critical events in almost real-time is a very big thing indeed.
Office 365 Cloud App Security (OCAS) is very good at identifying potential problems for tenant administrators to investigate. But don’t think that it’s always right. Humans are often better at resolving issues than computers are, simply because we can use our wider knowledge of how applications work and the Office 365 datacenter network to understand what might be behind an alert. Humans might be slower than computers, but when it comes to resolving OCAS alerts, we’re always better.
Microsoft wants to remove basic authentication from Exchange Online connection protocols. But pressures have forced Microsoft into a new strategy and away from the mid-2021 date for deprecation of basic authentication for five protocols. Instead, Microsoft will disable basic authentication for protocols where it’s not used, include four addition protocols in its target set, and pause action for tenants where basic authentication is in active use. When they restart, Microsoft will give tenants 12 months’ notice that basic authentication will be blocked for a protocol. You can argue that Microsoft should have pressed ahead with their original plan, but would widespread disruption of service be worth the benefit gained from blocking vulnerable protocols? Balancing risk versus reward is often not easy.
The New Microsoft 365 Security for IT Pros eBook is now available from Gumroad.com. The book is modeled after Office 365 for IT Pros and covers the essential steps tenant administrators should take to secure and defend their organizations. Security is something that everyone involved in tenant administration needs to think about, so it’s good to have some solid advice from the pros.
Some doubt that Exchange Online will disable basic authentication for five email connection protocols in October 2020. The refrain is that it will be too hard for customers. Well, it might be hard to prepare to eliminate basic authentication, but if you don’t, your Office 365 tenant will be increasingly threatened by attacks that exploit known weaknesses.
SharePoint Online and OneDrive for Business support the ability to protected Anyone links with passwords. The idea is good and the feature works well, but some Office 365 tenants have problems with the idea of using Anyone links because, as the name implies, anyone who has the link can use it to open a document.
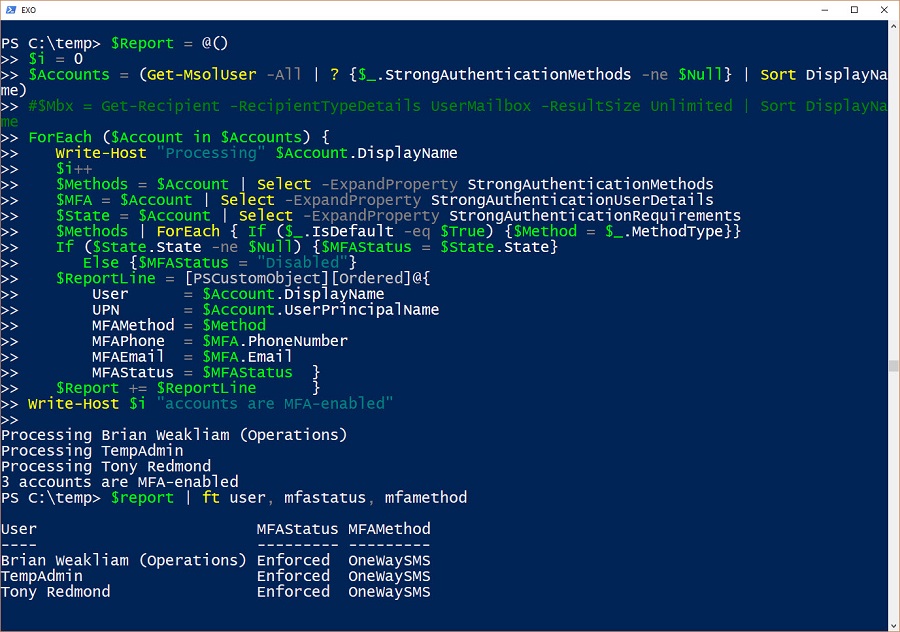
Microsoft makes a strong case that all Azure Active Directory accounts should be protected with multi-factor authentication (MFA). That’s a great aspiration, but the immediate priority is to check accounts holding administrative roles. This post explains how to use PowerShell to find and report those accounts.
