Some folks wonder why they can’t use documents shared with them using company-wide links with Copilot for Microsoft 365. As it turns out, the answer is simple. People must redeem a sharing link before SharePoint validates their access to a shared file. Copilot cannot use a document unless it has access to it. All of which brings up the point if it’s a good idea to use company-wide sharing links.
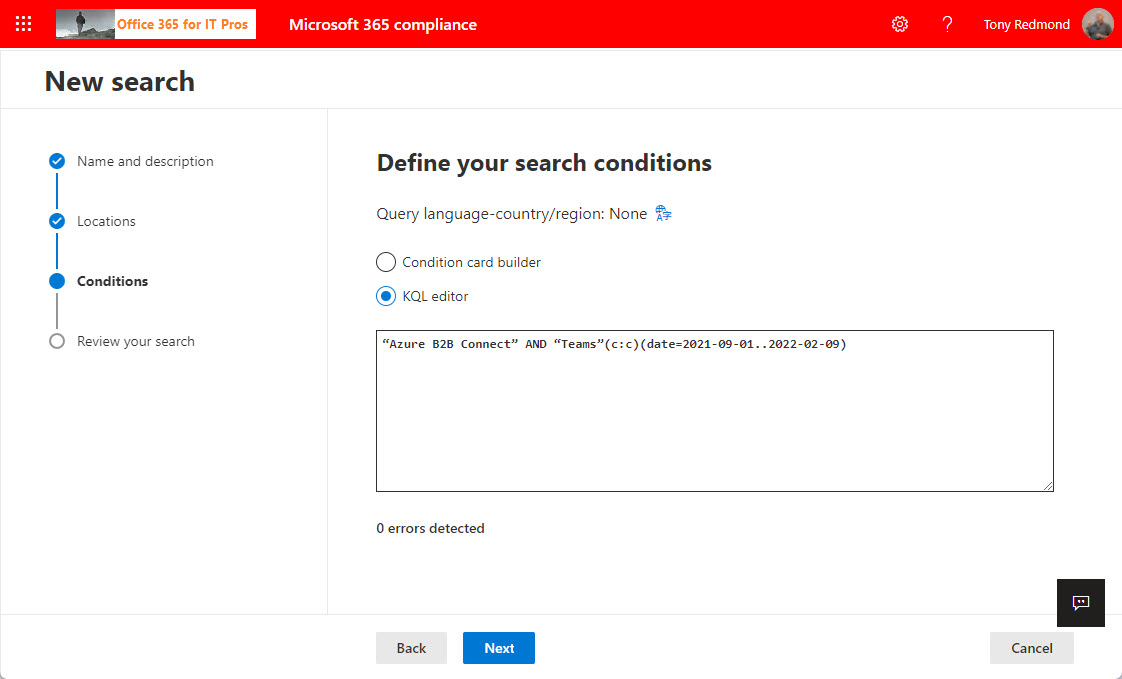
The KQL editor is a relatively new feature in Microsoft 365 that makes it easier to compose queries to find email and documents in content searches, core eDiscovery, and advanced eDiscovery. Although it’s not perfect, the KQL editor helps compliance managers to perfect queries and resolve syntax errors. Human intelligence is still needed to make sure that everything works!
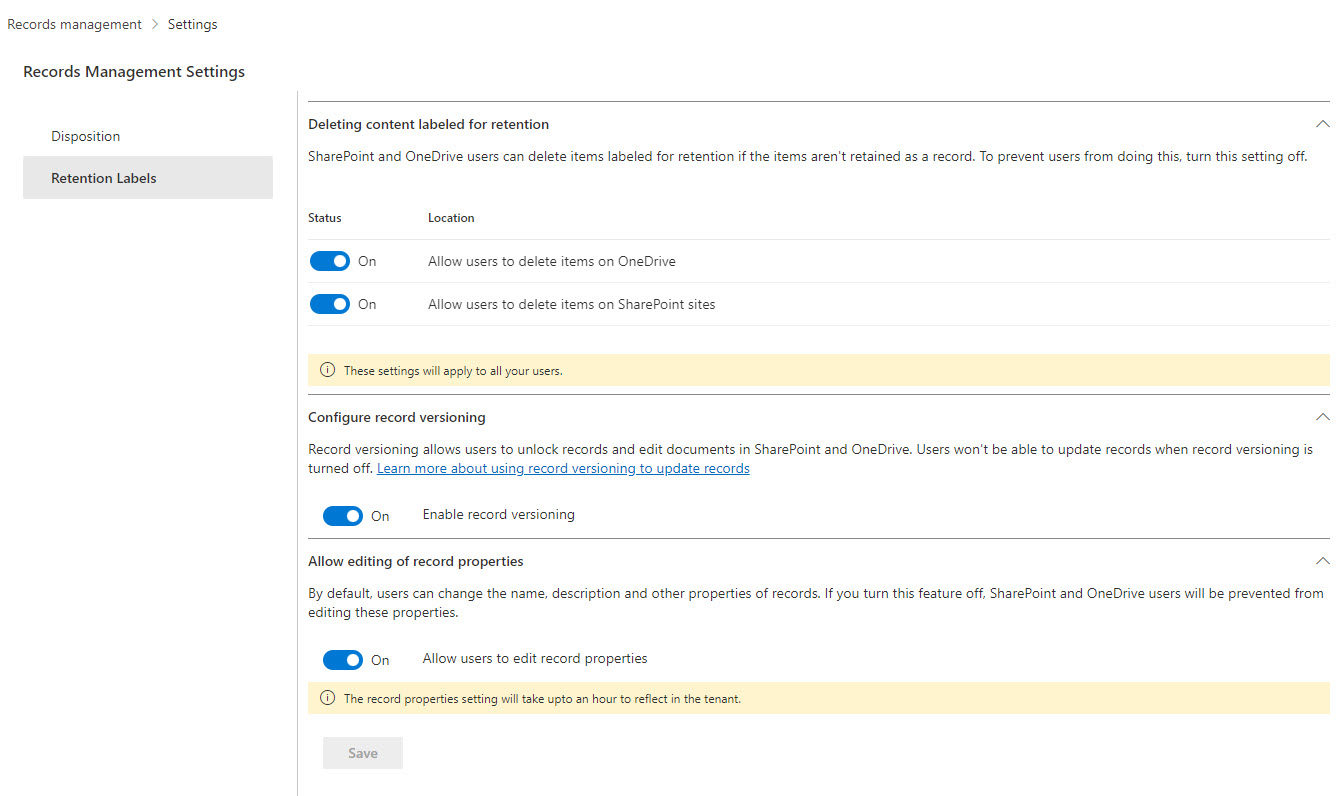
The Records management solution in the Microsoft 365 compliance center has some important controls for retention labels. Two new controls allow organizations to decide if they will allow users to unlock items assigned a record retention label. If they can’t, they won’t be able to update document contents or change an item’s metadata. This won’t suit all organizations, but it will make those which want locked down records management very happy indeed.
