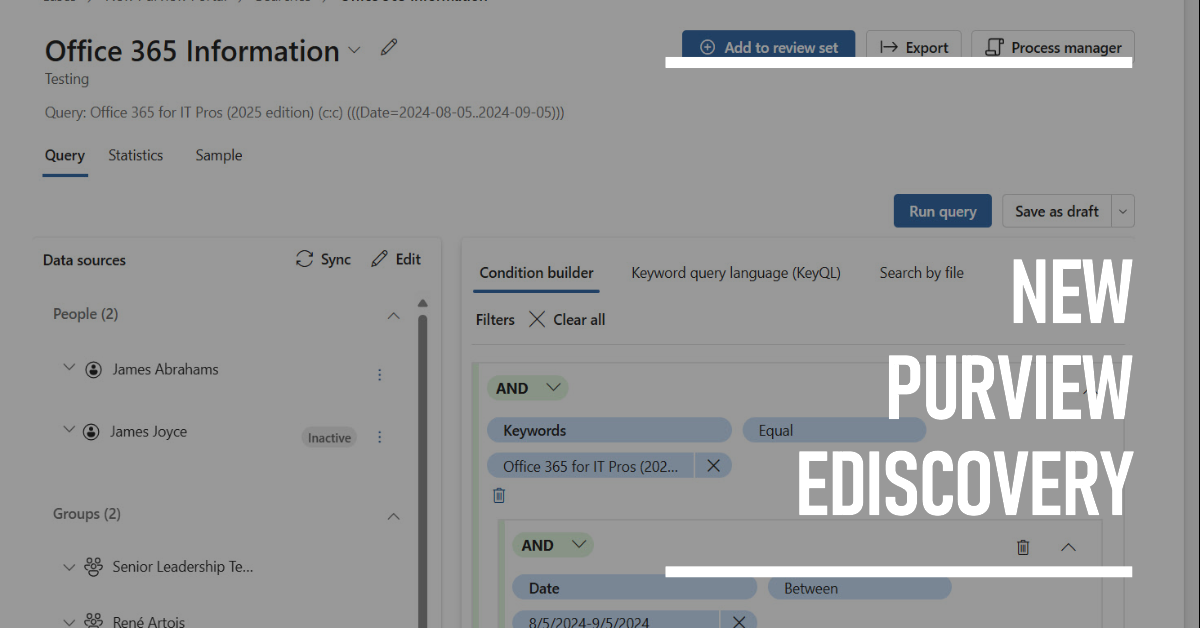
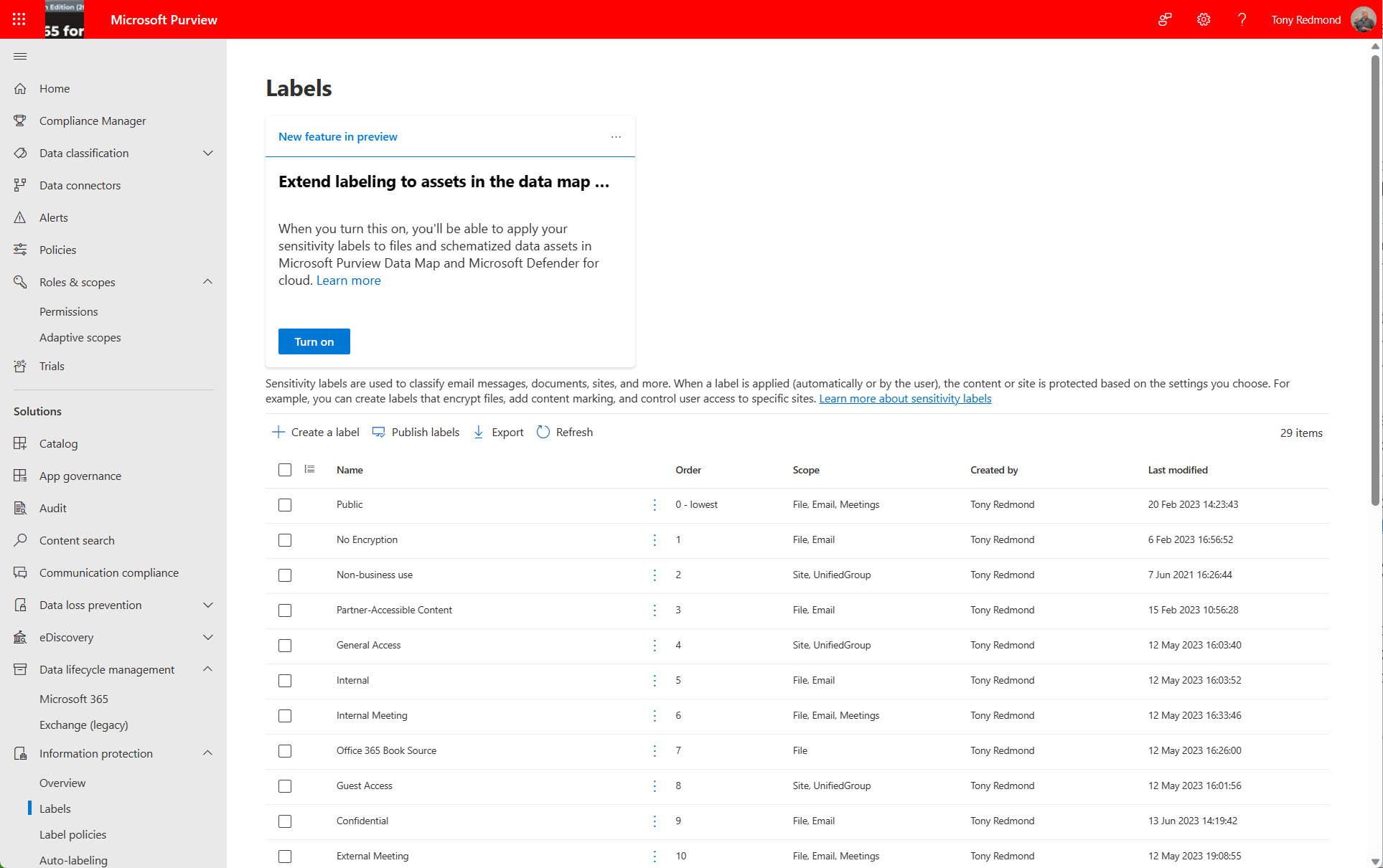
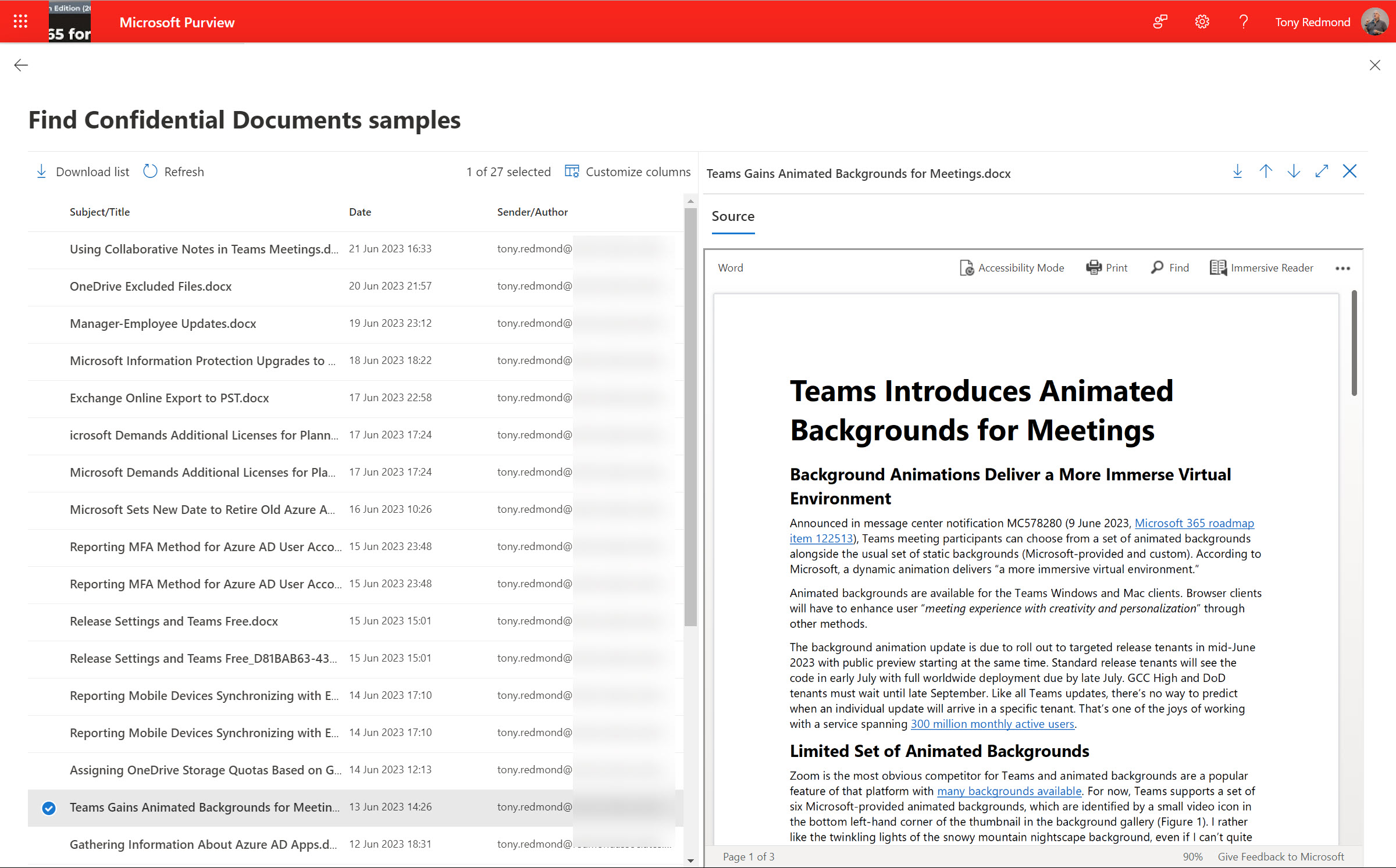
eDiscovery is a calling best left to skilled investigators. But Microsoft 365 administrators need to know how to search and how the new Purview eDiscovery works. The new implementation is due by the end of 2024 and is in preview now. It unifies the three existing solutions in the Microsoft 365 eDiscovery space and promises to deliver new functionality. But will it make its dates? Who knows!
