The ability to restore deleted groups only covers Microsoft 365 groups. That’s an odd situation to be in given the different types of groups in Microsoft 365, and the reasons why things work (or don’t) the way they do is down to history and different teams within Microsoft. It’s logical that customers assume they can restore any type of deleted group. Microsoft needs to do some magic to make that assumption real.
A recent report highlighted the problem of on-premises accounts synchronized to Entra ID that receive administrative role assignments. This article explains how to report the administrative role assignments managed by Privileged Identity Management (PIM) or direct role membership so that it’s easy to highlight on-premises accounts holding administrative roles.
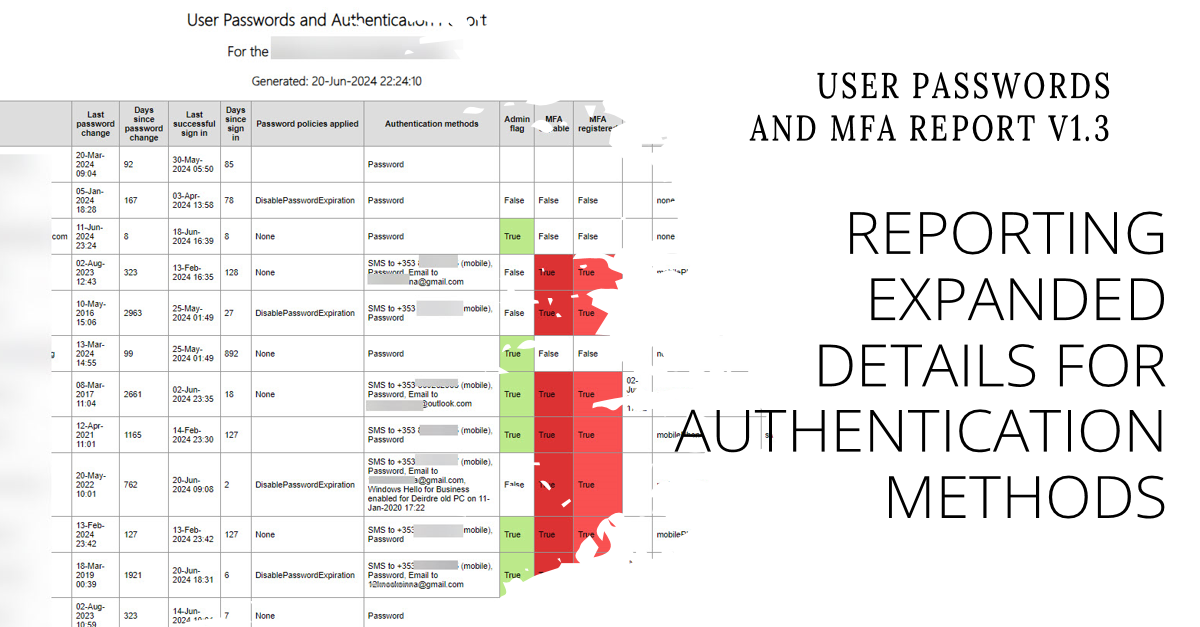
V1.2 of the User Passwords and MFA report includes the names of authentication methods registered for user accounts. V1.3 expands the amount of detail reported for each method, such as the phone number used for SMS challenges, or the email address used for SSPR. It’s a small but important detail that’s useful to administrators. However, it also comes with a potential privacy issue, so the script must handle that too.
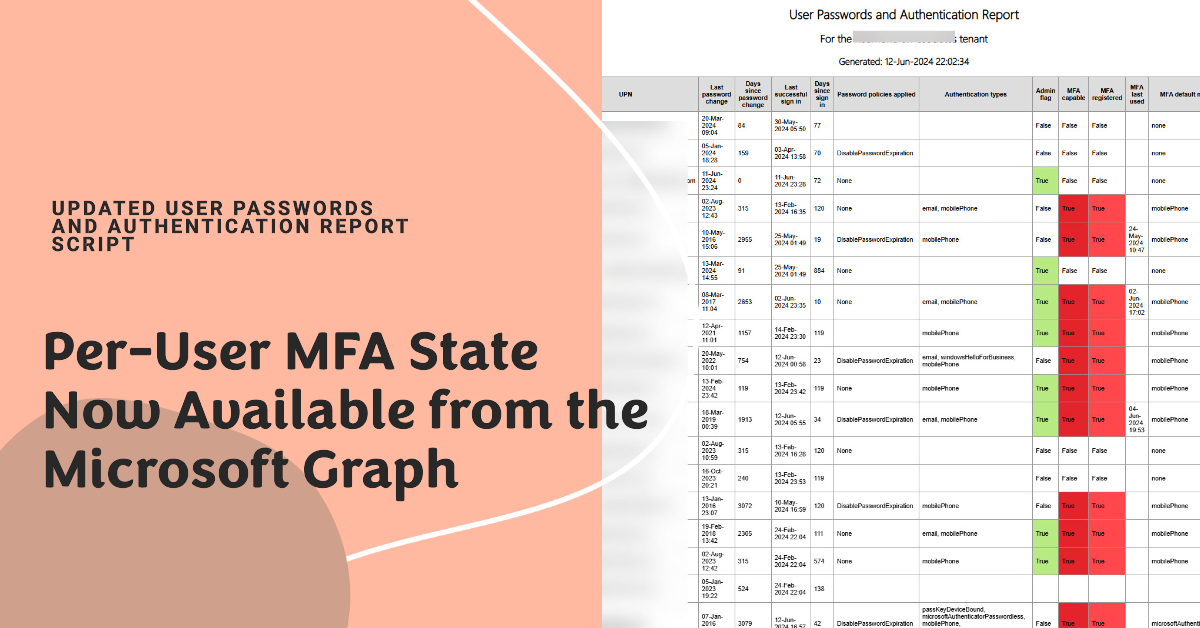
A Microsoft Graph update makes per-user MFA state available for user accounts. Being able to access the data means that we can include it in the User Passwords and Authentication report. You can now see if accounts are disabled, enabled, or enforced for per-user MFA along with all the other information captured about passwqrd changes, MFA authentication methods, and so on.