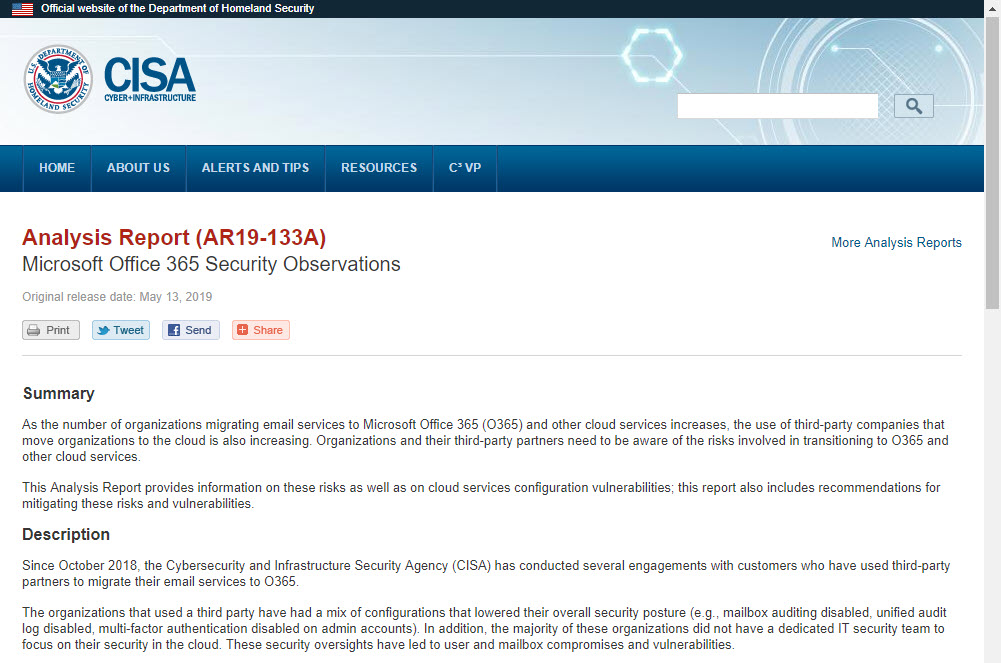
The CISA report titled “Microsoft Office 365 Security Observations” makes five recommendations to improve security of an Office 365 tenant. The recommendations are valid, but competent administrators won’t take long to implement them. In fact, the worst thing is that consultants brought in to help organizations didn’t seem to have much expertise in securing Office 365.
Microsoft has released the GA version of the Azure Information Protection client, which reads information about Office 365 sensitivity labels and policies from the Security and Compliance Center. It’s one more step along the path to making it easy for Office 365 tenants to protect their data. Work still has to be done, but at least we can see light at the end of the encryption tunnel.
The Microsoft 365 Security and Microsoft 365 Compliance Centers are now generally available. The new consoles will eventually replace the Office 365 Security and Compliance Center (SCC) but some work is needed to fill out their functionality and make the switchover possible. In the meantime, the Office 365 for IT Pros eBook writing team will stay focused on the SCC. And when the time’s right, we’ll switchover.