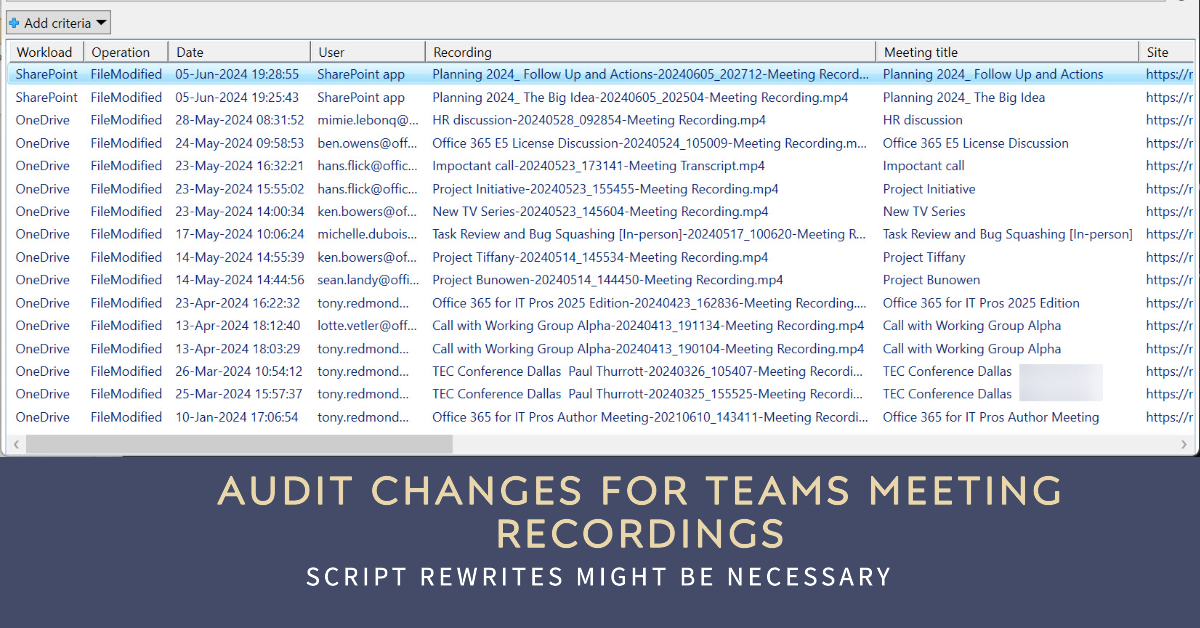
Three years ago, I wrote a script to analyze the audit records generated for Teams meeting recordings. Then things changed in terms of how the audit records were generated and how the Search-UnifiedAuditLog cmdlet returns audit search results. All of which meant that considerable work was needed to revamp (rewrite) the script. Maybe you need to check any script that uses the Search-UnifiedAuditLog cmdlet too?
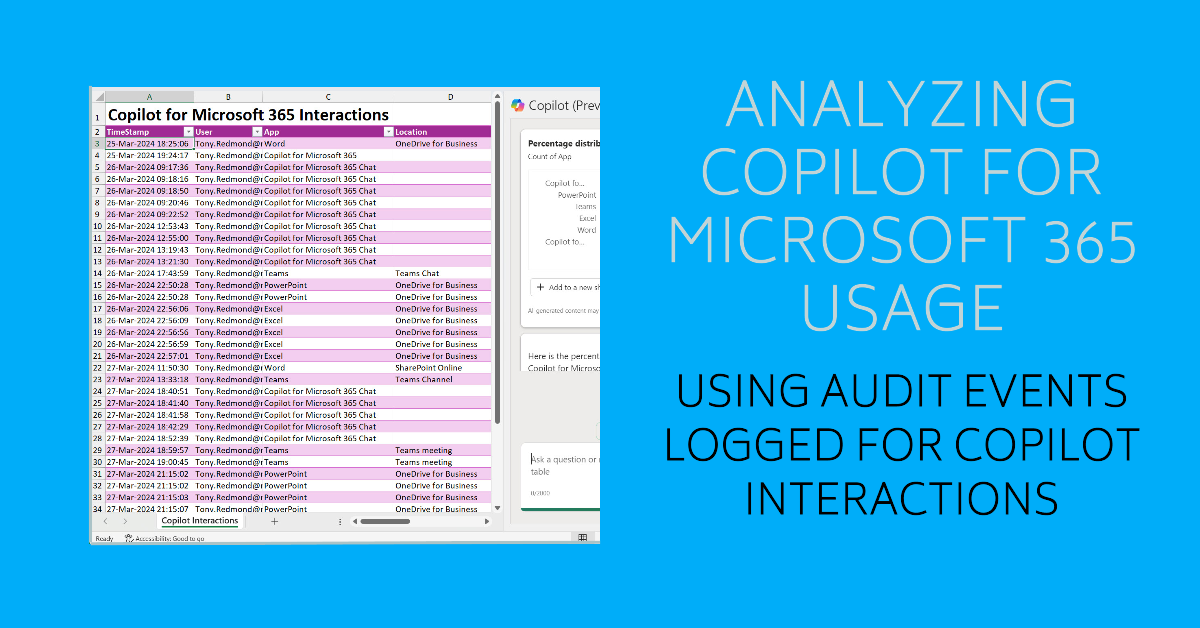
The unified audit log includes Copilot for Microsoft 365 audit events captured when users interact with Copilot through apps. The information is very helpful in terms of understanding the usage of Copilot in different apps (apart from Outlook, which isn’t captured). Some care needs to be taken to understand the data and interpret the audit events, but that’s usual when dealing with Microsoft 365 audit data.
A new preview feature supports high completeness audit log searches. These searches are optimized to make sure that they find every matching audit instead of finishing as quickly as possible. High completeness audit log searches do take more time but their results are accurate and they find more records than Search-UnifiedAuditLog was able to in the past. Looks like a good new feature.
A January 26 post announces the deprecation of four old Exchange audit cmdlets in favor of the Search-UnifiedAuditLog cmdlet. Removing old cmdlets is fine, but it would be nice if Microsoft took the opportunity to make Search-UnifiedAuditLog work better. Too many inconsistencies exist in how workloads provide information in audit events and Microsoft has made some recent unannounced changes.
In message center notification MC703706 Microsoft announces yet another attempt to retire the Search-Mailbox cmdlet. This time it’s due to happen in March 2024. I don’t mind Microsoft removing old technology from its products, but it’s important that the old functionality is replaced by newer, better technology. And that’s not the case here. At least, not so far.
The Sensitive by Default control allows tenants to prevent external access to newly uploaded documents until DLP processing checks their content. The idea is to close off the opportunity external users have to access control between its upload and DLP scanning of the content. You can combine the sensitive by default control with sensitivity labels to exert maximum control over confidential material.
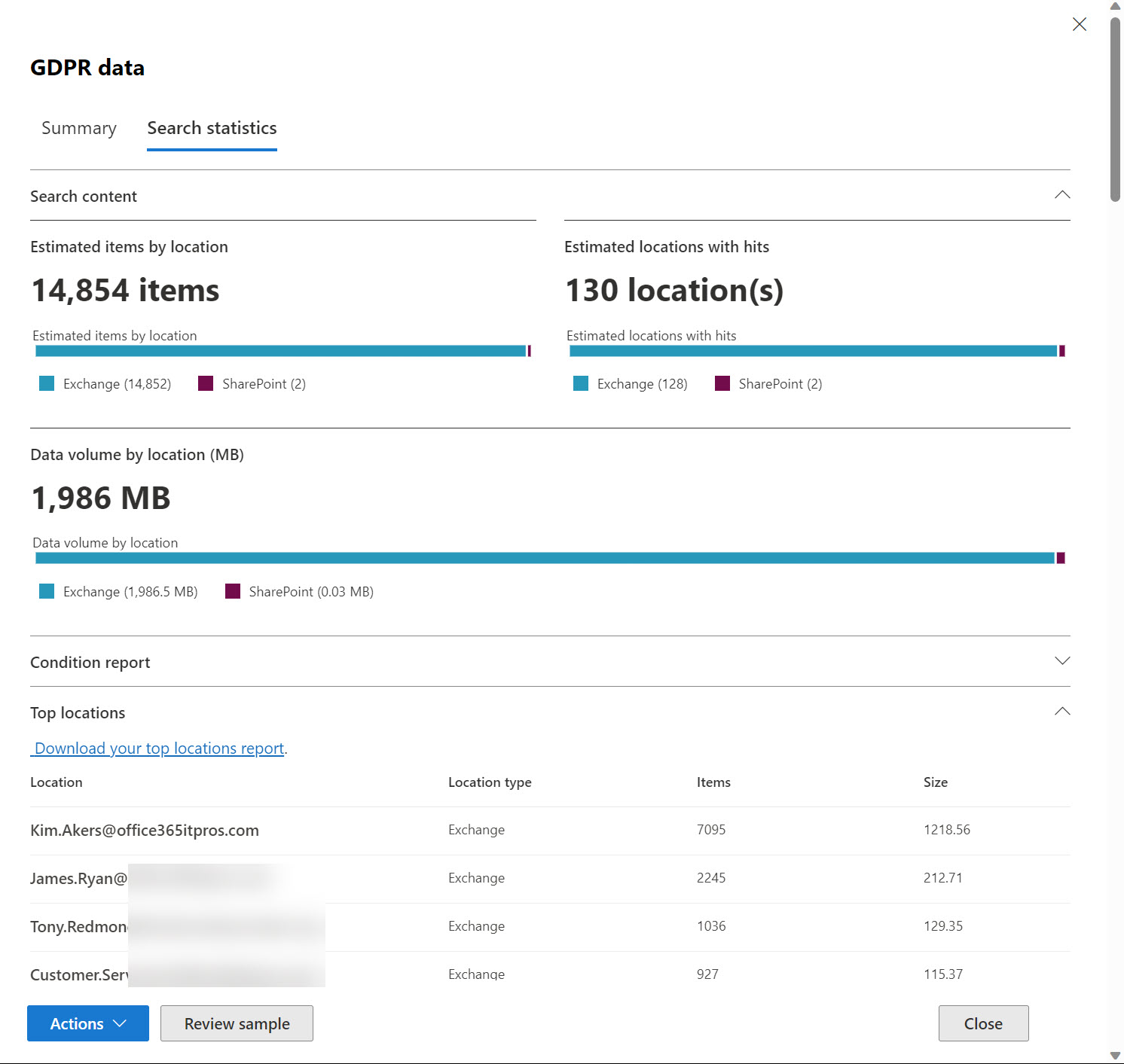
Microsoft plans to make an eDiscovery hold report available to tenants in January 2024. This article explains how to use PowerShell to create a similar report. Without seeing what Microsoft plans, it’s hard to create a perfect replica, but it will be possible to upgrade the script once Microsoft reveals their hand.