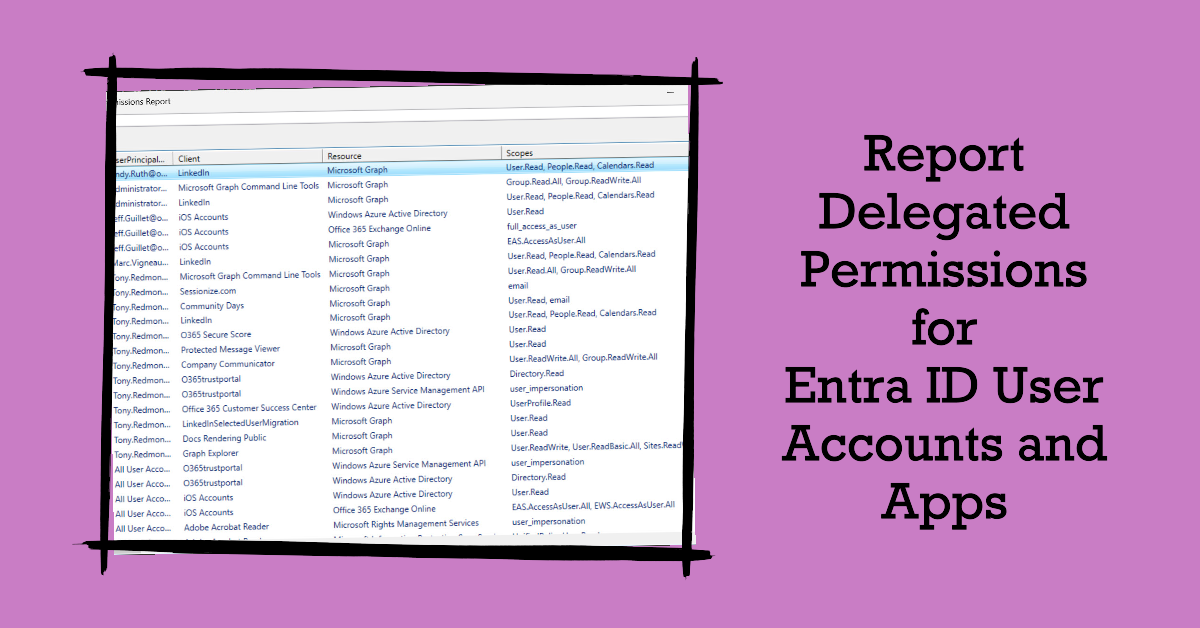
This article describes how to use the Microsoft Graph PowerShell SDK to report delegated permission assignments to user accounts and apps. Like in other parts of Microsoft 365, the tendency exists to accrue delegated permissions for both user accounts and apps over time. There’s nothing wrong with having delegated permissions in place, if they are appropriate and needed – and that’s why we report their existence.
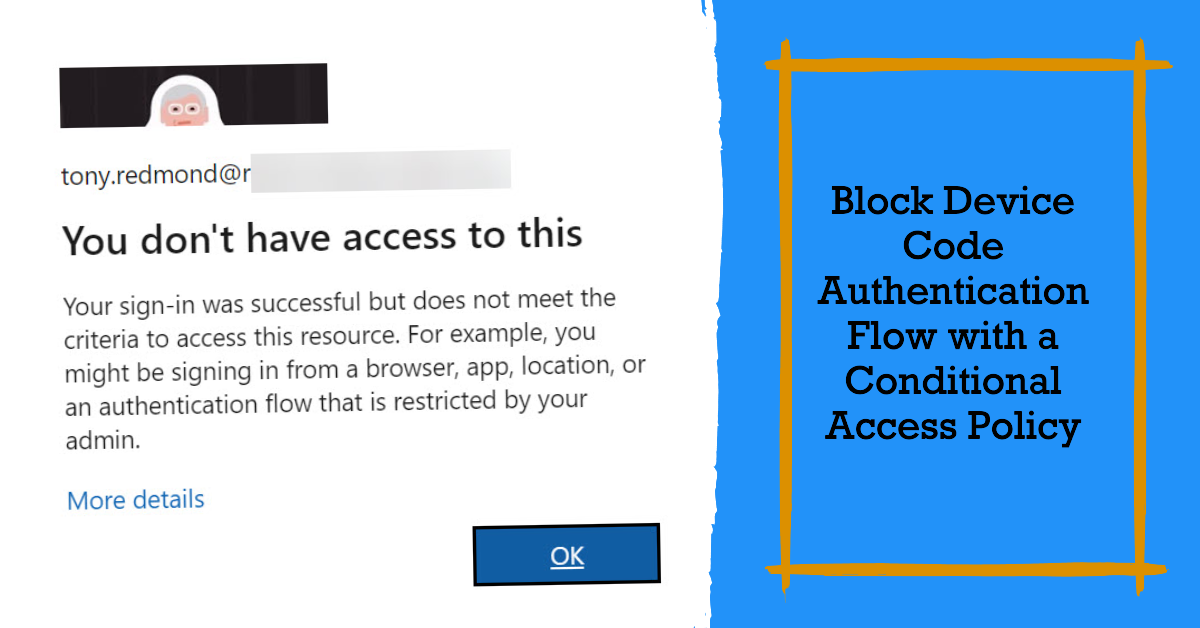
This article describes the process of blocking device code authentication requests against Entra ID with a preview feature for conditional access policies. It’s a good idea to tighten tenant security by removing device code authentication unless a clearly-defined need exists for apps to authenticate using this method. I suspect that most tenants will find that they can happily do without device code authentication.