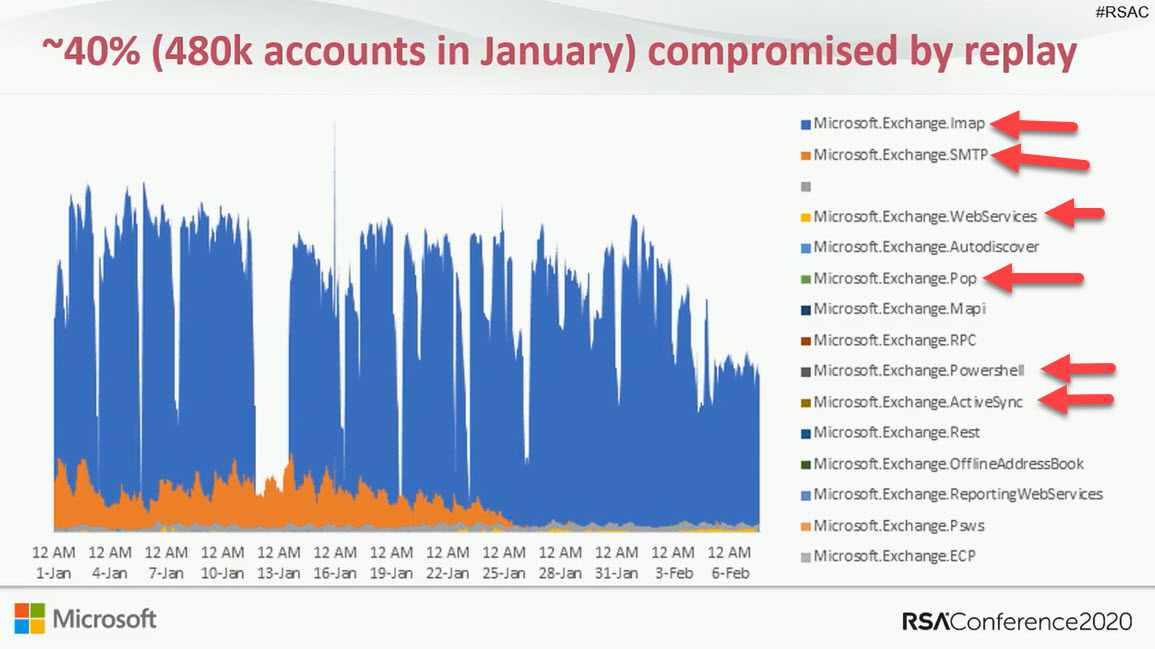
Exchange Online protocol authentication policies control what protocols a user can connect to mailboxes with, but it would be much better if we didn’t have to worry about some old and insecure protocols. Azure Active Directory gives Office 365 tenants the chance to clamp down on IMAP4 and POP3 connections and close off some of the holes that attackers try to exploit. Microsoft says that this can lead to a 67% reduction in account compromises, so that’s a good thing.
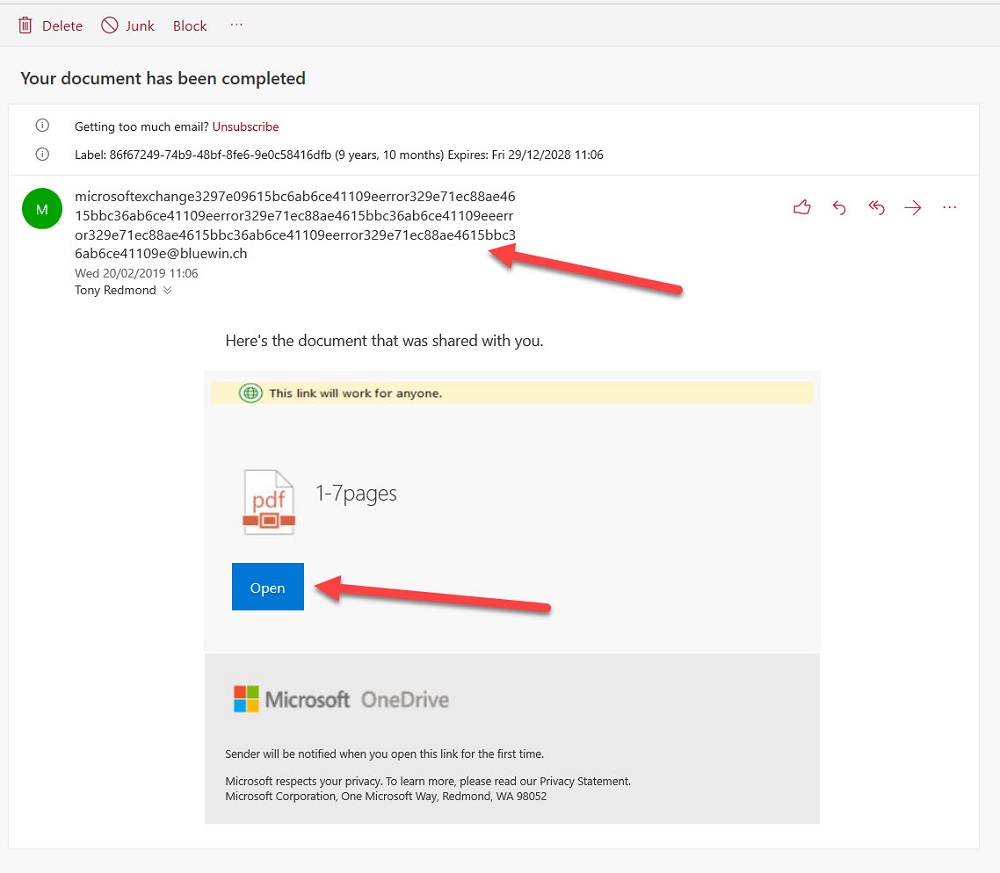
Phishing attacks through email happen all the time. A new relatively crude one arrived today. It’s easy for the trained eye to detect phishing, but do your Office 365 admins know how to use the tools available in Exchange Online Protection to suppress malware, and do your users know the signs of bad email? In this case, it’s an invitation to click to get to a PDF document to bring you to digitaloceanspaces.com. Some interesting things might happen afterwards, but I really don’t want to find out what occurs when I click the link.