Entra ID administrative units are supported for granular access to the Microsoft 365 audit log. Exchange Online manages the audit log so it’s core to the support. This article reviews how to restrict access to the audit log using compliance roles and RBAC and how administrative unit data is stamped onto audit events during ingestion to support restricted searches based on administrative units.
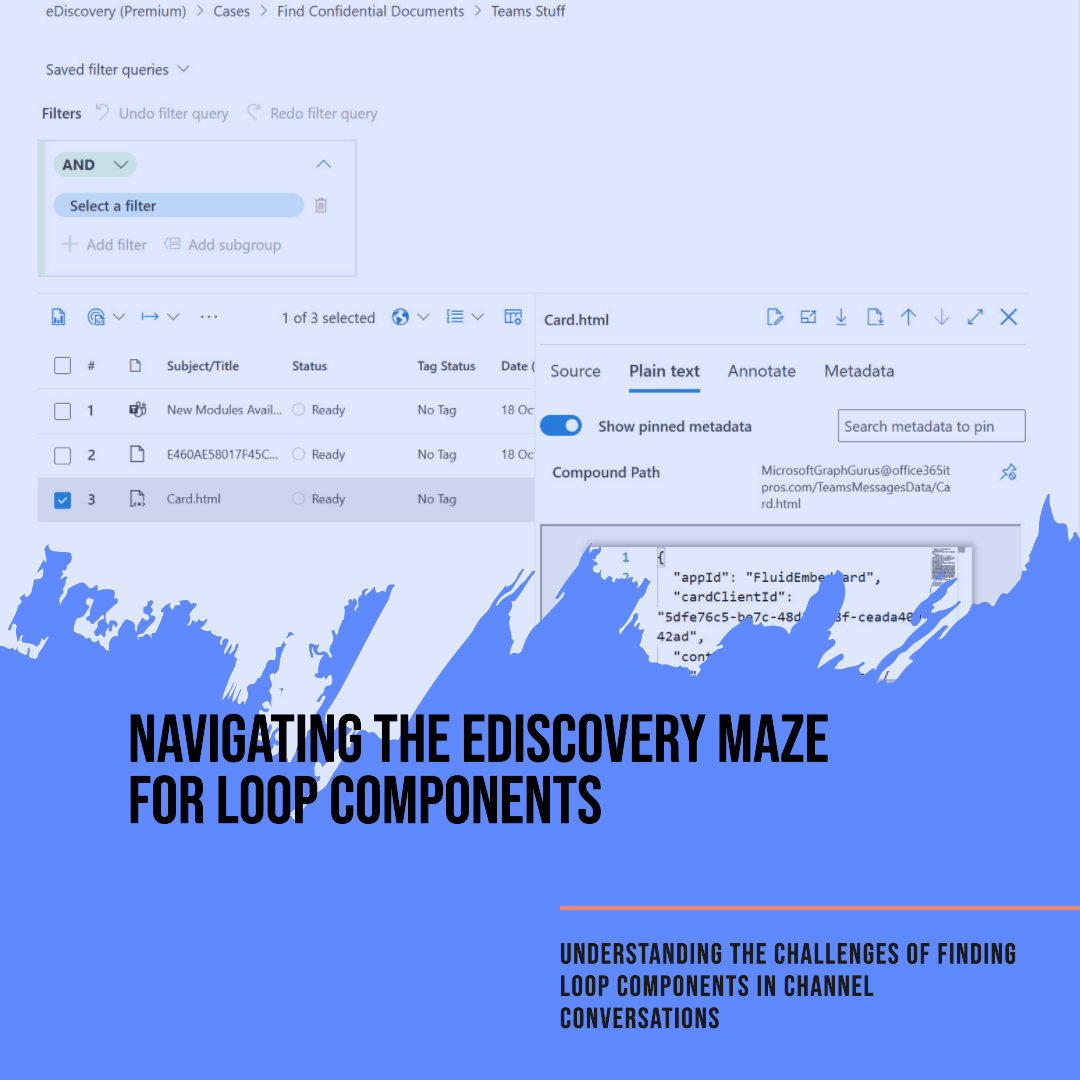
Following new support of Loop components for Teams channel conversations, it’s sad to discover that Loop component eDiscovery remains challenging two years after the first appearance of component technology in a Microsoft 365 application. eDiscovery can certainly find Loop components, but creating a seamless picture about their usage is harder than it should be.
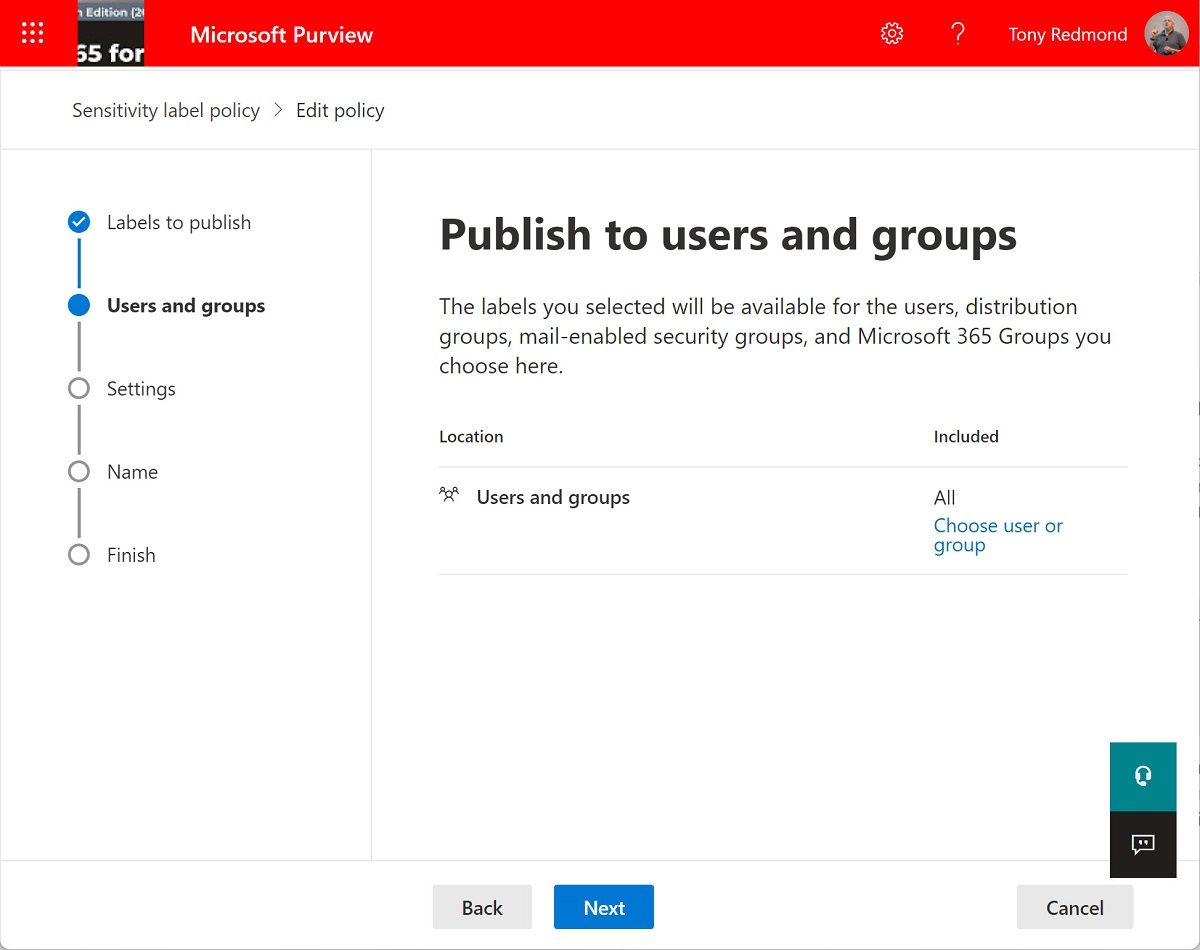
A question about finding out which sensitivity label policy makes a label available to a user requires some PowerShell to figure out the answer with some human-friendly results. The outcome is a script that analyzes sensitivity label policies to find where a user gets their labels from. It’s another example of how useful PowerShell can be.
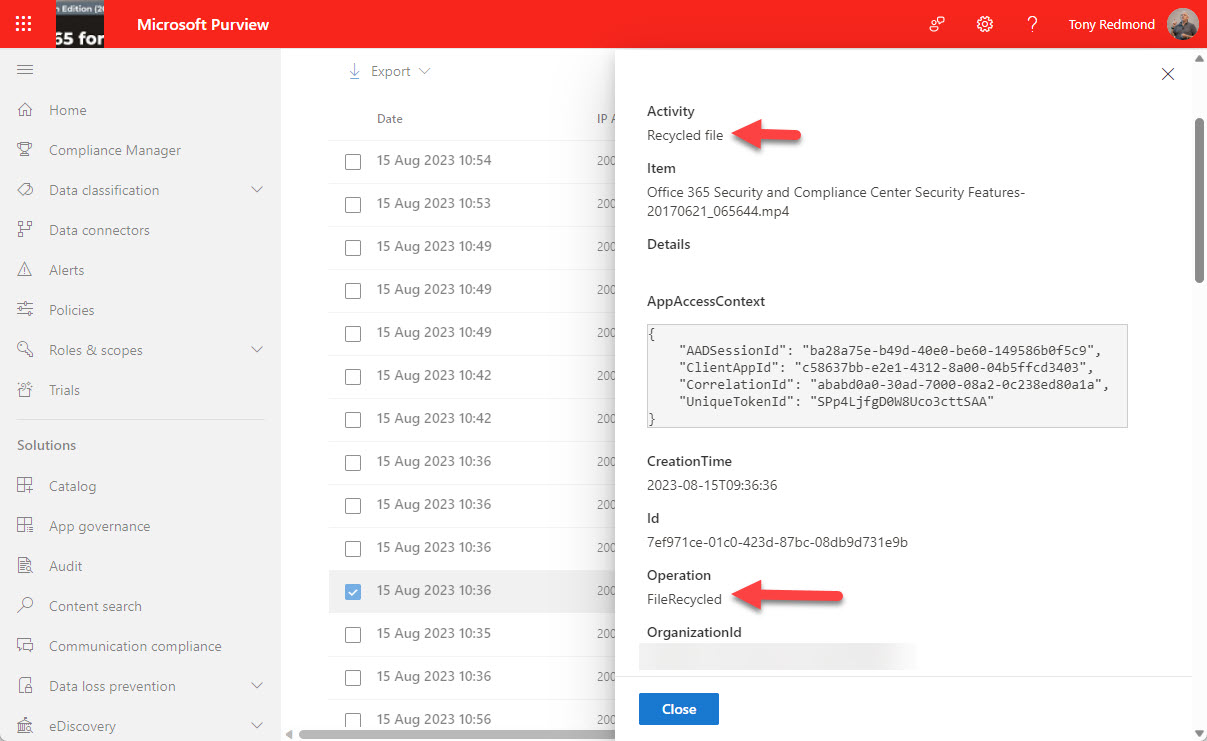
For years, I have scanned the audit log to find FileDeleted events to report deletions of SharePoint and OneDrive documents. Now, FileRecycled audit events are used instead. This wouldn’t be a problem if Microsoft had told customers, but not a trace can be found to let organizations know that the audit data they use for compliance operations has changed. I don’t know if this is the only activity name change, but given that one update has happened (and for a relatively important audit event), it’s likely that others lurk in the undergrowth.