Microsoft 365 retention policies allow organizations to keep or remove content from workloads like Exchange Online and SharePoint Online. You can apply filters in retention policies, but Microsoft only supports this capability auto-label retention policies. You can go ahead and update a standard retention policy to add a content filter with PowerShell and the policy will work. The question is, how long will it work for before Microsoft changes something on the backend to stop the policy working?
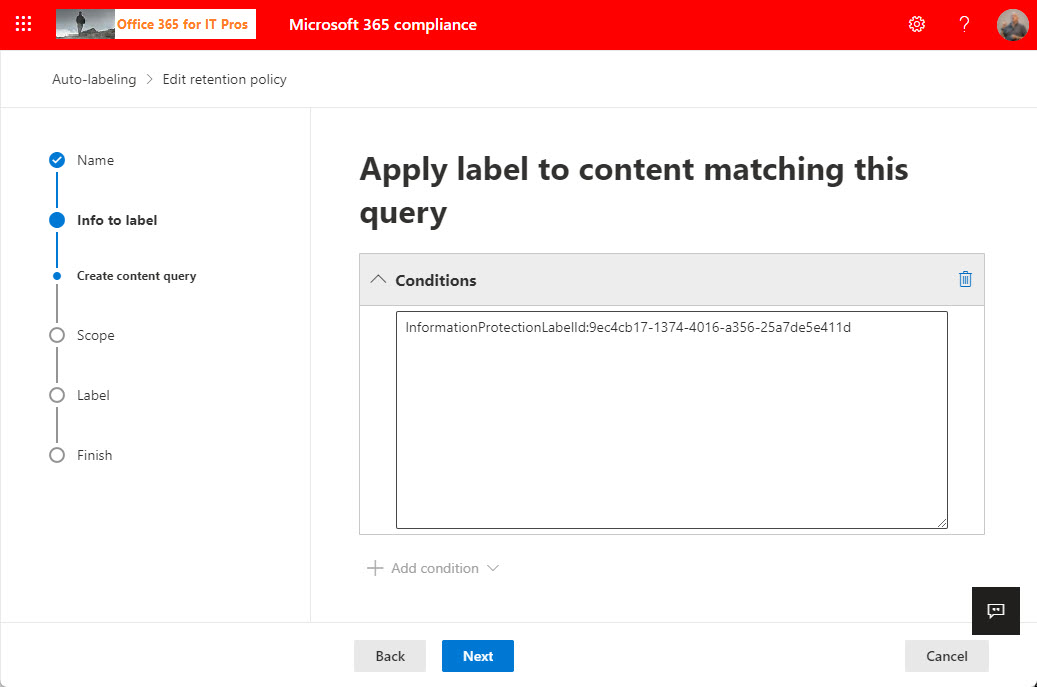
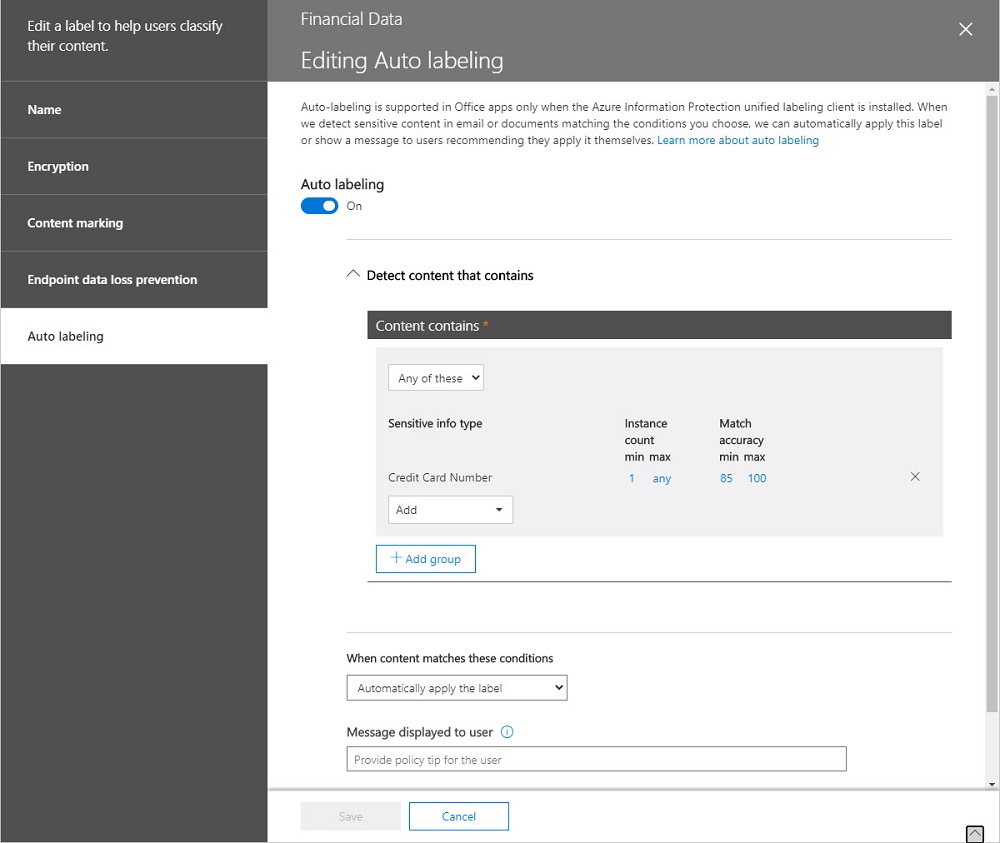
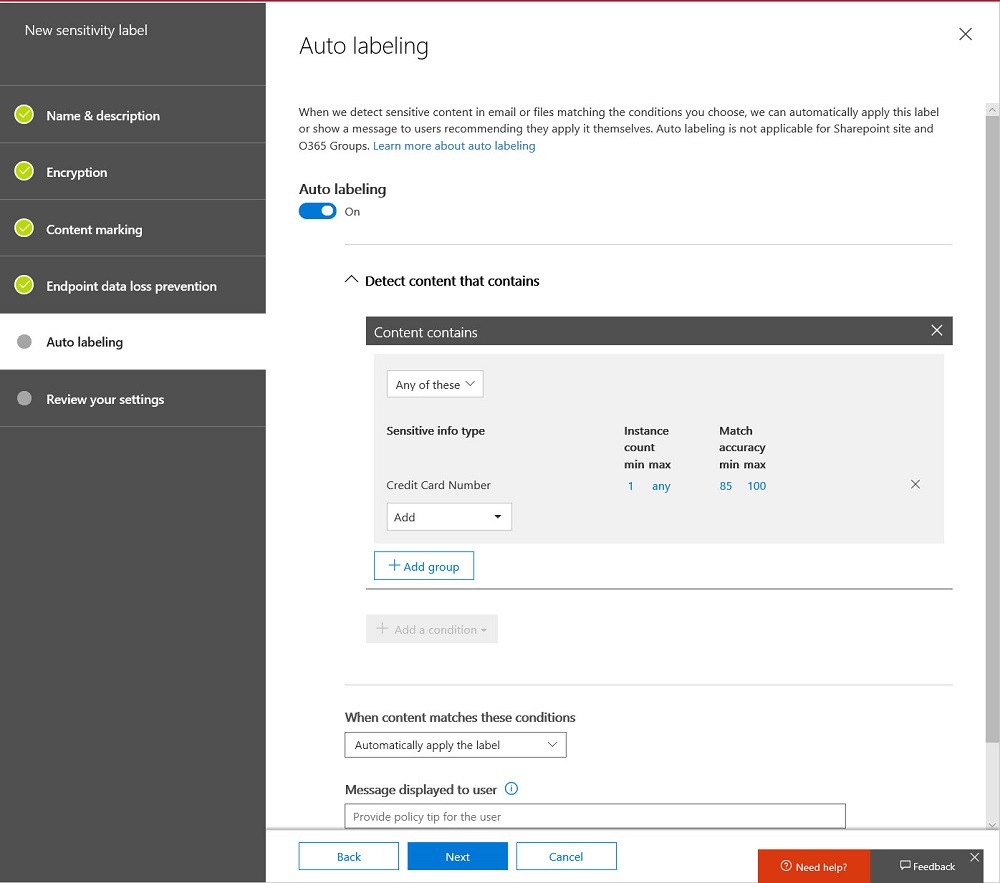
Auto-label retention policies find items in Microsoft 365 locations and apply retention labels to those items. In this article, we explain the steps involved in creating an auto-label retention policy to look for items with sensitivity labels and apply retention labels to those items.
Microsoft plans to surface recommendations to use communications compliance policies as part of its DLP workflow. That sounds acceptable, but it’s the second example of how Microsoft pushes high-priced premium features to Office 365 tenants through DLP. Apart from the undesirability of pushing features to customers through software, communications compliance is not something that you implement on a whim, so why does Microsoft think this is a good idea?
Microsoft has moved retention processing for SharePoint Online, OneDrive for Business, Teams, and Yammer from the Managed Folder Assistant to a new retention assistant. (background processing job). It’s part of an effort to use workload-agnostic processing whenever possible to perform retention actions across Microsoft 365.