Office 365 tenants can use Exchange transport rules to apply autosignatures to outbound email, including messages protected with encryption. You can even include some properties of the sender extracted from Azure Active Directory, and you can add an exception so that the autosignature isn’t applied to replies.
Exchange Online now captures session identifiers in its mailbox and admin audit records that are ingested in the Office 365 audit log. That’s interesting and useful, but how do you access and interpret this information on a practical level?
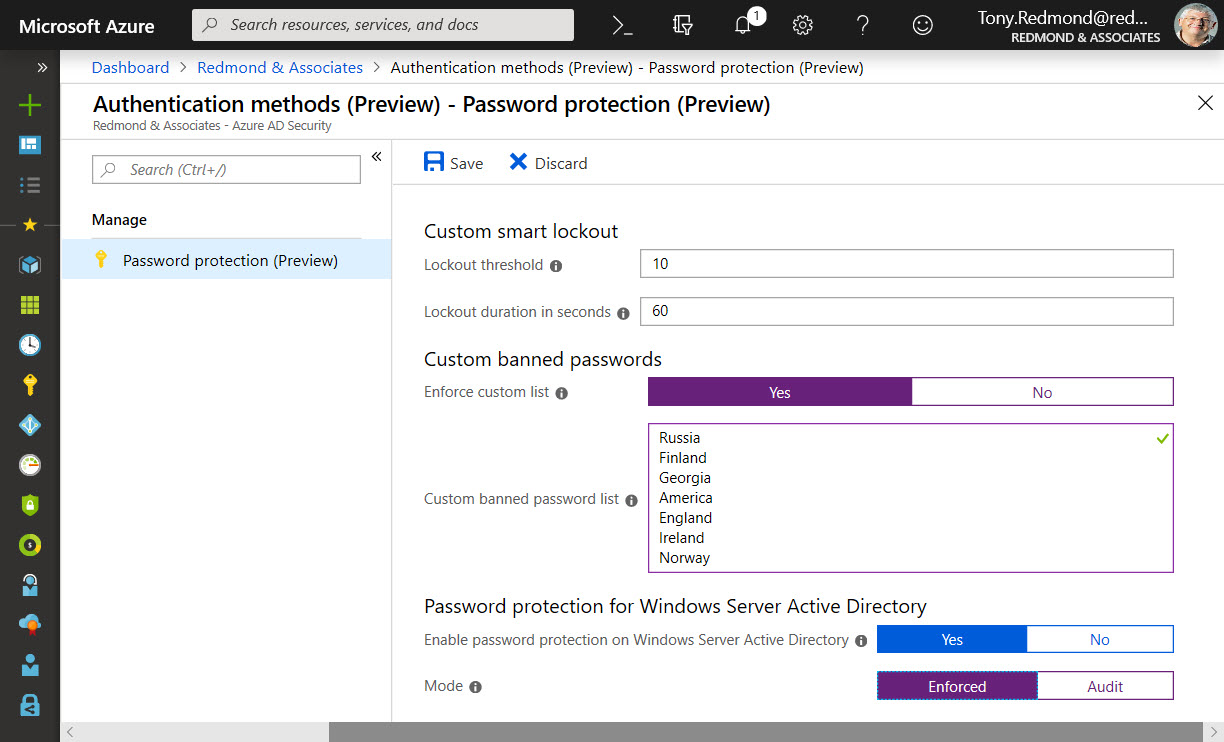
Making sure that Office 365 user (and administrator) accounts have good passwords is a never-ending task. A new preview feature in Azure Active Directory helps by ensuring that users can’t include common words specific to the organization (like its name) in a password. It’s another piece in the puzzle to frustrate potential attackers.