Microsoft has announced that they are replacing the user data search tool with Purview eDiscovery standard. The change will happen on 30 August 2023 and active user data search cases will be transferred automatically to eDiscovery standard at that point. The change makes sense because the user data search tool hasn’t been enhanced much since its inception. Anyway, user data search cases were simply a special form of eDiscovery case, and now they’re all the same.
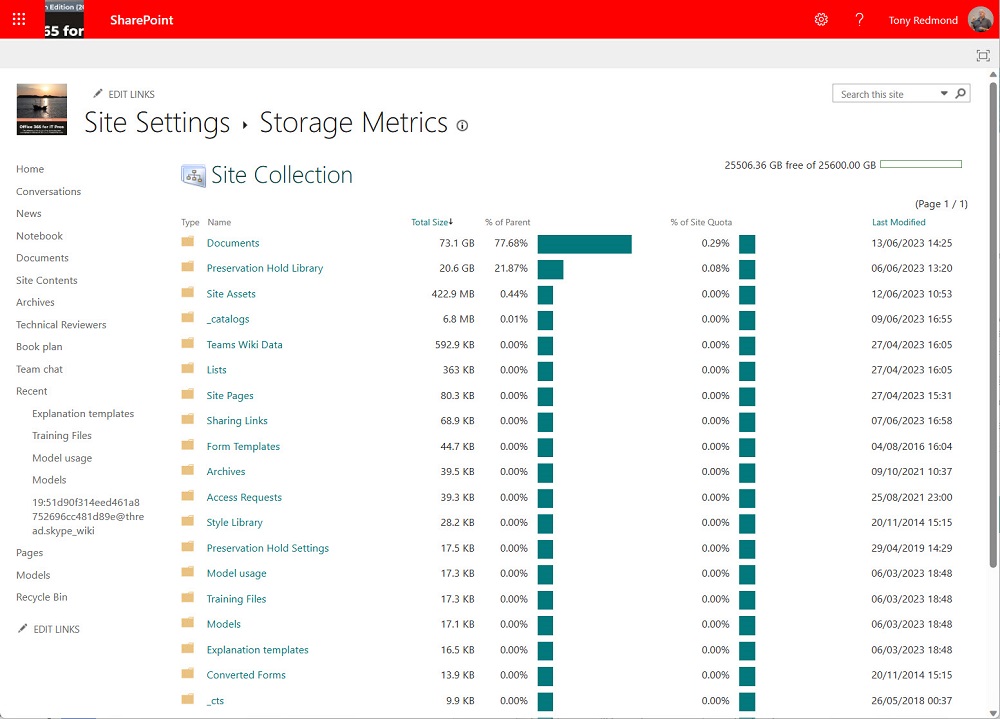
The SharePoint Preservation Hold Library is where files needed for retention or hold purposes are stored. In the past, the library stored separate copies of each version of a retained file. Now it stores files complete with the entire version history, which is more intelligent and means that SharePoint consumes less storage for retention.
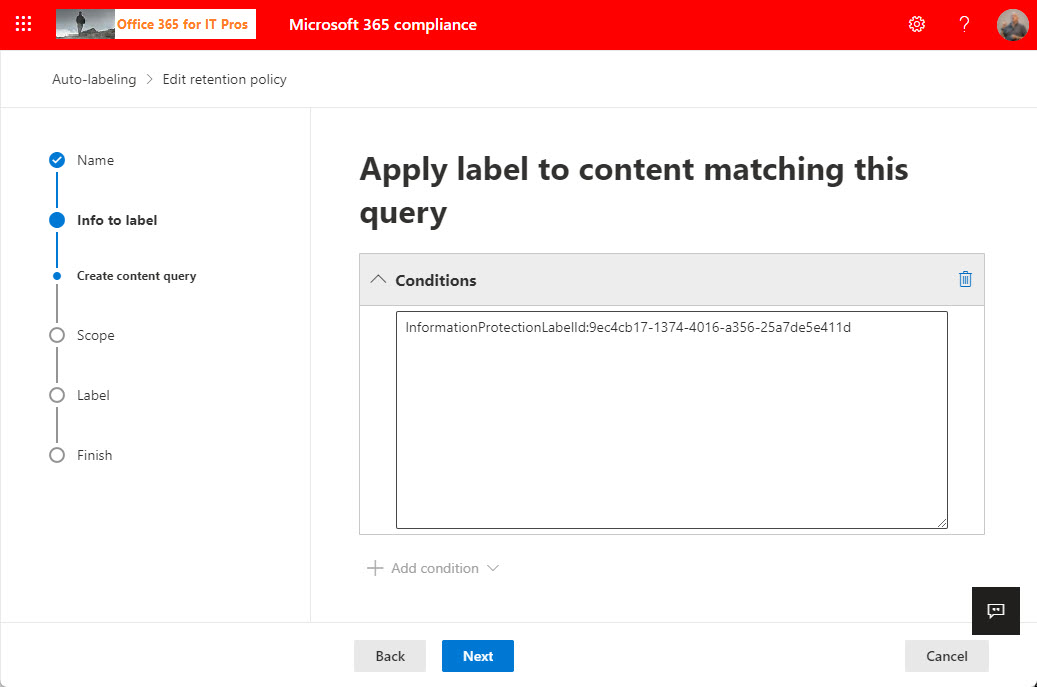
The need to find SharePoint documents with sensitivity labels might arise during a tenant divestiture to decrypt the documents before the split. As it turns out, searches against the SharePoint InformationProtectionLabelId property is a good way to find the files. After that, the need arises to decrypt the documents, which is where Microsoft Purview eDiscovery (premium) might come in handy.
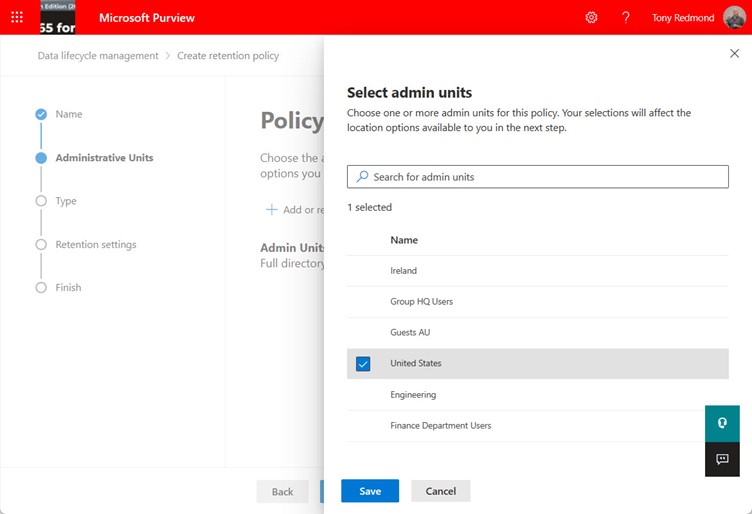
Microsoft Purview data lifecycle management (retention labels and policies) support Azure AD administrative units to scope the set of objects that compliance administrators can manage. Administrative units can be used with data lifecycle management, data loss prevention (DLP), and information protection (sensitivity labels). You’ll need Microsoft 365 E5 licenses (or equivalents) to manage the policies, but that shouldn’t be an issue for the kind of enterprise tenants Microsoft is targeting this functionality at.
Following the removal of Remote PowerShell connections for Exchange Online, Microsoft is removing Remote PowerShell for the compliance endpoint. The change to REST-based cmdlets is expected to deliver better performance and reliability. The changes are implemented in V3.2 of the Exchange Online management module, which should be available on May 1.
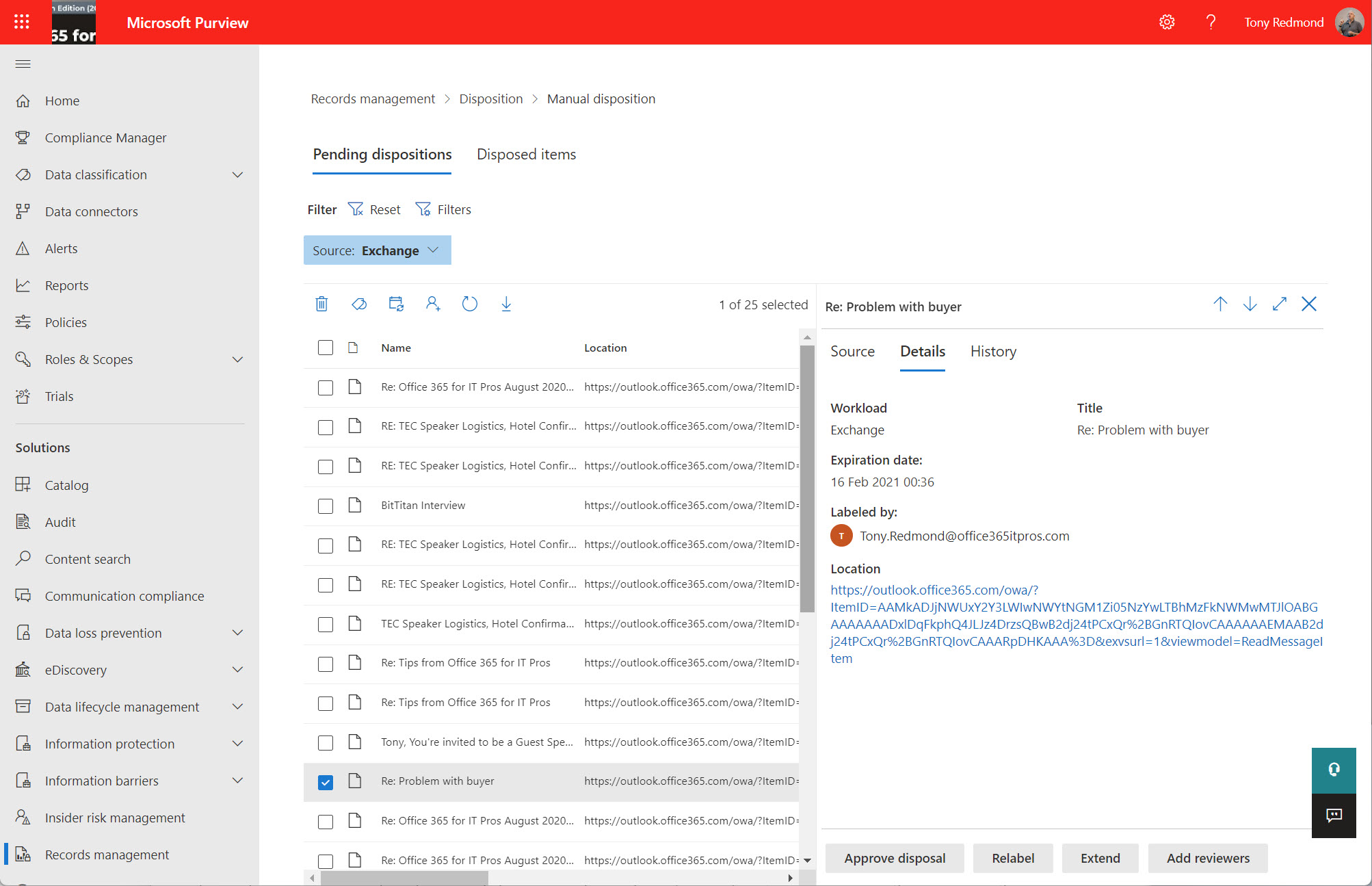
The Get-ReviewItems cmdlet (in the Exchange Online management module) is available to export details about disposition review items in either a pending or disposed state. It’s possible that you don’t care very much about records management, retention labels, or disposition processing, but if you do, you’ll be glad that the new cmdlet exists.