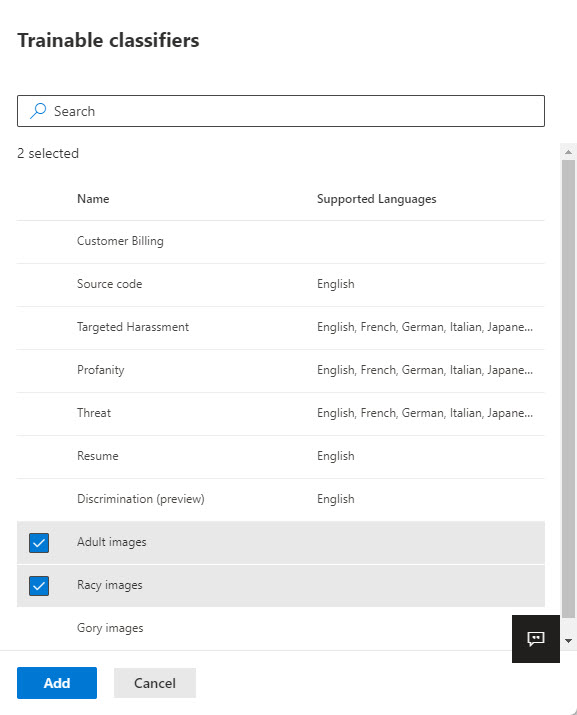
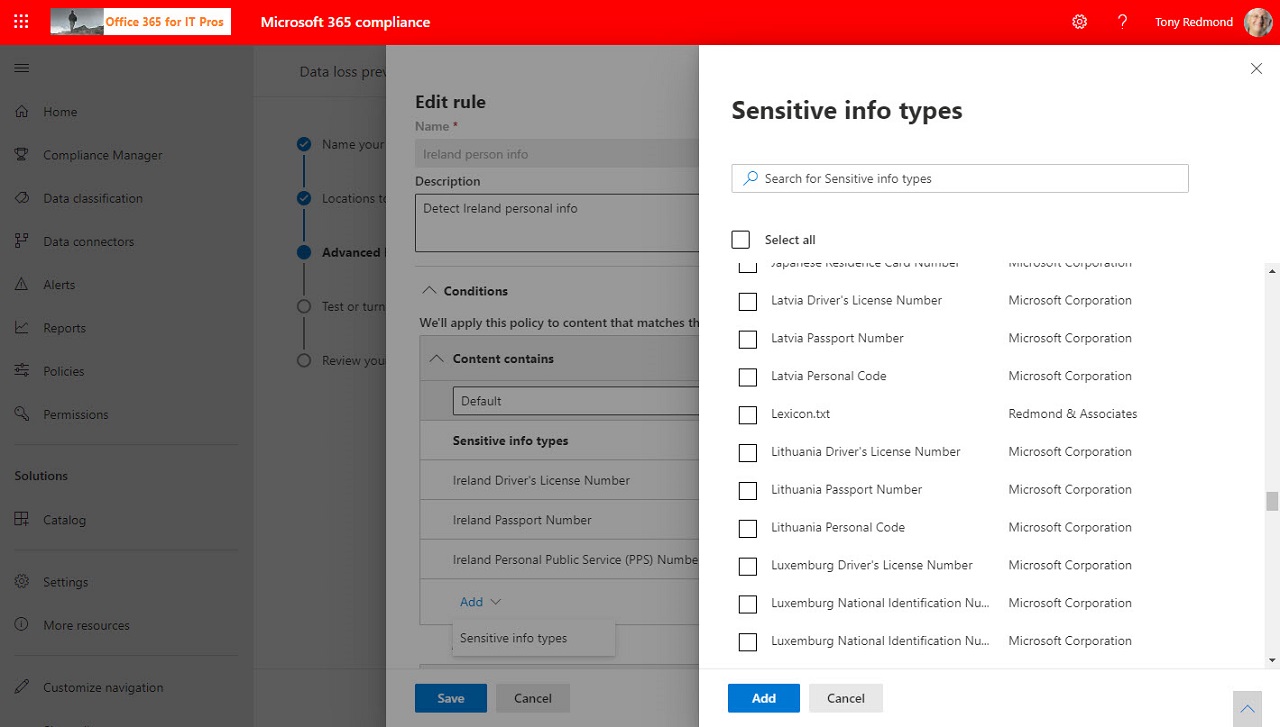
Microsoft has released a set of new sensitive information types, used to locate sensitive data by Microsoft 365 DLP policies. Many are country-specific versions of previous generic types (like passports or identity cards). The recommendation is to consider upgrading DLP policies to use the new types to get better (more accurate) matching.