The latest version of the Azure Information Protection (AIP) client supports the ability to associate S/MIME protection with an AIP label. Although interesting, it’s a feature unlikely to be of much practical use to the majority of Office 365 tenants.
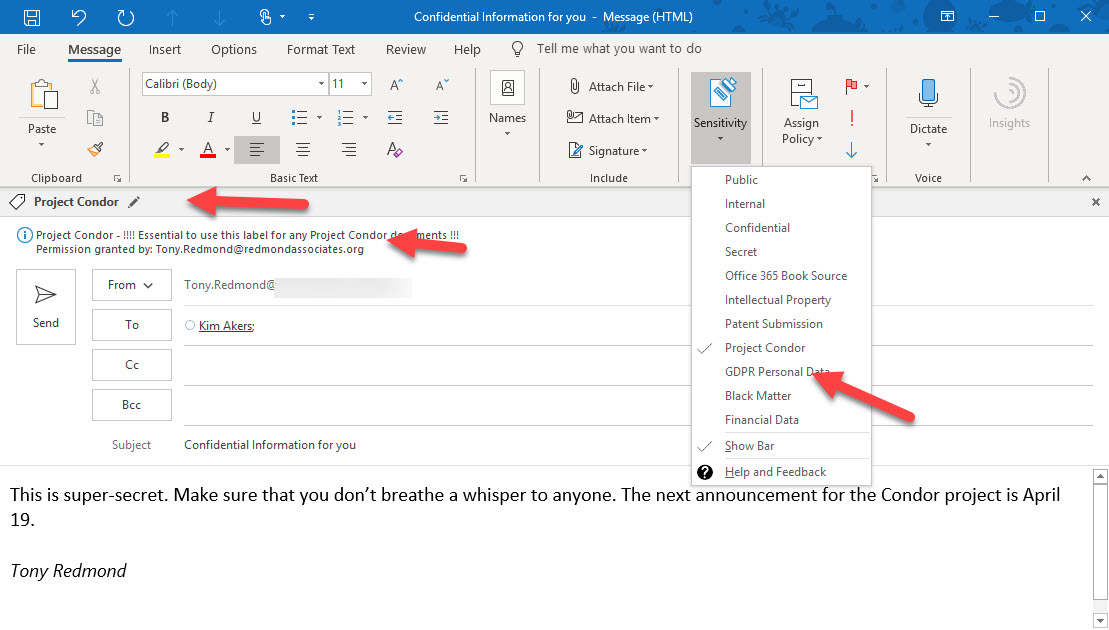
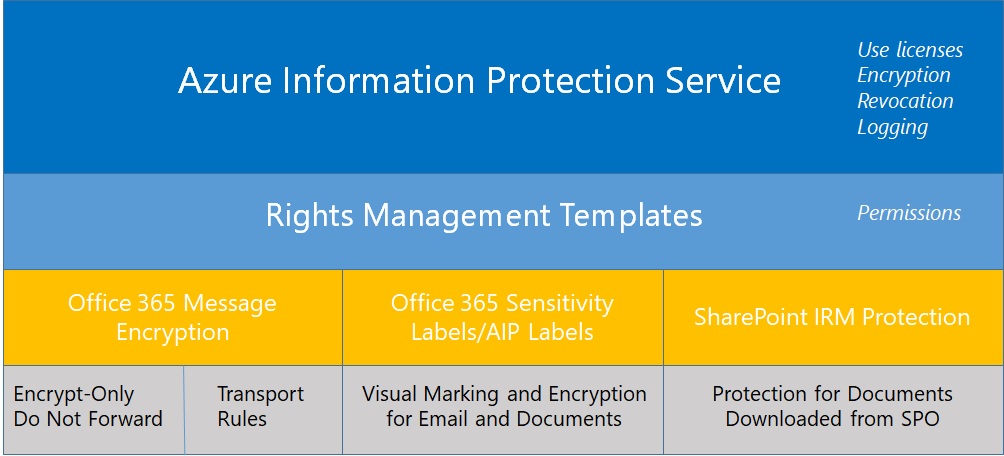
Rights management and encryption are likely to be a much more common Office 365 feature in the future. Sensitivity labels makes protection easy for users to apply through Office apps. The downside is that protection makes content harder to access for some Office 365 and ISV functionality.