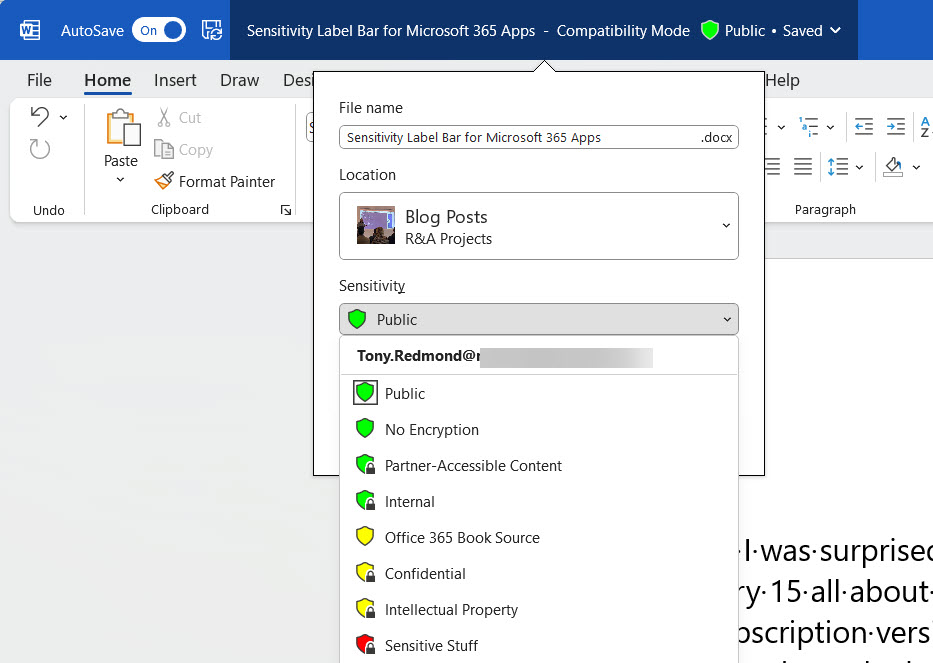
The subscription versions of the Office desktop apps now boast a sensitivity bar to show users what sensitivity label applies to the document they’re working on. It’s a good change because it means that people have full access to information about available labels. You can opt to hide the sensitivity bar, meaning that you hide the name of the sensitivity label rather than the complete bar.
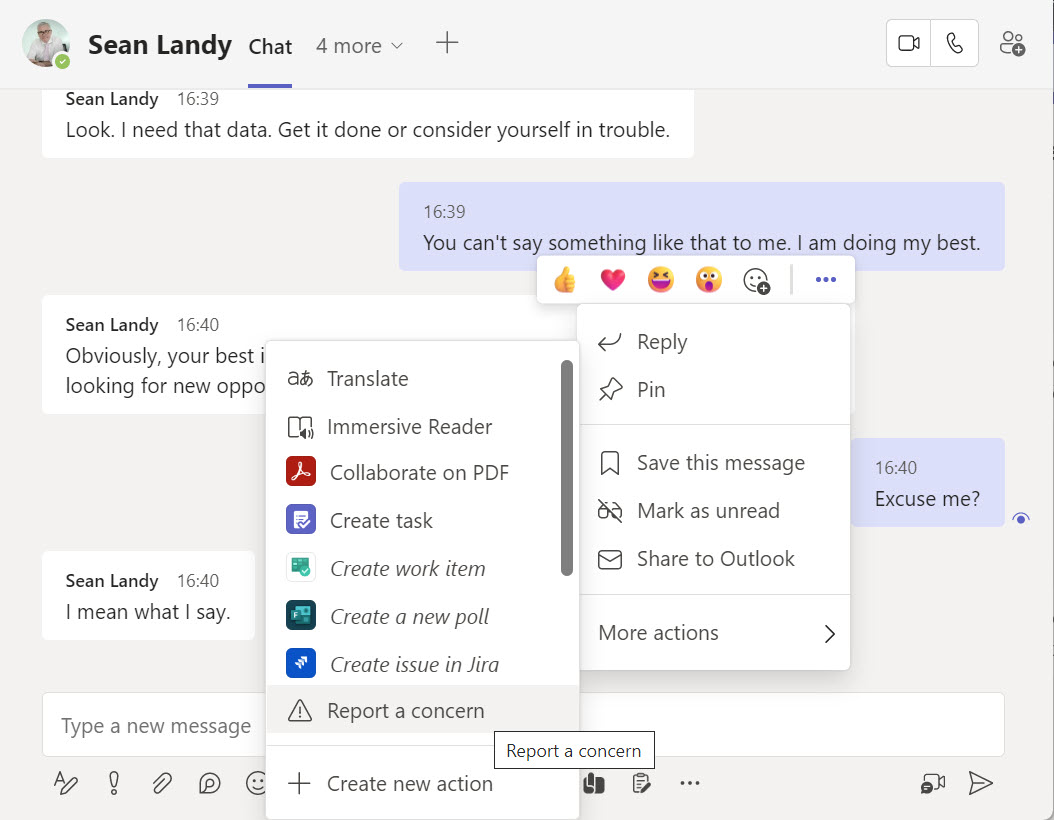
The Report a concern option is available in Teams personal and group chats when enabled in a messaging policy and the organization uses communication compliance policies. Microsoft creates a communication compliance policy automatically to process messages reported by users. The investigation process follows the same flow as for other communication compliance policies, even if the messages might vary a tad in terms of their content because it’s a very subjective decision by a user to report content. Overall, a nice feature to have.
A reader asks how to monitor membership changes for some specific high-profile groups. You can buy a commercial product to do the job or use PowerShell to exploit the information held in the Office 365 audit log. A combination of a custom attribute assigned to the sensitive groups and an audit log search does the job.
In March 2020, I wrote about mailbox audit events for Office 365 E3 accounts not showing up in the Office 365 audit log. As far as I can tell, Exchange Online deals with new mailboxes properly now. However, there might be some mailboxes in your organization that aren’t generating the audit records you thought they are… so it’s time to check.
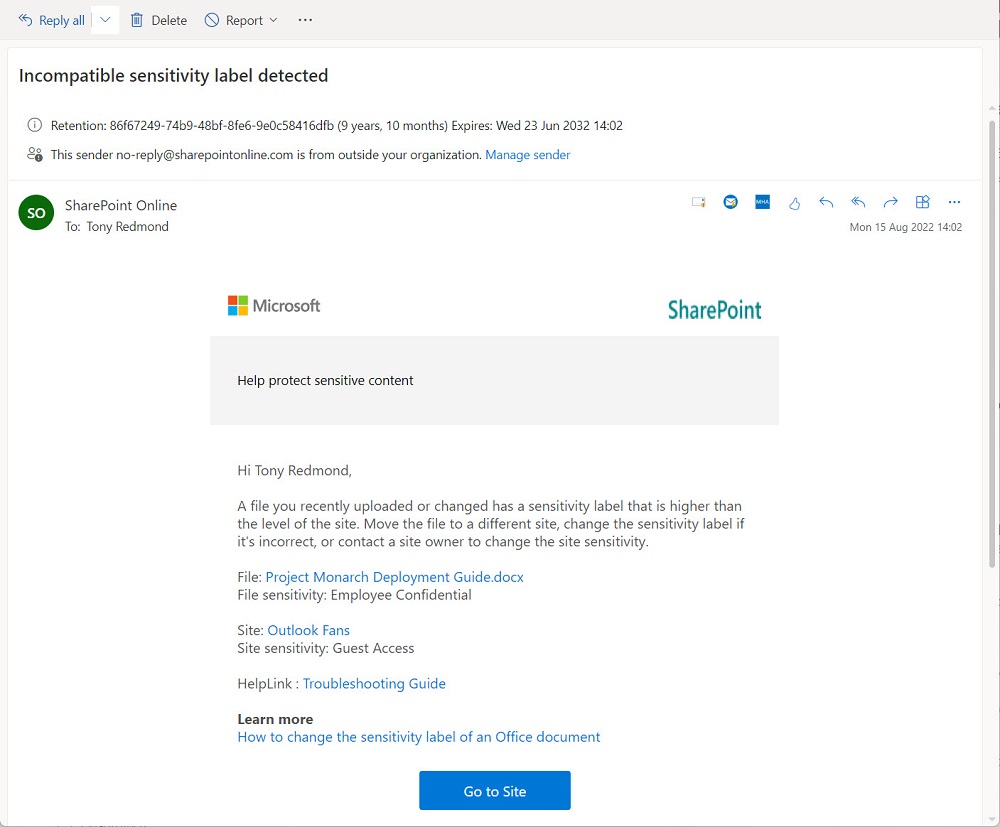
Document label mismatches happen when users create, upload, or update Office documents in SharePoint sites and give the documents a higher-priority sensitivity label than the one assigned to the site. When this happens, SharePoint Online creates a DocumentSensitivityMismatchDetected audit event. Unhappily, that event doesn’t tell us who caused the mismatch, but some work with PowerShell reveals all.