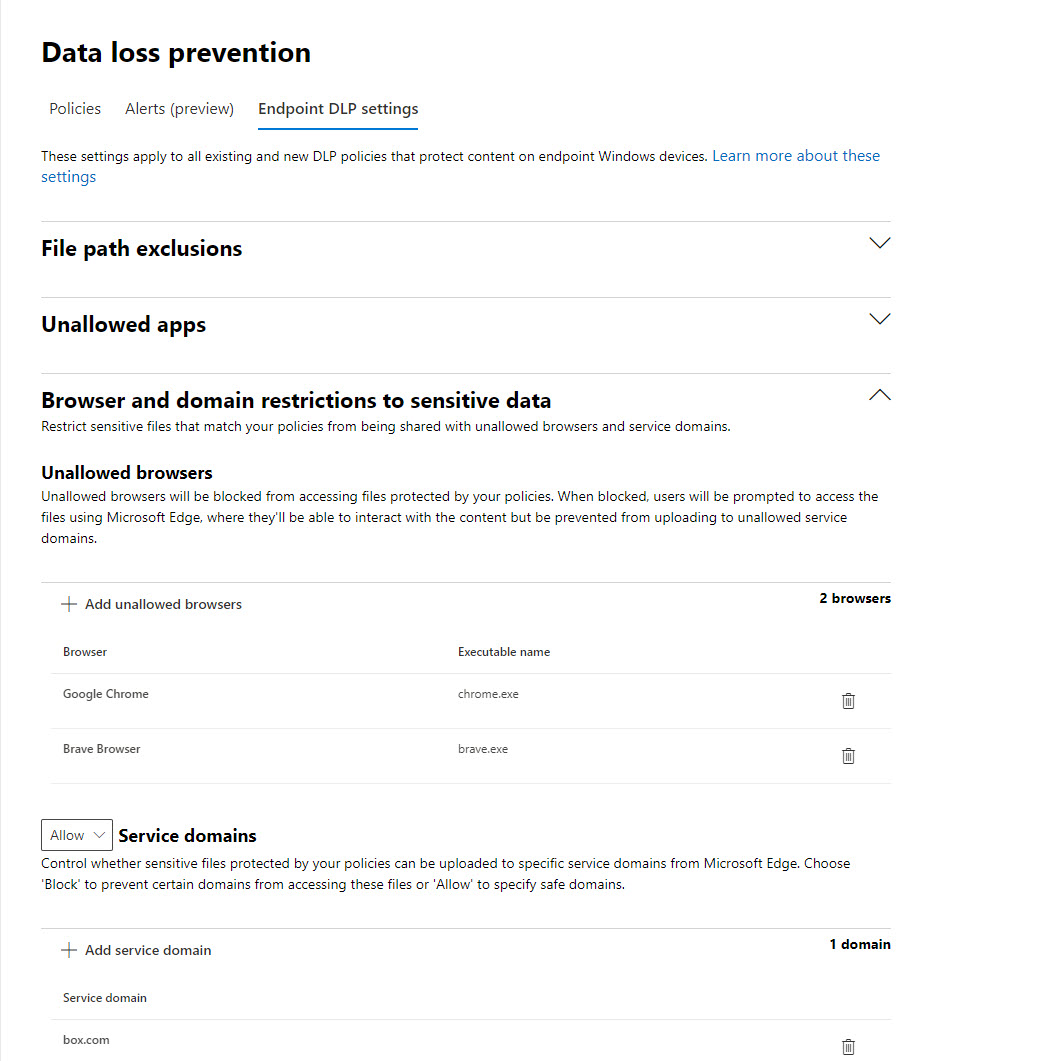
Microsoft has made Endpoint DLP generally available. Leveraging Windows 10 workstations and the Edge browser, Endpoint DLP sends signals for evaluation to detect possible violations. The solution requires Microsoft 365 licenses and only supports Windows, so it’s not for every tenant. But those who have Microsoft 365 licenses will find this an attractive solution.
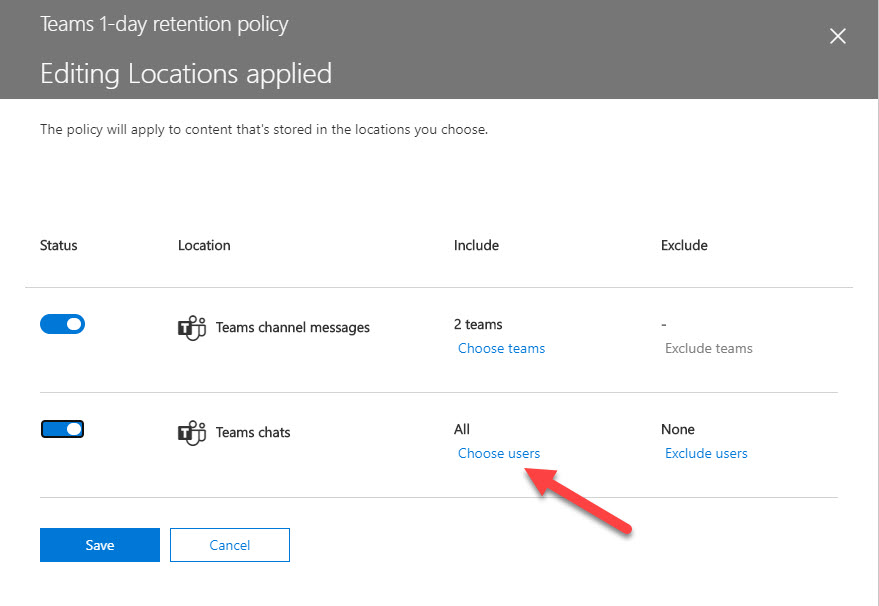
A change made to an Office 365 retention policy for Teams personal chats in the KPMG tenant removed data for 145,000 users. That’s unfortunate, and it underlines the need for admins to understand how retention policies work. Maybe the people involve did and it was a simple slip that could happen to anyone, but perhaps it will cause tenant admins to reflect on how they make changes to organization configurations.
Power Automate (Flow) can forward email from Exchange Online mailboxes to external recipients. This isn’t a great idea if you want email kept within the control of your data governance framework. Power Automate now inserts x-headers in the email it sends, which allows the use of transport (mail flow) rules to detect and reject these messages if required.
Communications compliance policies scan user messages to detect violations of company or regulatory rules. A change introduces support for hybrid users whose mailboxes are on Exchange on-premises servers. The change might not pick up many new violations, but it does increase the coverage and stops some violations sneaking through, which is always a good thing.
Microsoft has released information about high-value Office 365 audit events and audit event retention policies. Both are part of a Microsoft 365 Advanced Audit offering. The MailItemsAccessed event is the first high-value audit event (we can expect more) and the retention policies are used to purge unneeded events from the Office 365 audit log.