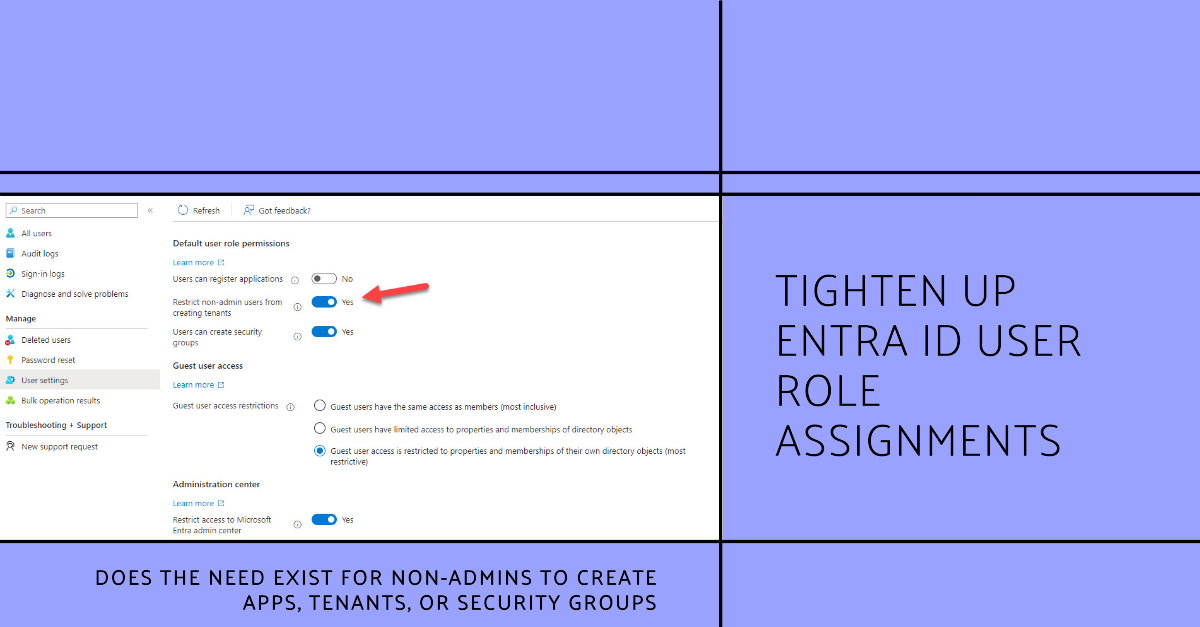
The user authorization policy defines user role permissions, or actions that non-admin users can take within an Entra ID tenant. The default settings are silly. I can’t think of good reasons to allow non-admin users to create new registered apps, tenants, or security groups. Why default settings allow these actions is a mystery, and it could be they’re just outdated.
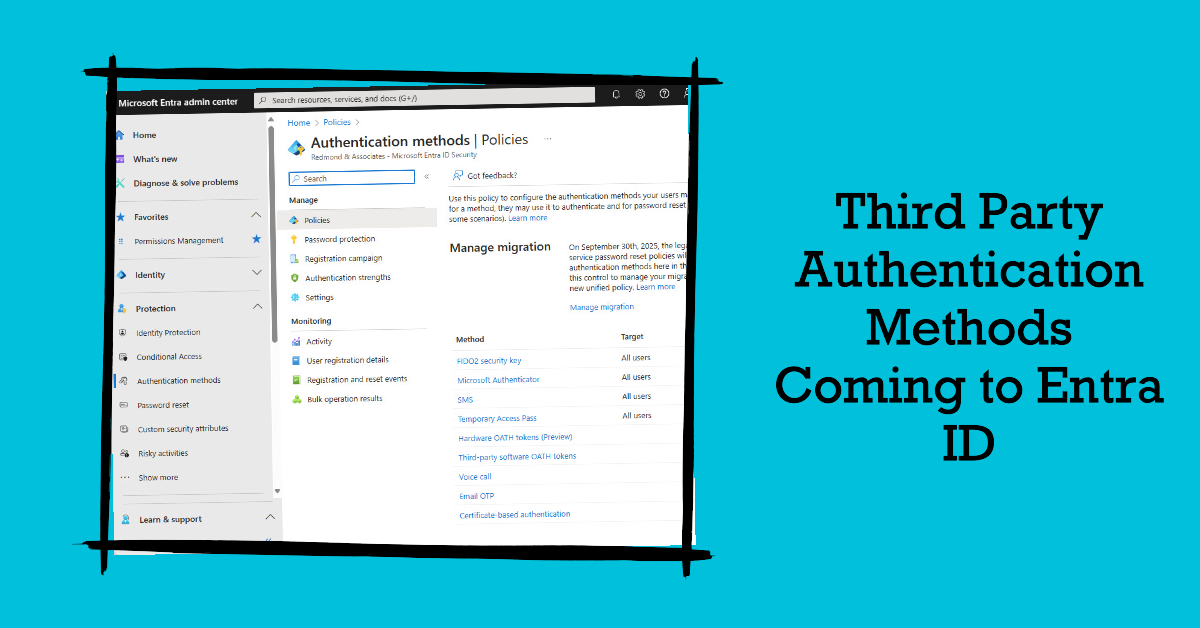
In a May 2 announcement, Microsoft said that they have signed up 9 ISVs to add support for Entra ID authentication methods. The third-party methods work the same way as native Entra ID authentication (like the Authenticator app), meaning that verified connections can be used by other Entra solutions like Privileged Identity Management.
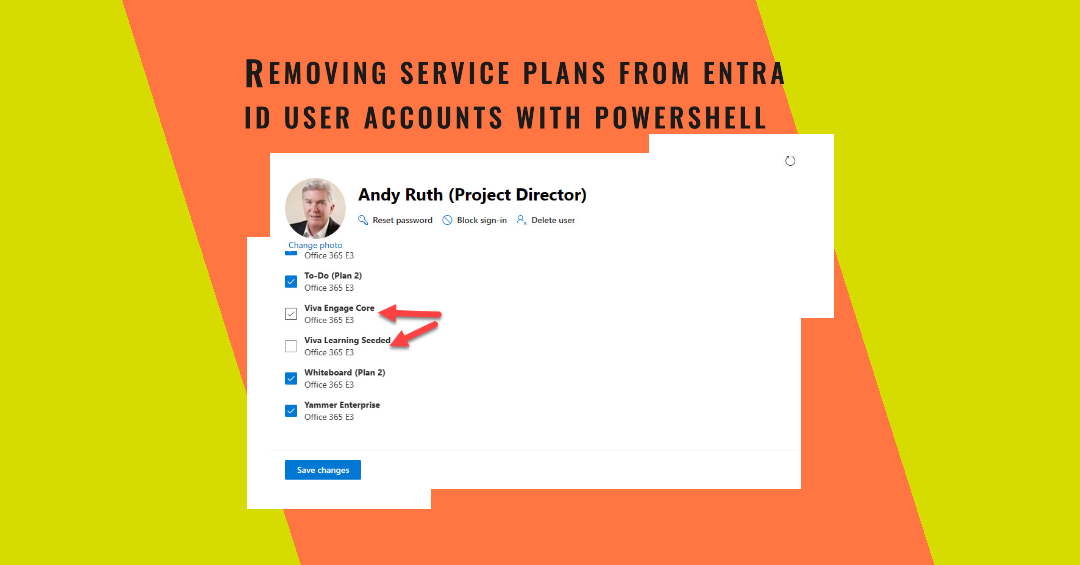
Some years ago, I wrote a script to demonstrate how to remove service plans with PowerShell. This article describes some upgrades to make the script even better by improving the code and leveraging complex Microsoft Graph queries against the license information stored for Entra ID user accounts. It’s PowerShell, so feel free to change the script!