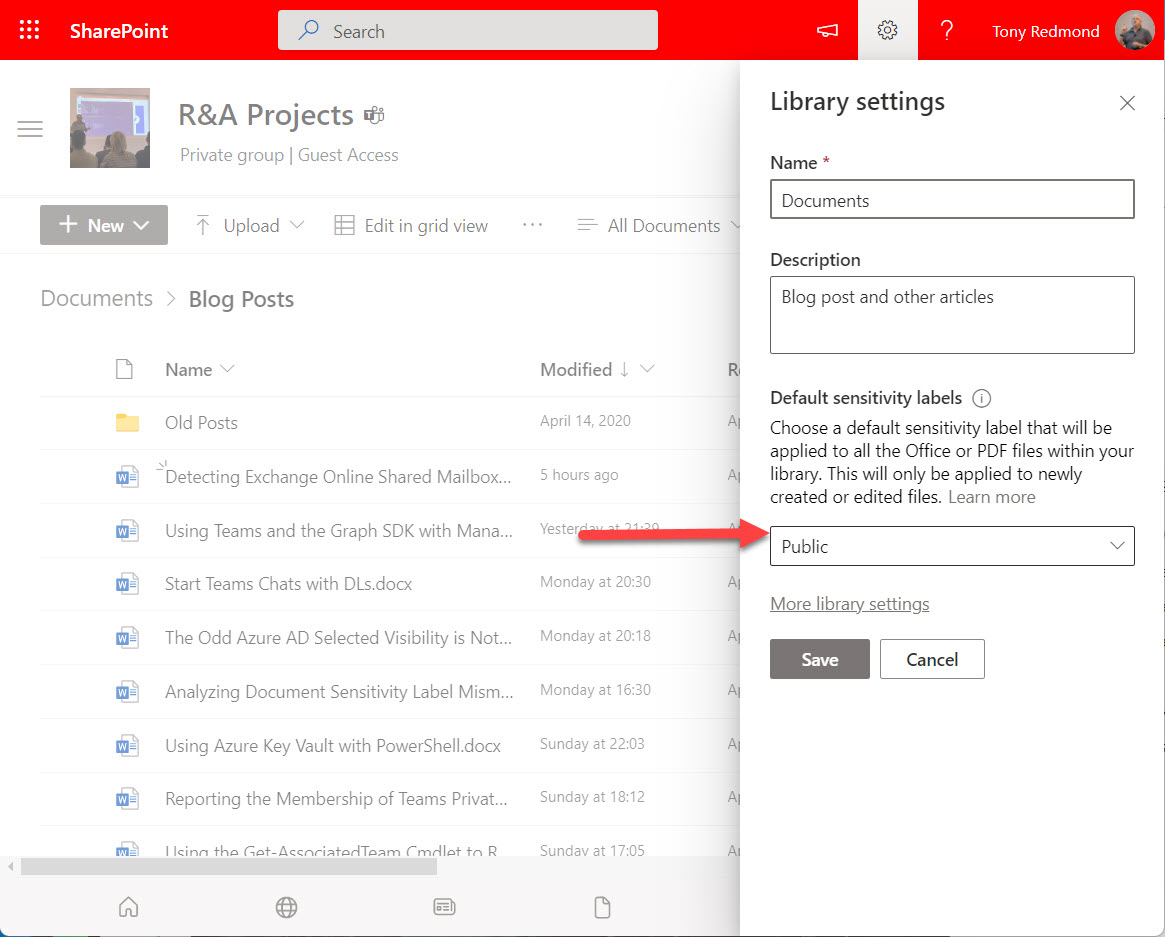
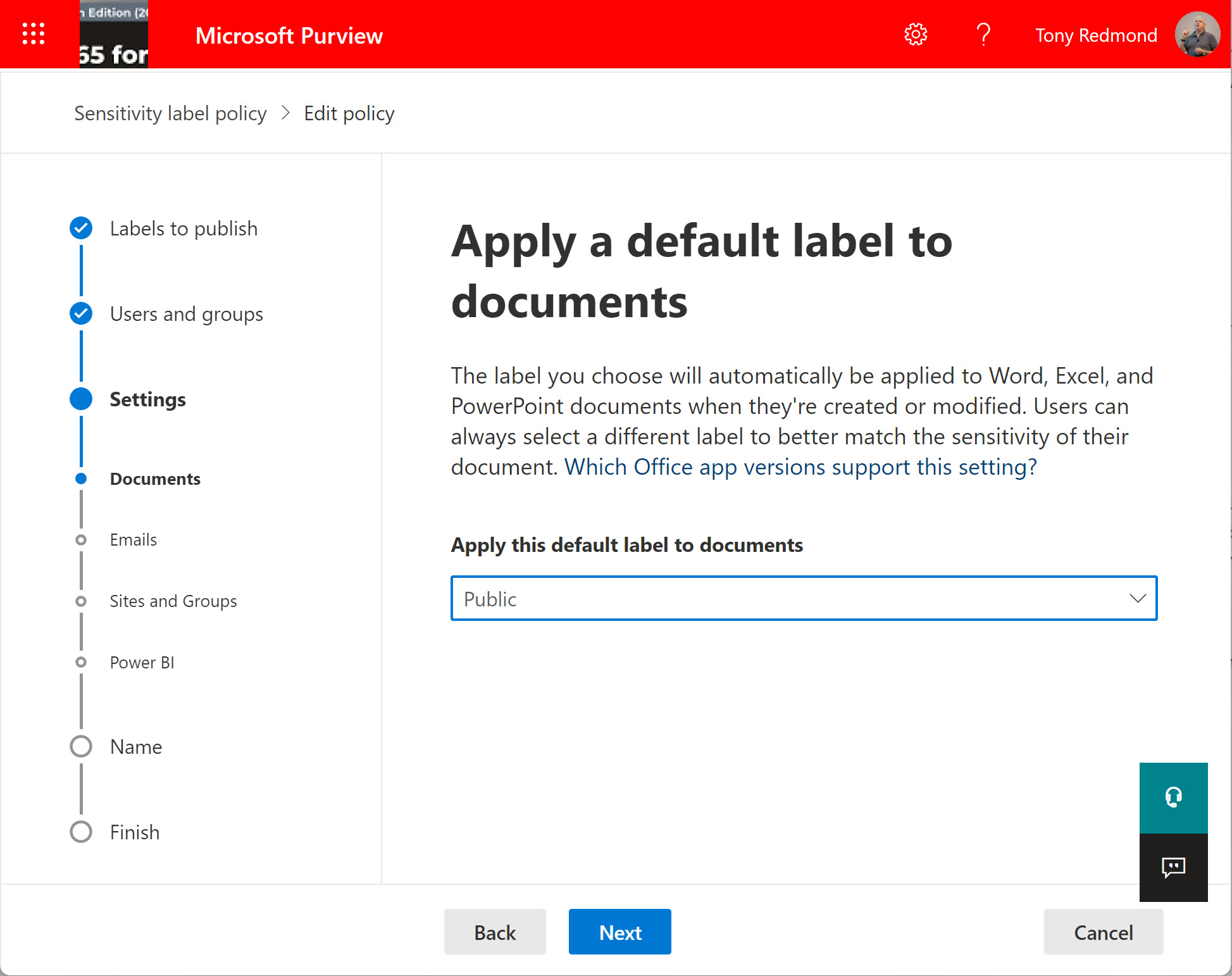
Microsoft is rolling out the public preview of the ability to set a default sensitivity label for SharePoint Online document libraries. This is likely to be a premium feature when it is generally available. For now, Office documents are supported, but Microsoft promises to support PDFs in the future.
In a welcome move, Microsoft has revamped its guidance for Microsoft 365 compliance licensing, specifically for Data Lifecycle and Records Management. The new text is much clearer about when different licenses are needed to use a feature, which is goodness even if you disagree that a feature should need a high-end license. Now if only Microsoft could do the same for the rest of its documentation…
Microsoft has released 42 new sensitive information types (SITs) in preview. The new SITs cover credentials used in services such as Azure, GitHub, Amazon, and Google, and can be deployed in Purview solutions like DLP and auto-labeling policies.
An update for SharePoint Online and OneDrive for Business means that the Office desktop apps (Windows and macOS) will apply default sensitivity labels to documents that aren’t already labeled. This is a good change because it helps to close a gap for organizations that want to be sure that every document is labeled.
The GUI of the Microsoft Purview compliance center doesn’t support the exclusion of selected mailboxes when the special All target is used. However, you can use PowerShell to add mailbox exclusions to sensitivity label policies, including adding the members of a group as exclusions.