When a problem arises, it’s good to know what user accounts are affected. In the case of the recent MFA outage, the need existed to report the list of accounts that were MFA-enabled. Here’s how to do the job with PowerShell.
Microsoft’s Azure-based multi-factor authentication (MFA) service experienced a service outage on November 19. Does this mean that we should disable MFA for accounts?
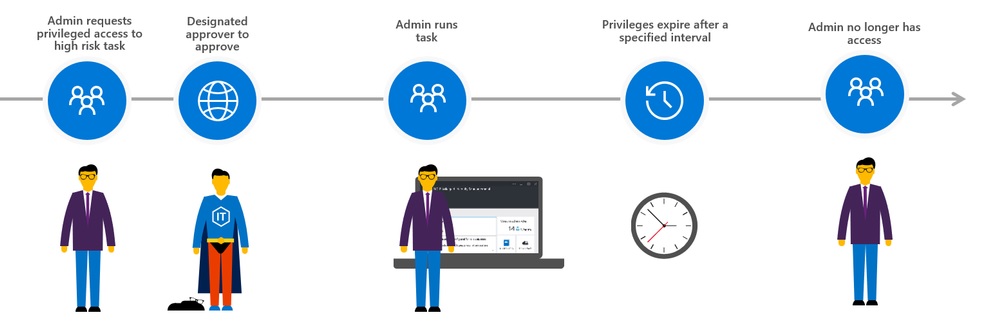
Microsoft has launched Privileged Access Management (PAM) for Office 365. The name’s incorrect because PAM only works for Exchange Online right now. PAM is based on RBAC, which is good, but is the implementation too Exchange-centric?
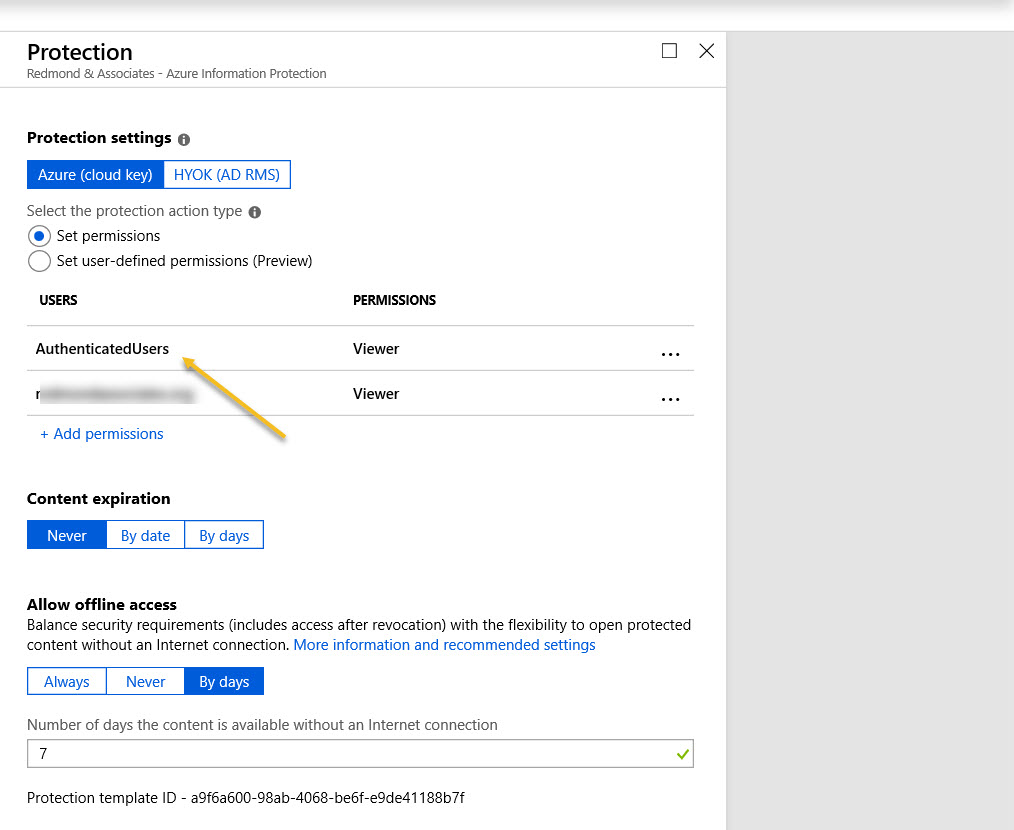
Azure Information Protection rights management templates now support the Any Authenticated Users permission to allow Office 365 users to share email and documents with anyone who can authenticate with Azure Active Directory or has an MSA account or uses a federated service.