License management is a core competence for Microsoft 365 tenant administrators. This article explains how to use PowerShell to remove licenses from accounts when an equivalent service plan is available from another license. It’s the kind of fix-up operation that tenant administrators need to do on an ongoing basis.
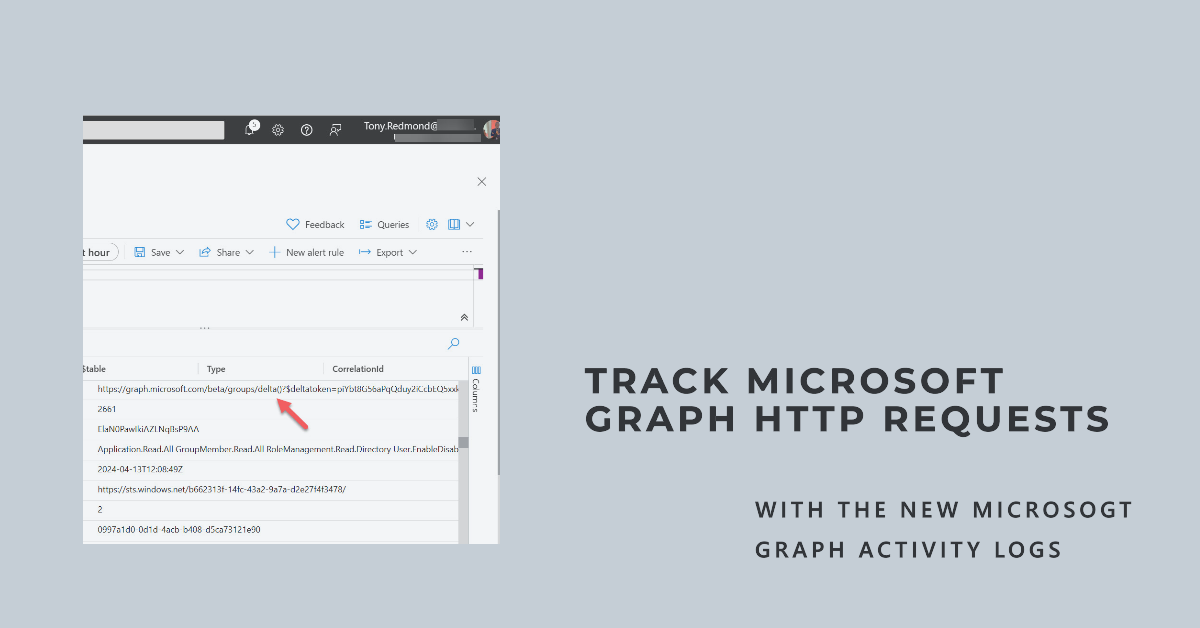
April 11 saw the general availability of Microsoft Graph activity logs, a new set of data recording details of Graph API HTTP requests made in a tenant. The logs are intended to help security analysts understand actions taken by apps in a tenant such as data access or configuration updates. Before working with Graph activity logs, security analysts will need to understand Graph API requests and the context they’re made.
The Maester tool is a community initiative to create a tool to help tenant administrators improve the security of their Entra ID tenants. It’s still in its early stages, but even so Maester shows signs that it will be a valuable asset for administrators who want to learn more about securing their tenant against possible external compromise.
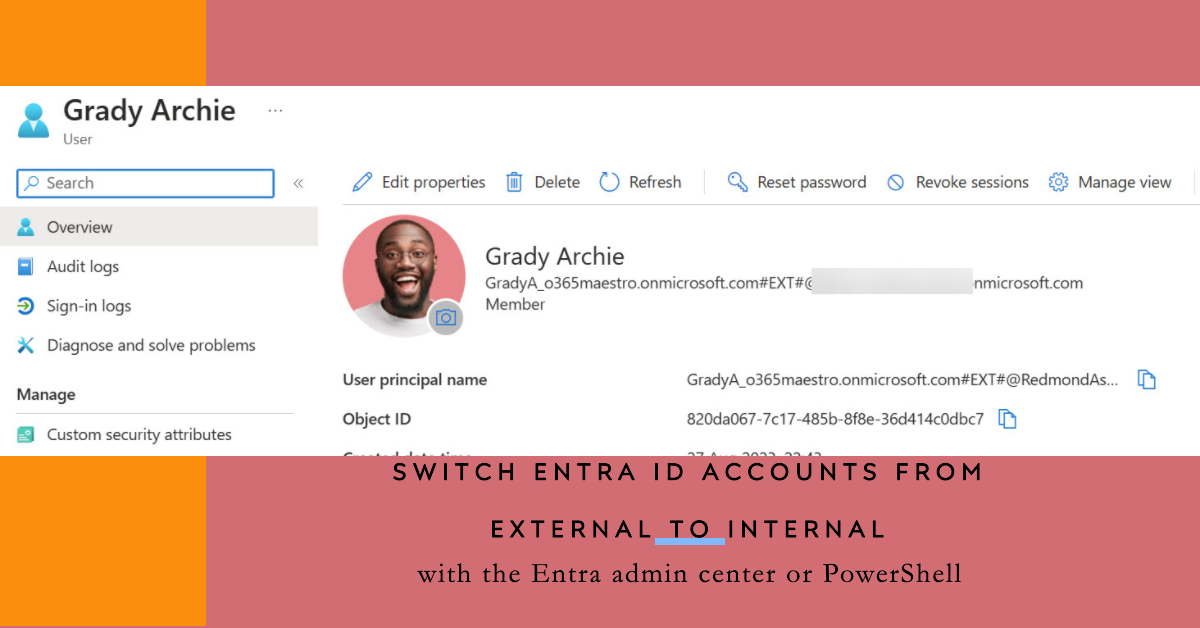
A new convert to internal user preview feature allows Entra ID administrators to convert external accounts to internal accounts. An option is available in the Users section of the Entra admin center or PowerShell can be used to automate the conversion of accounts. It’s a useful feature that should prove popular.