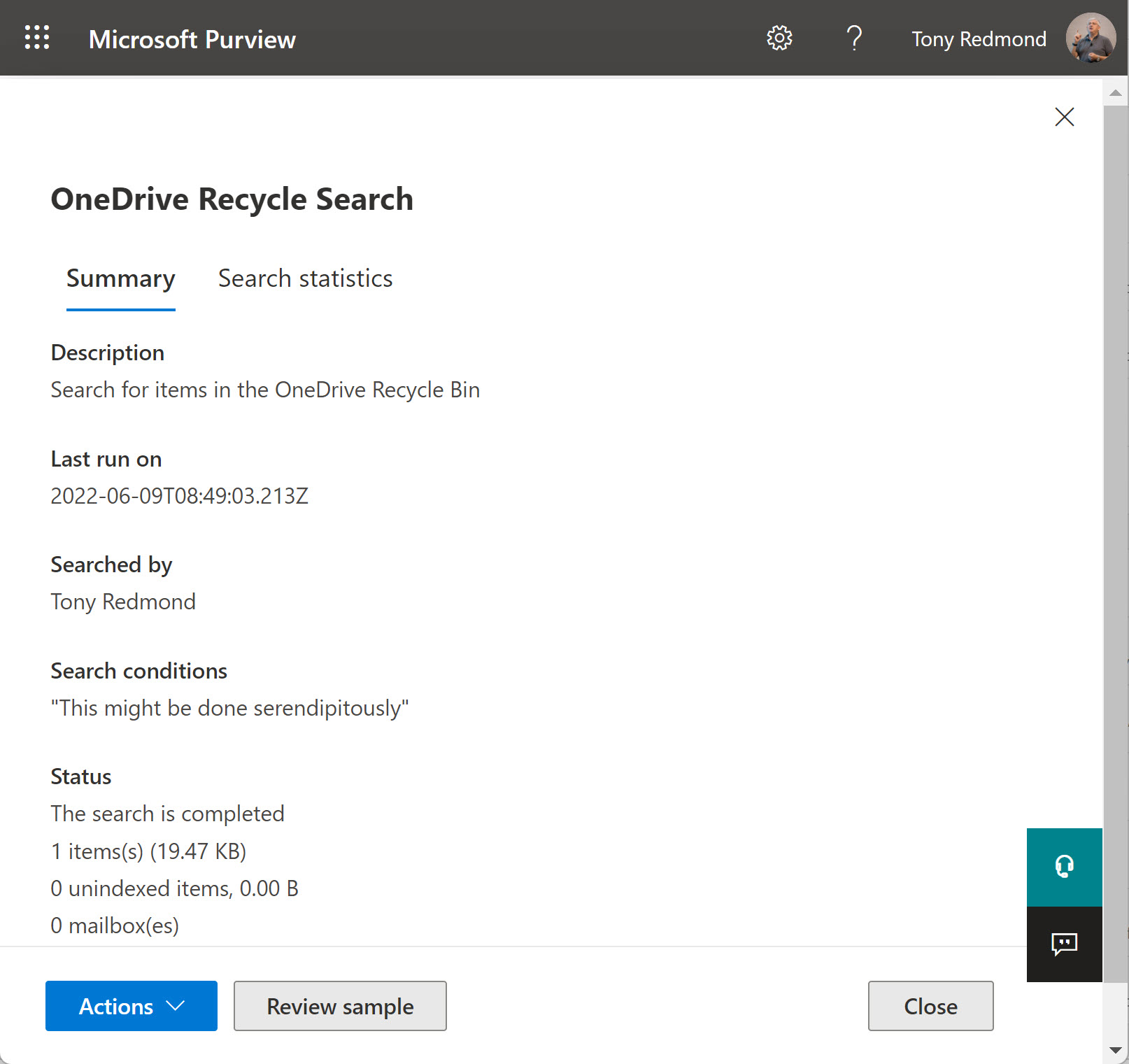
For whatever reason, Microsoft documentation says that items in the OneDrive for Business recycle bin are not indexed and cannot be discovered. They’re wrong. Searches can find items which end up the in OneDrive for Business recycle bin and any holds that applied to those items are respected. Maybe it’s just a matter of phrasing, but this proves once again that documentation can be incorrect. Just like blog posts!
Microsoft will soon make an update available for Purview Premium eDiscovery to reveal Teams reactions to chats and channel conversations when investigators review the results of searches. The information comes from Teams rather than the compliance records stored in Exchange Online. The new feature isn’t coming to Standard eDiscovery.
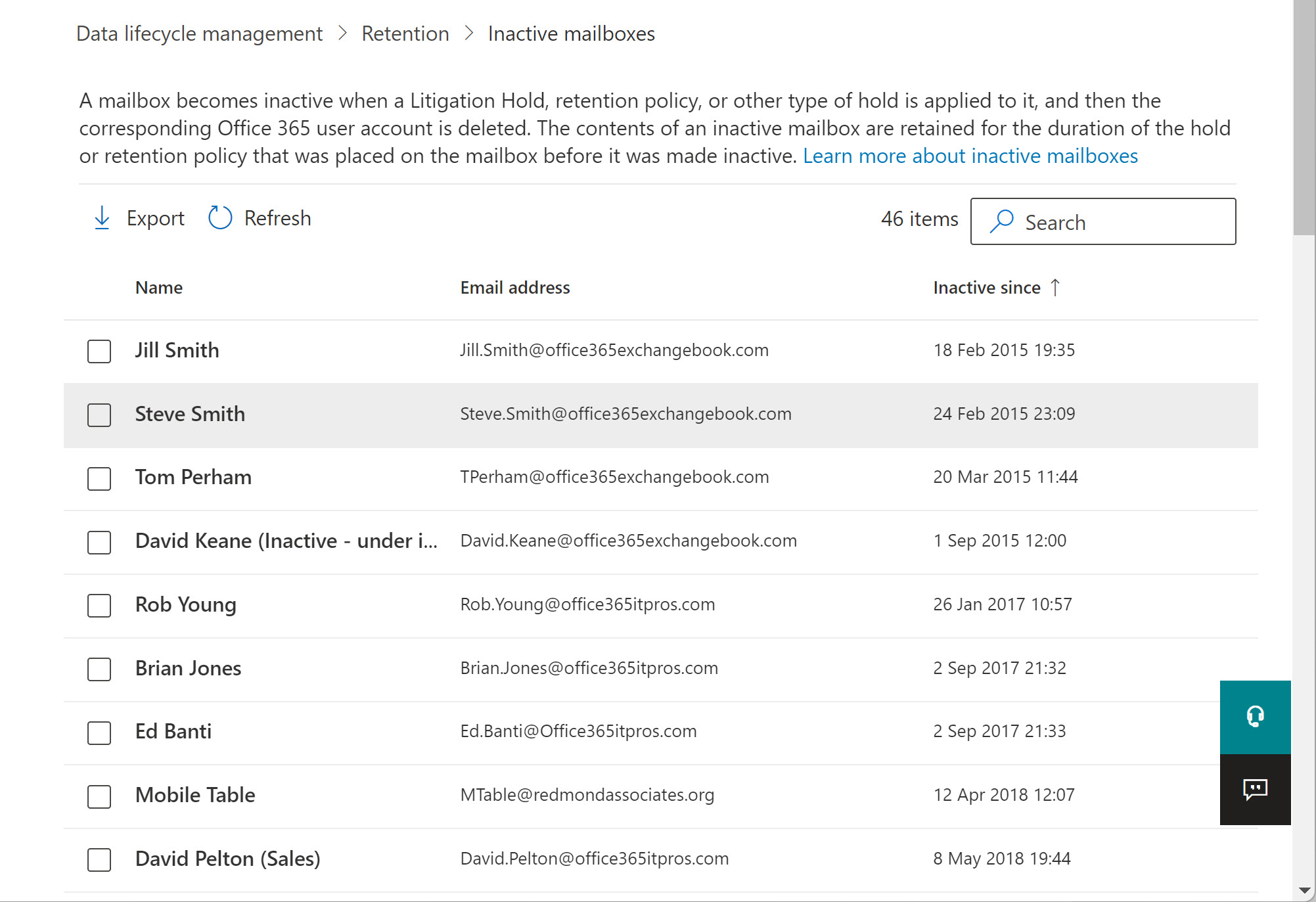
Exchange Online tenants have a choice between inactive mailboxes and shared mailboxes when the need arises to keep “leaver” data like that belonging to ex-employees. Inactive mailboxes are essentially a compliance tool and sometimes shared mailboxes are better choices. We explore both in this short article.
On May 19, Microsoft disclosed that a problem had stopped audit events being generated when people used the Exchange SendAs and SendOnBehalfOf permissions to send email for other mailboxes. Microsoft says that the problem is now fixed, but as it turns out, some issues still exist with capturing audit records for SendAs events.
Microsoft Loop components are available now in Teams chats and will soon become available in OWA. Loop components are a new way of collaborative working that some will find very attractive. However, under the covers, some compliance issues can block organizations from allowing the use of Loop components. This post explains the issues involved in eDiscovery and export of items containing Loop components.
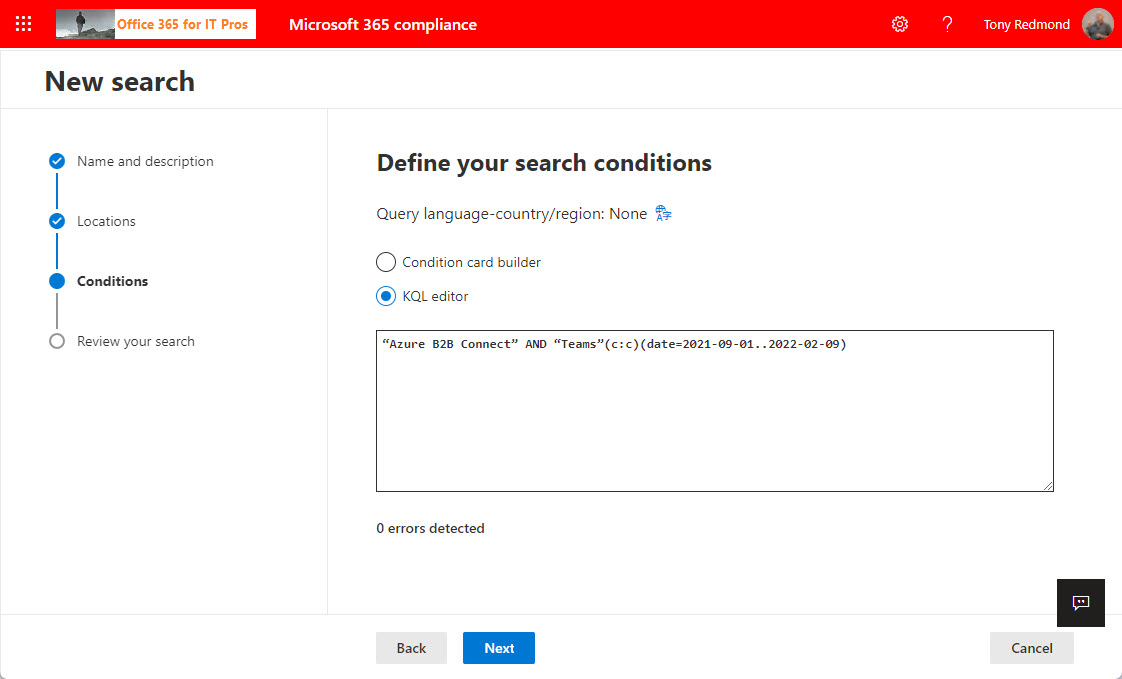
The KQL editor is a relatively new feature in Microsoft 365 that makes it easier to compose queries to find email and documents in content searches, core eDiscovery, and advanced eDiscovery. Although it’s not perfect, the KQL editor helps compliance managers to perfect queries and resolve syntax errors. Human intelligence is still needed to make sure that everything works!
SharePoint Online and OneDrive for Business will soon gain the ability to apply default sensitivity labels to document libraries. The feature is currently in preview and requires some complicated PowerShell to configure, but Microsoft is working on the GUI and expects to make the capability generally available later this year.