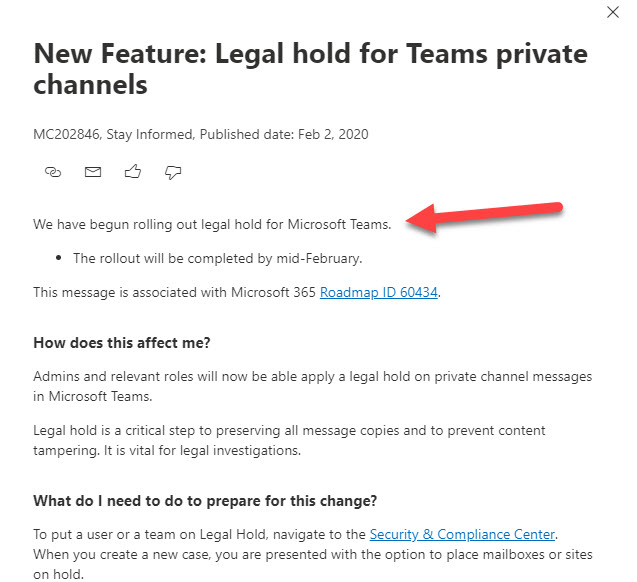
The Office 365 compliance framework can now to place holds on Teams compliance records created for conversations in private channels. You simply have to place holds on the mailboxes of members of the private channels and hope that no one removes the members from the tenant. If they do, the hold lapses, which seems like a pity.
The Microsoft 365 Compliance and Security centers are roling out to Office 365 tenants where they’ll replace the old Security and Compliance Center over time. The new centers look fresher than the SCC, but looks can deceive and it’s much more important that the functionality exposed in the new portals work reliably all the time.
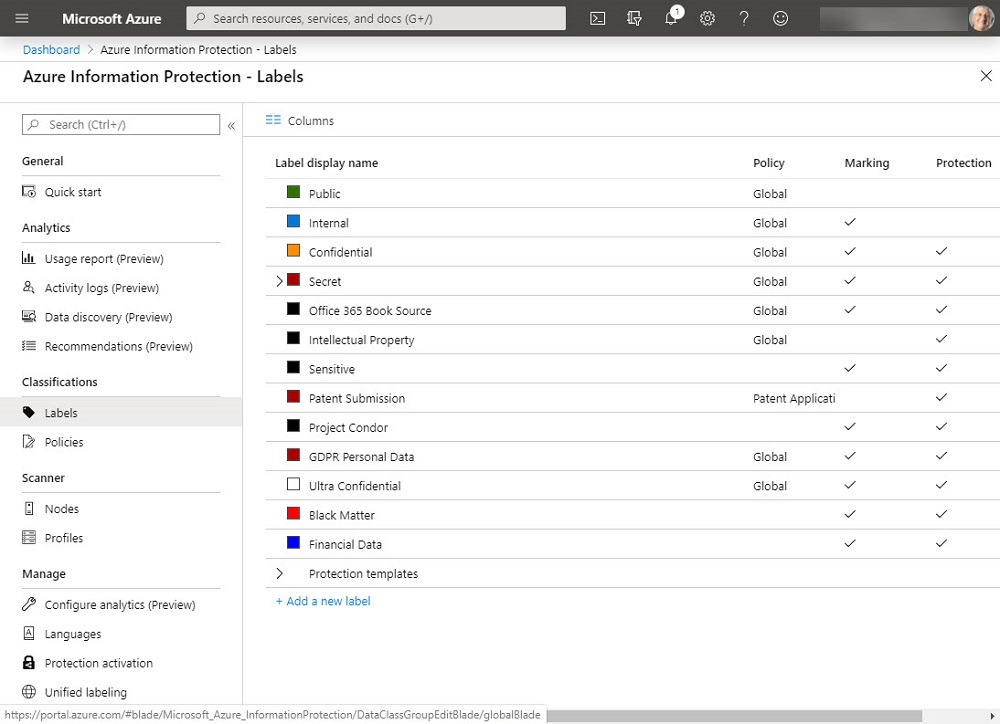
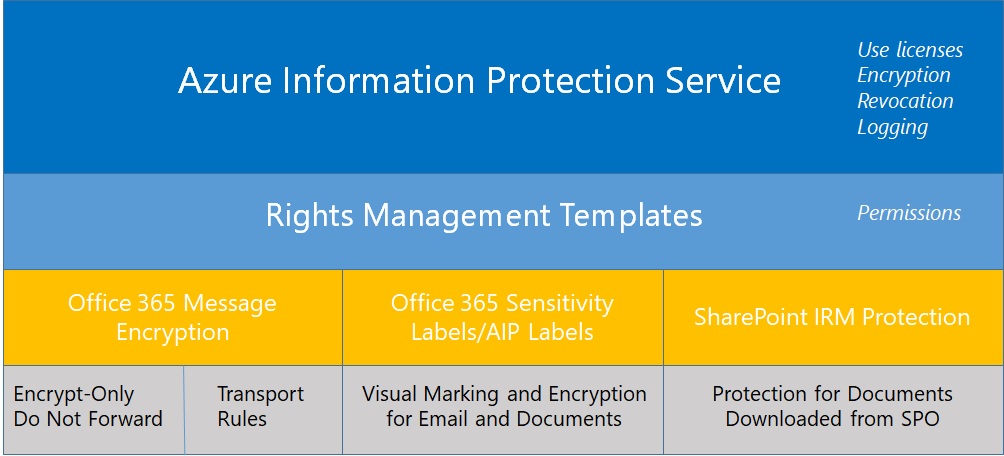
Microsoft retracted the announcement of the deprecation of the classic Azure Information Protection client and label management in the Azure portal. Office 365 sensitivity labels have taken over from AIP clients in most tenants, so the impact of this change is limited. However, if you still need to use an AIP client, you should move to the unified version.