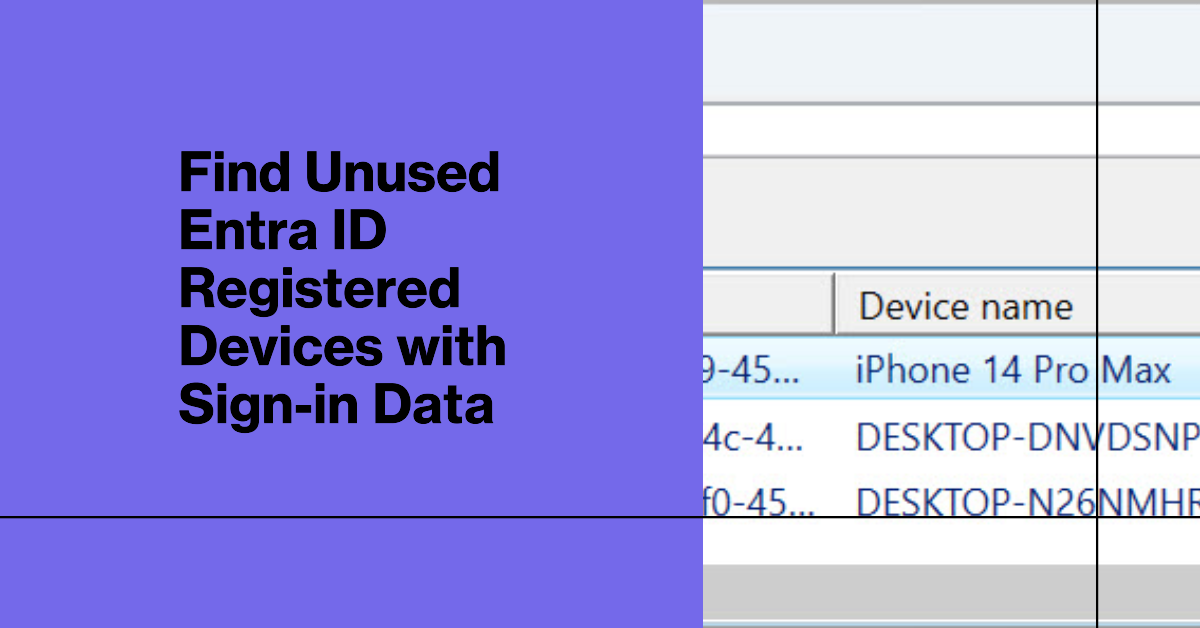
This article describes how to use sign-in data to identify unused Entra ID registered devices. It’s an imperfect solution because Entra ID doesn’t log device information in many sign-in records. I’m sure there’s a good reason why Microsoft doesn’t capture the device information, but it’s a little frustrating. We have an imperfect and partial solution, but that’s better than nothing.
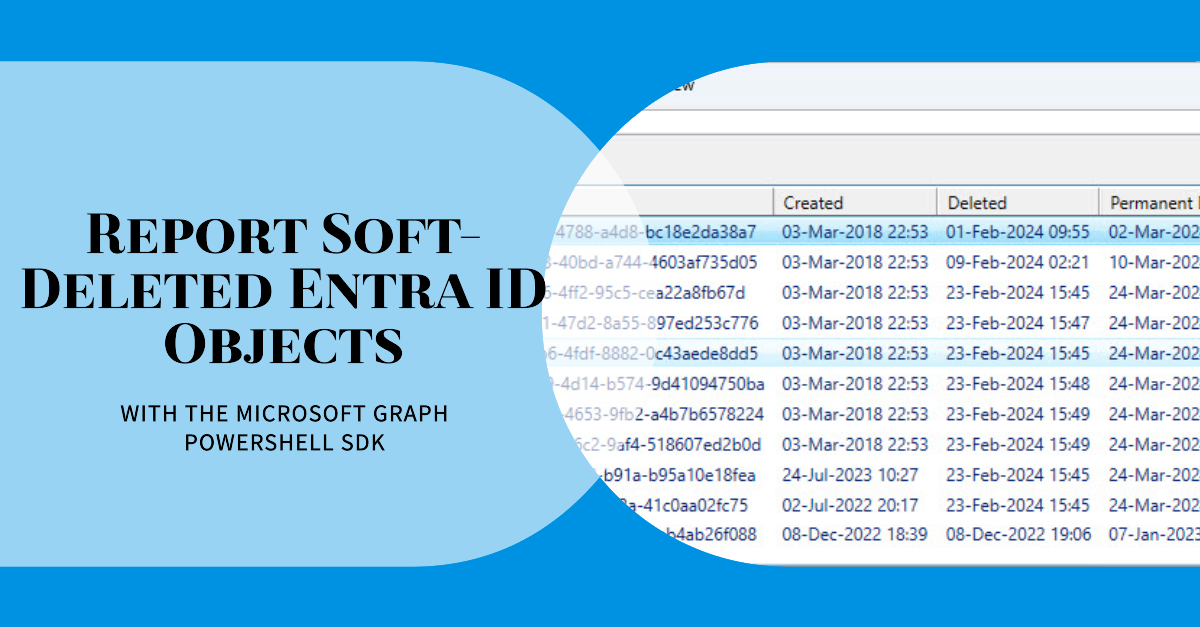
A Microsoft Technical Community article gave some interesting information about how to report soft-deleted Entra ID objects. We think we can improve the information by tweaking the script, especially to include the object type in the output. As always, you can download the script from GitHub.