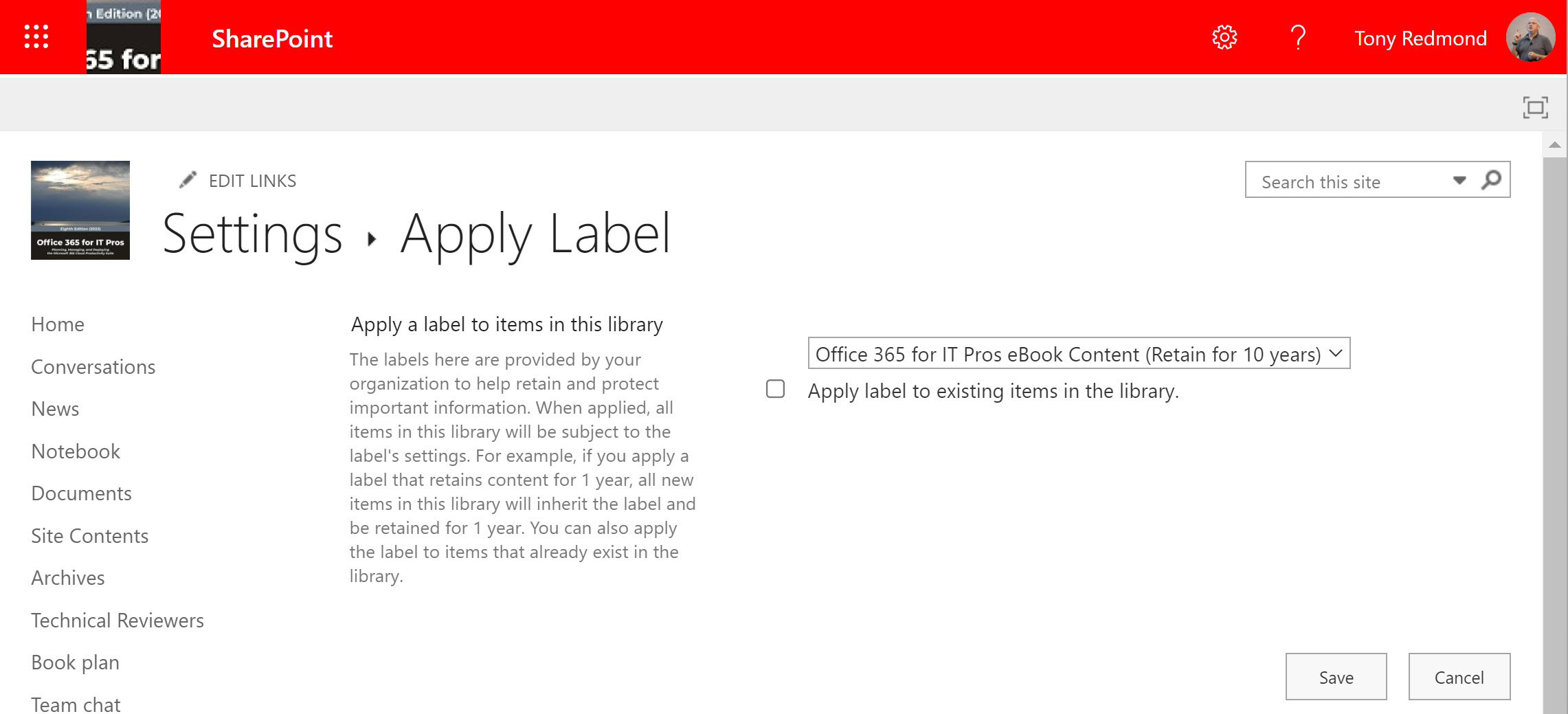
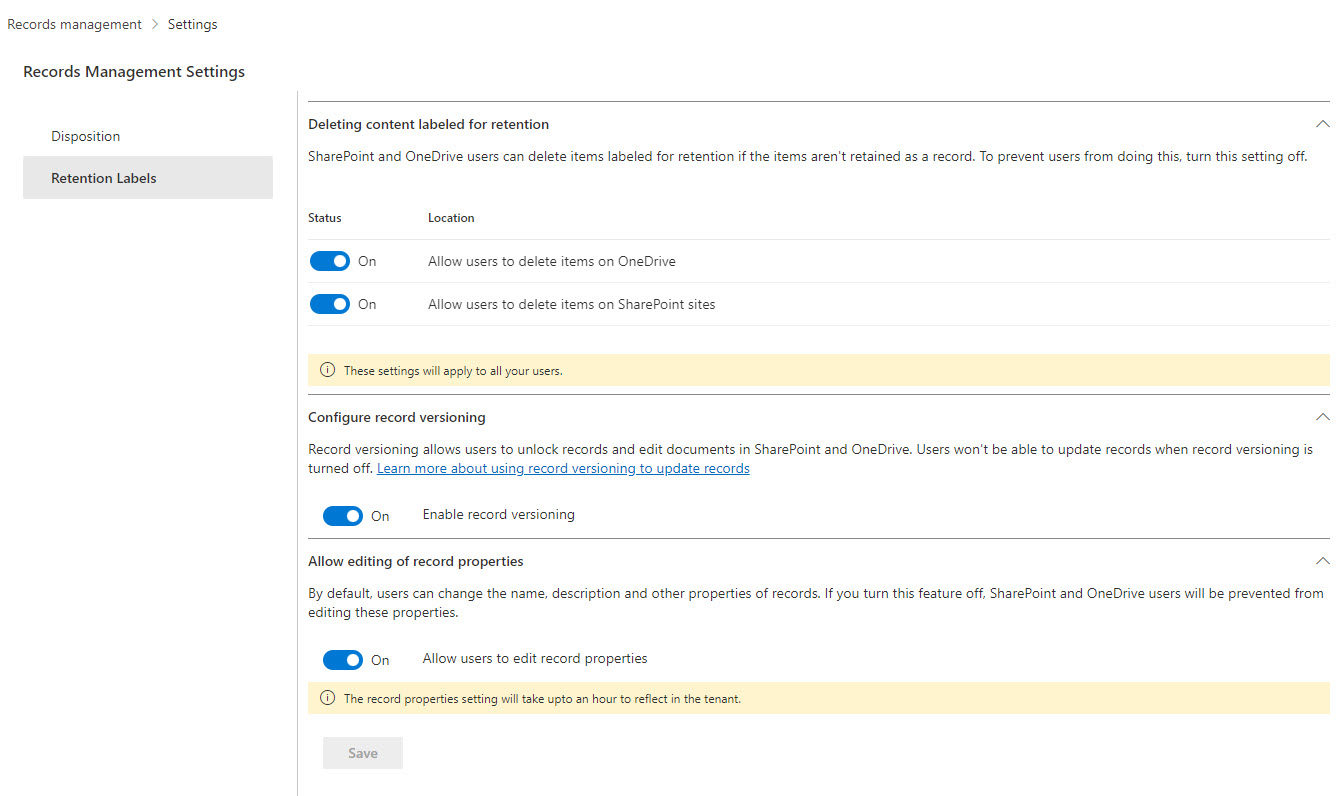
The Records management solution in the Microsoft 365 compliance center has some important controls for retention labels. Two new controls allow organizations to decide if they will allow users to unlock items assigned a record retention label. If they can’t, they won’t be able to update document contents or change an item’s metadata. This won’t suit all organizations, but it will make those which want locked down records management very happy indeed.
Microsoft 365 retention policies allow organizations to keep or remove content from workloads like Exchange Online and SharePoint Online. You can apply filters in retention policies, but Microsoft only supports this capability auto-label retention policies. You can go ahead and update a standard retention policy to add a content filter with PowerShell and the policy will work. The question is, how long will it work for before Microsoft changes something on the backend to stop the policy working?
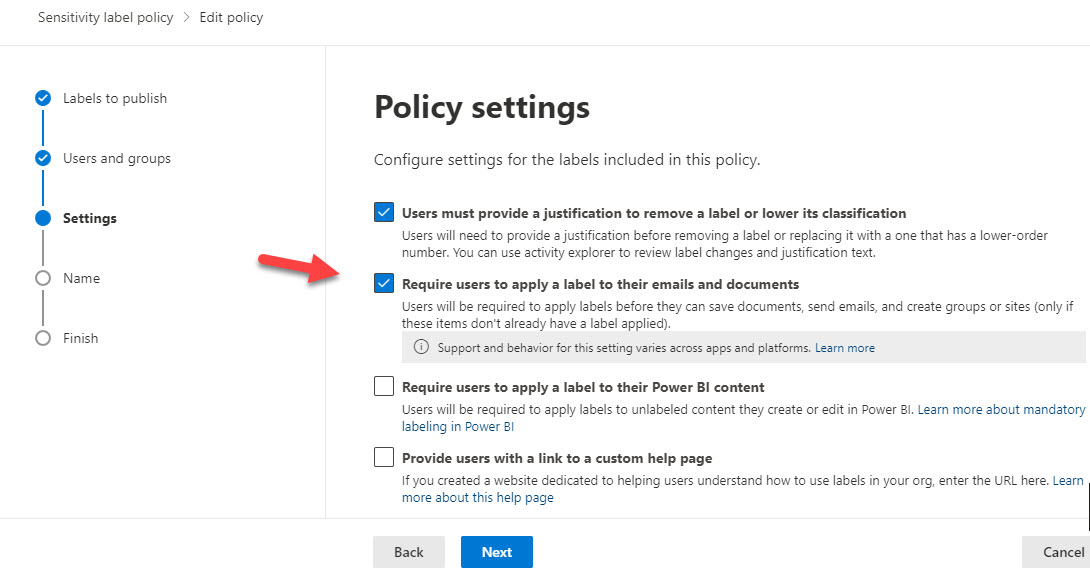
A change in how Office apps apply mandatory labeling as dictated by sensitivity label policies means that both new and old documents are processed. New documents have always been dealt with; the change being made ensures that Office apps detect the lack of a label when opening an existing document and will apply mandatory labeling at that point. It’s a change to help customers move on from the unified labeling client.
The Microsoft 365 audit log holds all kinds of useful data, including events logged for SharePoint Online and OneDrive for Business file deletions. It’s easy to use PowerShell to search the audit log to find and interpret the events and create a report. Large tenants might need to export the audit data on a regular basis to an external repository to allow for long-term retention and analysis. We explain the principles of the process in this article.
New audit events are available to capture information about Teams meetings and participants, but only if you have Office 365 E5 or above licenses. That’s because Microsoft deems these events to be high-value audit information prized by forensic investigators when they try to unravel what happened in an incident. You’ll have to make your own mind up how valuable the events are, but we’ve written some PowerShell to make the data more accessible.