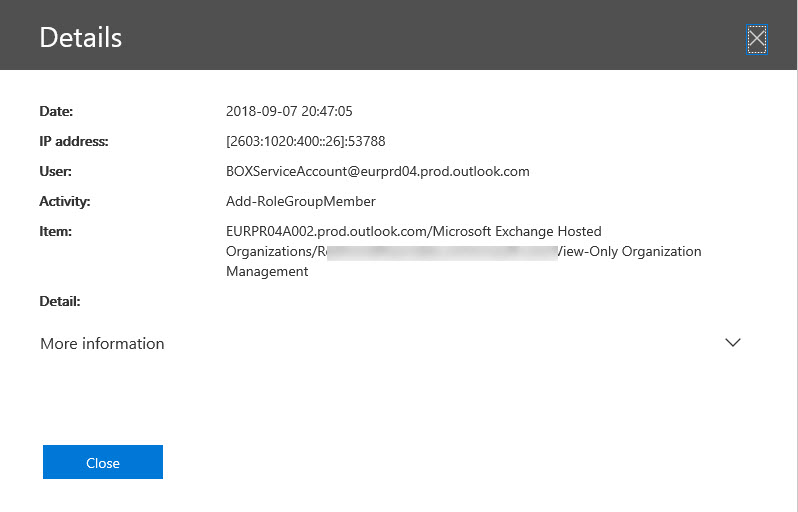
Records featuring an account called BOXServiceAccount appear in the Office 365 audit log. Not much information is available about the account, but it’s all OK because it’s used to assign administrative roles to Office 365 accounts.
Microsoft has released a new setting in the tenant Information Rights Management (IRM) configuration to control if attachments of messages encrypted with the Encrypt Only feature (in OWA and Outlook) are decrypted when downloaded. In fact, two settings are available. One for people with Azure AD accounts, and one for those without.
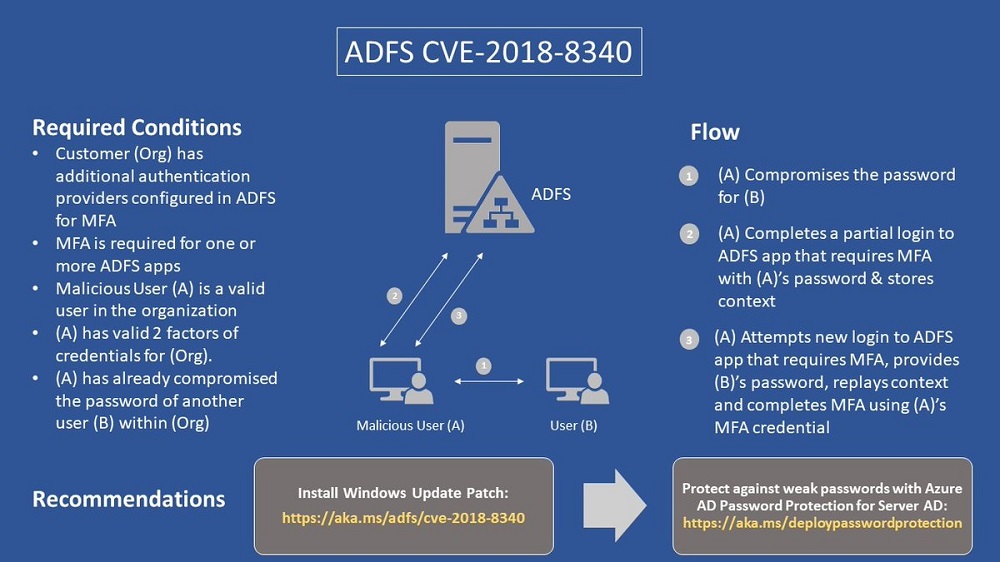
Microsoft has issued patch CVE-2018-8340 to fix a problem with Active Directory Federation Services. You should download and install this patch now.
The security company Avanan says that 10% of Office 365 users are affected by “PhishPoint.” That estimate seems pretty high to me.