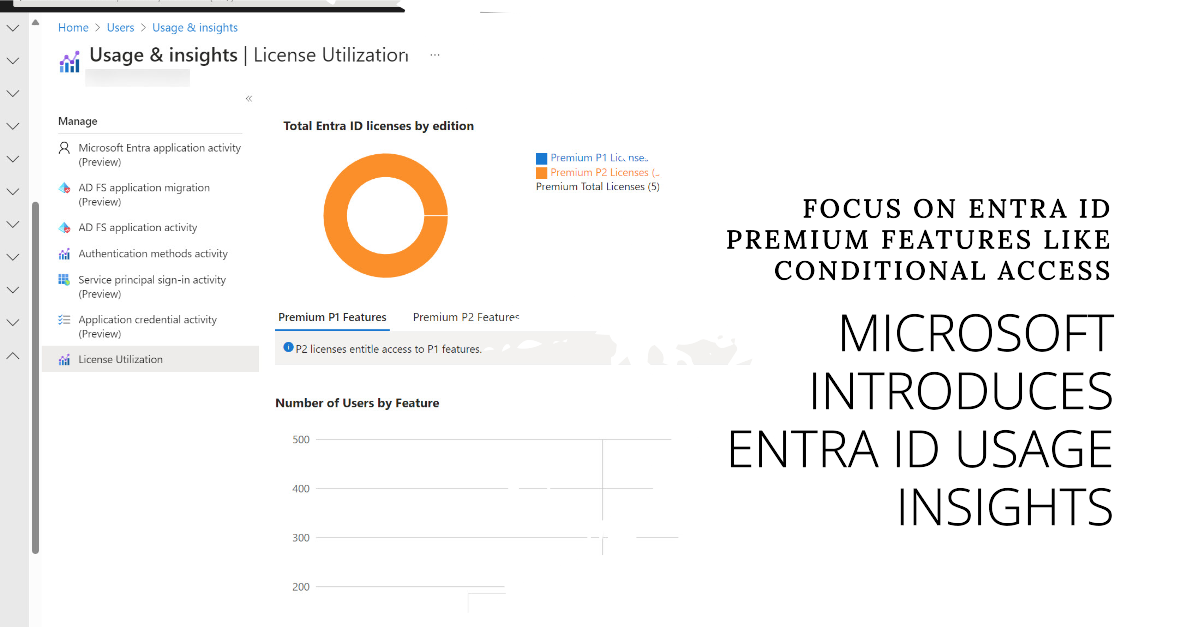
Microsoft has released the preview of the Entra ID usage insights for premium license consumption. This could be the harbinger of a more restricted licensing regime for Entra ID premium features such as conditional access. Putting any barrier in place to stop more accounts being protected by multifactor authentication seems like a bad idea. Let’s hope that this isn’t the case here.
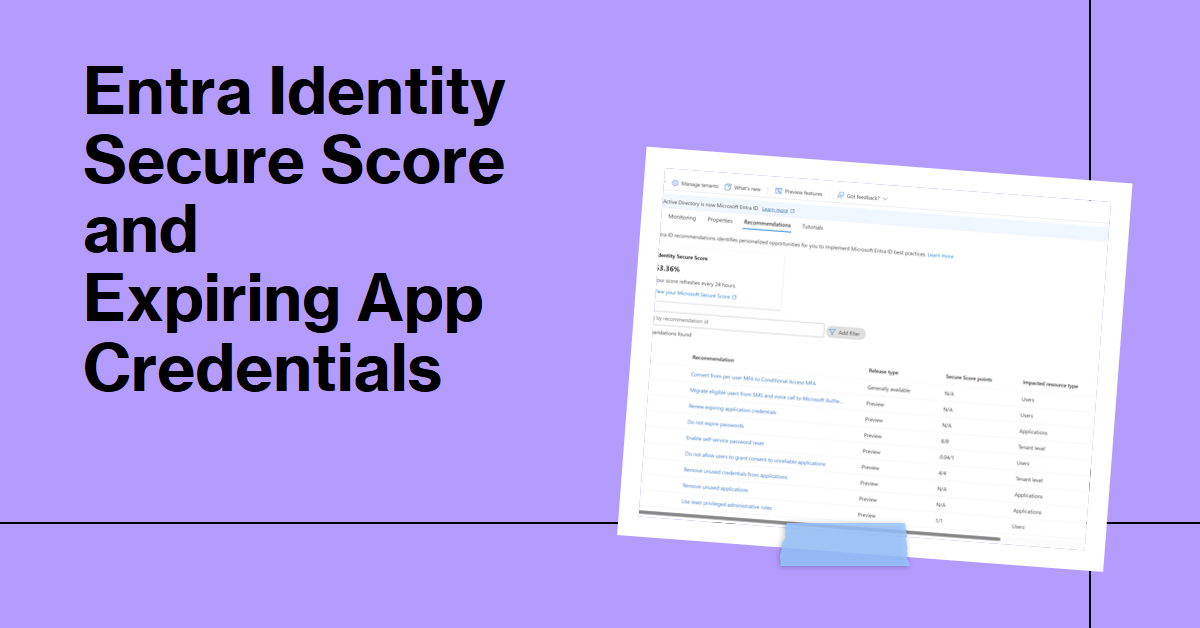
If your Microsoft 365 tenant has Entra P2 licenses, you can use the Entra Identity Secure Score feature to measure your tenant against Microsoft benchmarks and recommendations, including expiring app credentials. The fact that credentials expire is one of the reasons why I don’t use apps as much any more. Using the Microsoft Graph PowerShell SDK is just easier.