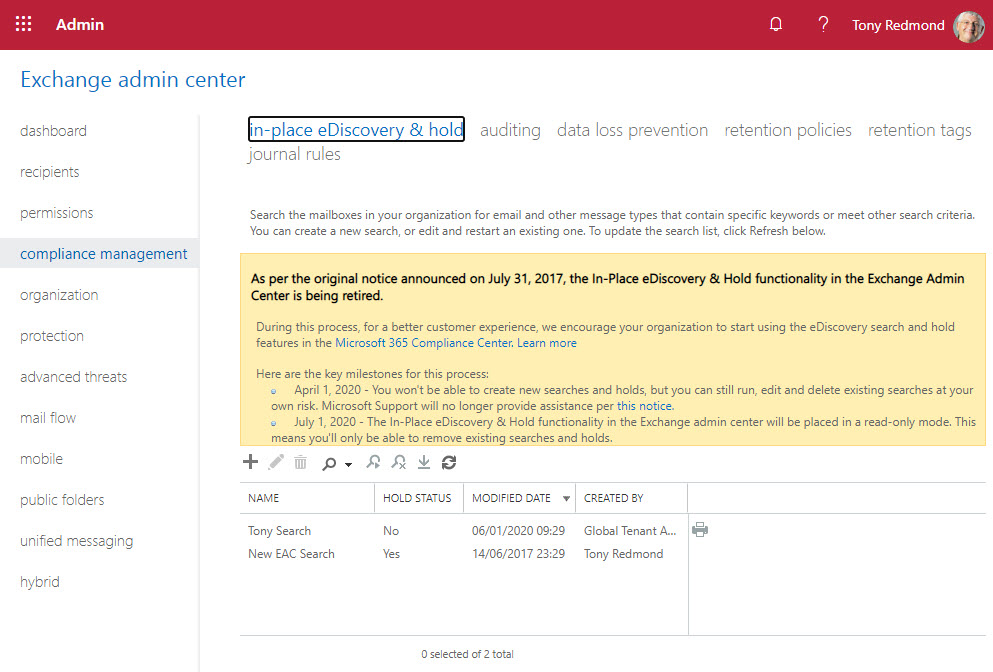
Microsoft announced the retirement of legacy eDiscovery tools from Office 365. The Exchange Online in-place holds and eDiscovery tool, Office 365 Advanced eDiscovery 1, and the Search-Mailbox cmdlet are being retired. All will be gone by mid-2020. It’s a pity to see the Search-Mailbox cmdlet being removed, but time and progress make this kind of thing inevitable.
OWA now supports the automatic labeling of outbound messages with Office 365 Sensitivity Labels. The new feature uses Office 365 sensitive data types to detect content in messages that should be protected, and once detected, the message is stamped with a label before it passes through the Exchange Online transport service.
A busy week included speaking engagements in Germany and Oslo. The Experts Live Norway event saw Tony talk about Office 365 data governance, a topic he thinks he knows well. You can grab a copy of the presentation he used in Oslo from this post.
Exchange Online supports inactive mailboxes as a way to keep mailbox data online after Office 365 accounts are removed. Inactive mailboxes are available as long as a hold exists on them. You can update mailbox properties to exclude all or some org-wide holds. If you exclude holds from a mailbox, you run the risk that Exchange will permanently remove the mailbox. If that’s what you want, all is well, but if it’s not, then you might not be so happy.
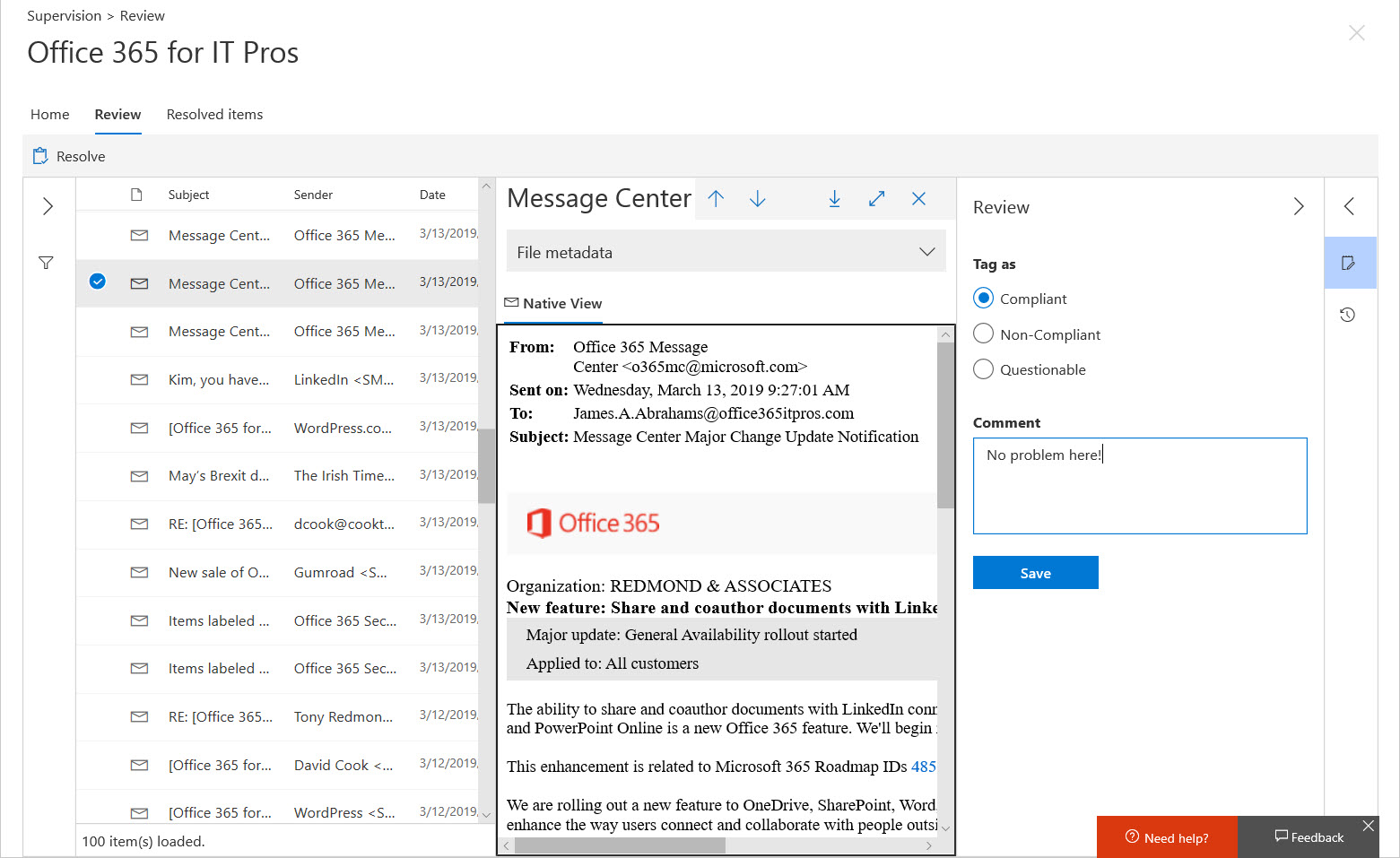
Although Office 365 supervision policies are intended to monitor a subset of user communications, usually involving specific groups of people, you might want to use a policy to monitor all email. In that case, how do you make sure that your policy has everyone in scope? The problem is that supervision policies don’t support dynamic distribution lists, so you need to do some work to build and maintain a distribution list containing all user mailboxes.
If you’re interested in deploying backups for SharePoint Online, you might be doing so to prevent data loss through accidental user deletion. However, Office 365 retention labels and policies can help prevent accidental deletion too. And the best thing is that retention policies and labels are part of Office 365 E3, so you don’t have to pay more to get protection.
Microsoft released an update for the unified labeling version of the Azure Information Protection client needed for Office 365 sensitivity labels, which now boast auto-label support. Solid progress is being made to move sensitivity labels to the point where they are considered to be generally available, probably later this year. In the meantime, pay attention to the premium features like auto-label which require more expensive licenses.