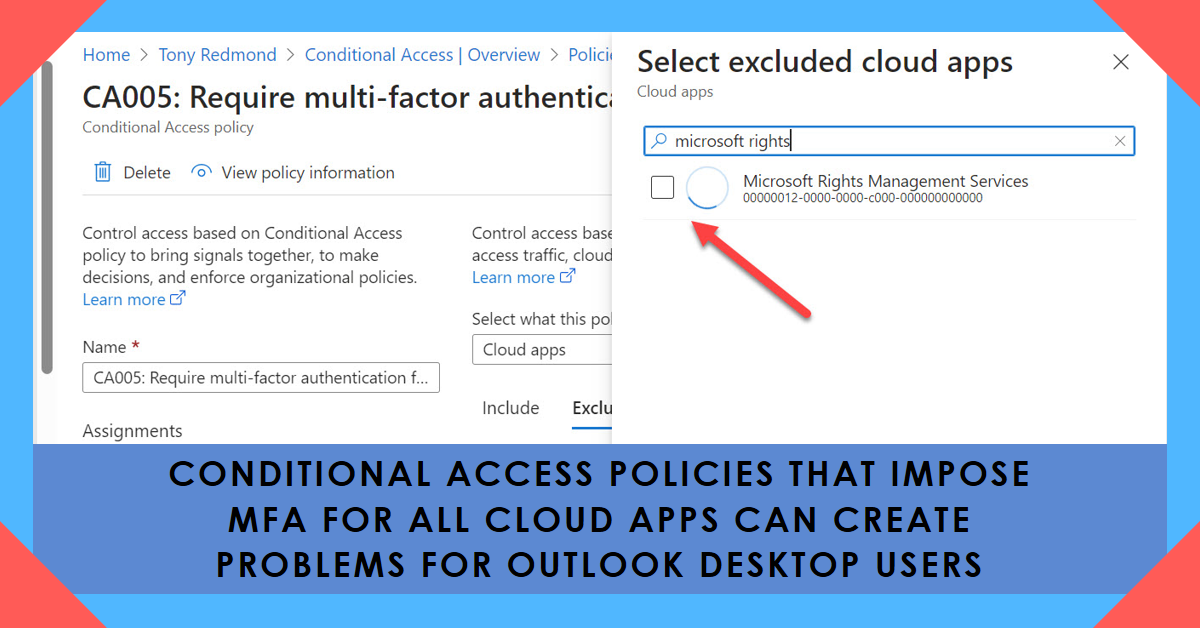
If conditional access policies impose MFA for all cloud apps, it gives external users a problem when they use Outlook desktop to read protected email. The issue is because Outlook can’t obtain a use license to decrypt the content because it can’t satisfy the MFA challenge. It’s an example of how two good parts of the Microsoft 365 ecosystem clash.
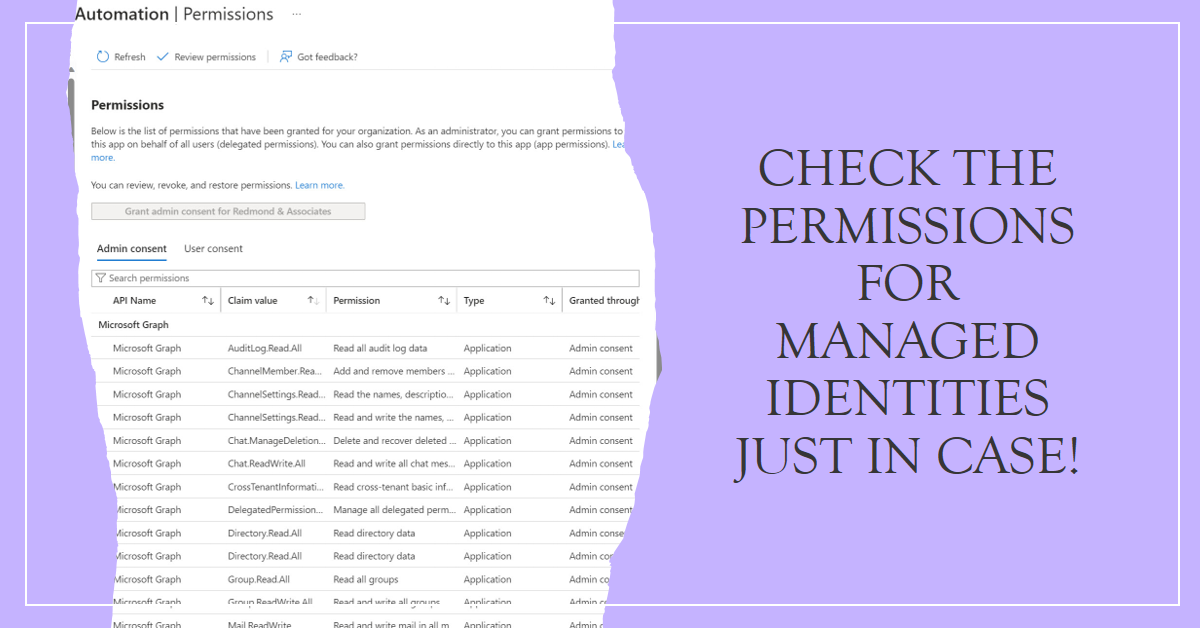
This article explains how to check Managed Identity permissions, or rather the set of consented Graph and other permissions held by the service principals used for managed identities. These can become highly permissioned over time, and that’s why checking periodically is a good idea.
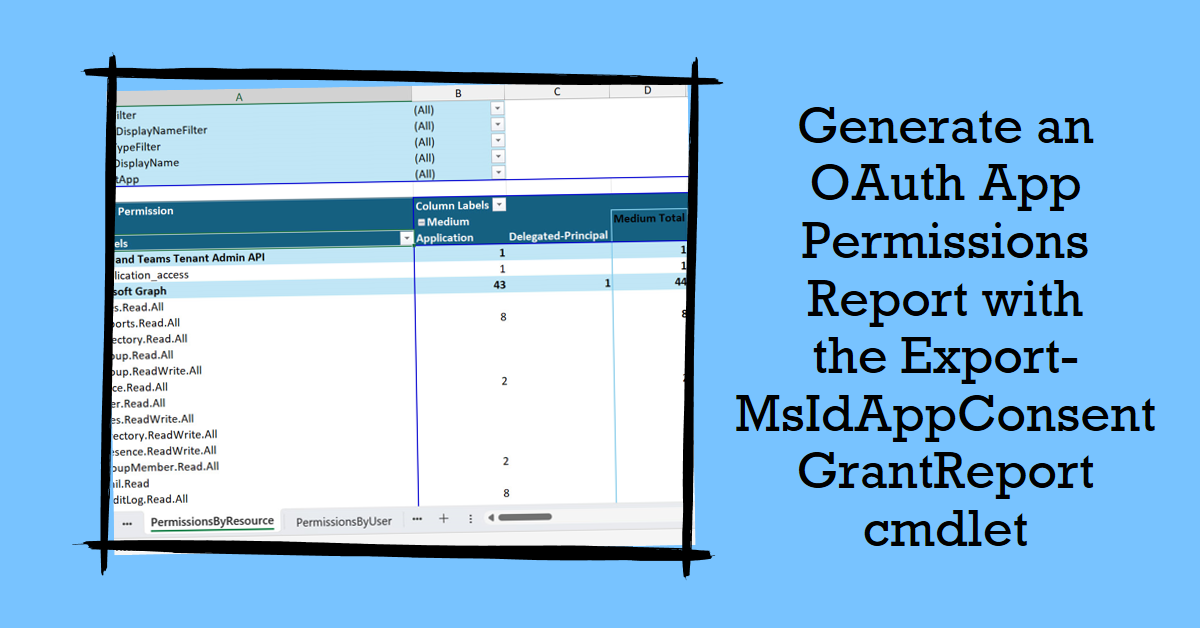
The latest version of the MSIndentityTools PowerShell module includes the Export-MsIdAppConsentGrantReport cmdlet to generate a report of OAuth app permissions. Allied with the ImportExcel module, the cmdlet can produce a very nice workbook containing lots of information about permissions held by the apps in a tenant. But even better, you can export the data to PowerShell and use it in your scripts.