Microsoft announced that the Office 365 E3 and E5 plans will receive new Information Protection licenses. They’re preparing for the introduction of sensitivity labels and the increased use of encryption to protect access to content in Office 365 apps like SharePoint Online, Exchange Online, OneDrive for Business, and Teams. You don’t have to do anything to prepare for the new licenses, but it’s nice to know what they are and how the licenses are used.
Rights management and encryption are likely to be a much more common Office 365 feature in the future. Sensitivity labels makes protection easy for users to apply through Office apps. The downside is that protection makes content harder to access for some Office 365 and ISV functionality.
A question asks how to remove a bunch of emails from a shared mailbox. You can use OWA to do the job, especially with its Cleanup Mailbox option, but perhaps some administrative action is needed.
On Wednesday, November 28, Tony’s speaking about Office 365 Data Governance at the European SharePoint Conference in Copenhagen, Denmark. The topic is interesting, if only because its source material changes all the time.
The availability of Azure Information Protection and Office 365 sensitivity labels allow tenants to protect important and confidential files. That’s nice, but it’s even better when you know what files are protected. Here’s how to use PowerShell to create a report about those files.
Following a Dutch report saying that Office 365 might violate GDPR, some thoughts about how to restrict some of the flows of information from an Office 365 tenant to Microsoft.
A little known fact is that you can use graphic symbols and characters in Office 365 labels. It might bring a splash of color to your compliance and retention efforts, especially in a world where emojis are everywhere. After all, the symbols are just character codes that computers can process and Office 365 is designed to be multilingual and cope with different character sets (like the way Teams deals with Hebrew and Arabic).
Content Searches Find Teams Compliance Items When someone leaves your company, you might need to preserve their Office 365 data. The steps needed to preserve user information stored in Email, OneDrive, and SharePoint are straightforward, but what about the messages the employee sent using Teams? As it turns out, an Office 365 content search or …
Read More “Preserving the Teams Data of Ex-Employees”
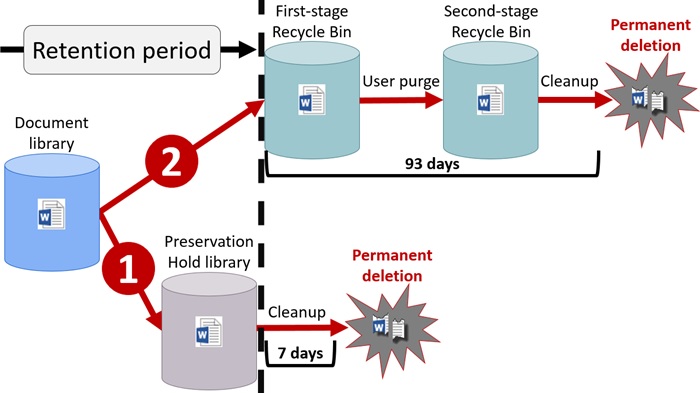
Microsoft Teams support Office 365 retention policies, but how do you know if policies you create are effective in removing items from Teams? Well, as it turns out, you must go poking under the covers to validate that removals happen as planned.