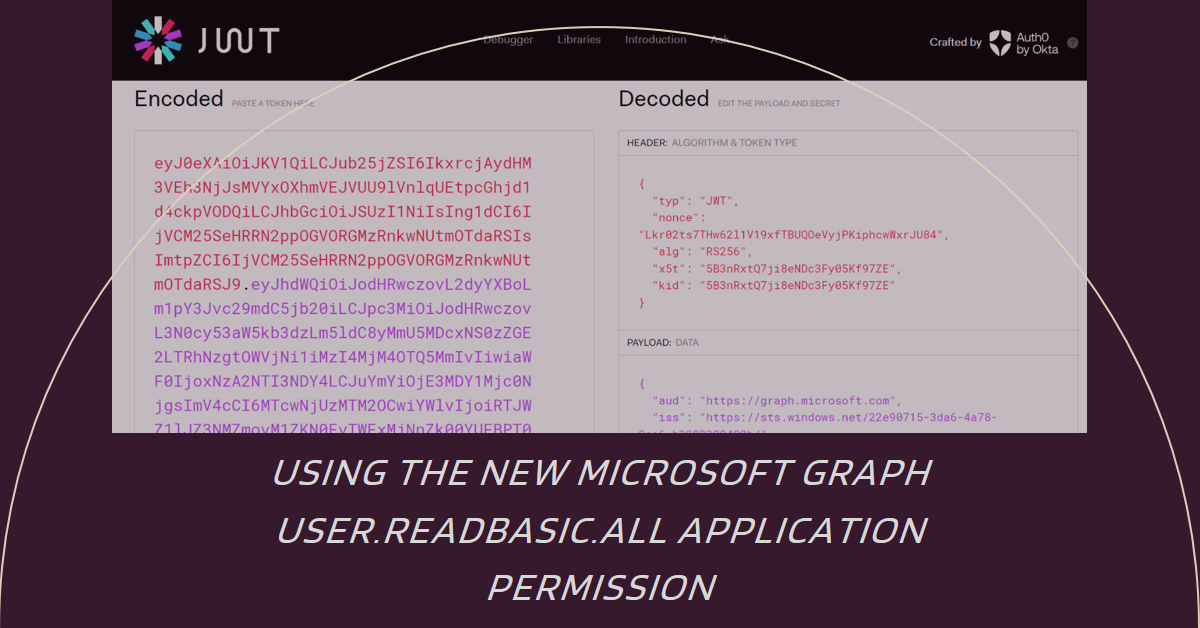
The Graph User.ReadBasic.All permission is now available for both delegated and application usage. Think before rushing to use the permission. Although the permission does what it sets out to do, the restriction on filtering means that many scenarios need the full User.Read.All permission.
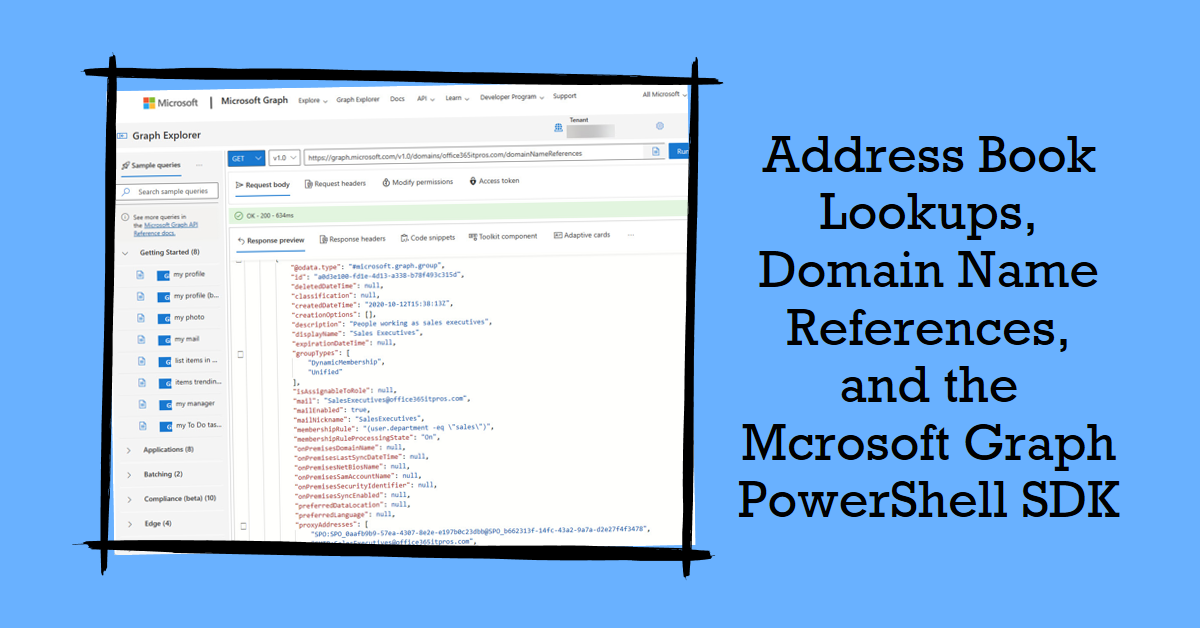
Microsoft is changing the way that Exchange Online address book updates work to force users to use search rather than browsing through the GAL/OAB. That’s fine and should improve things. When playing with finding how many items are in the GAL, I found that the Get-MgDomainNameReference cmdlet appears to have some issues. First, it can only return up to 999 items, which isn’t a lot when you’re dealing with users and groups that have a connection to a domain. Second, it doesn’t return a nextlink, so you can never fetch all available items. It just goes to prove that Microsoft Graph PowerShell SDK cmdlets are at the mercy of the underlying APIs.
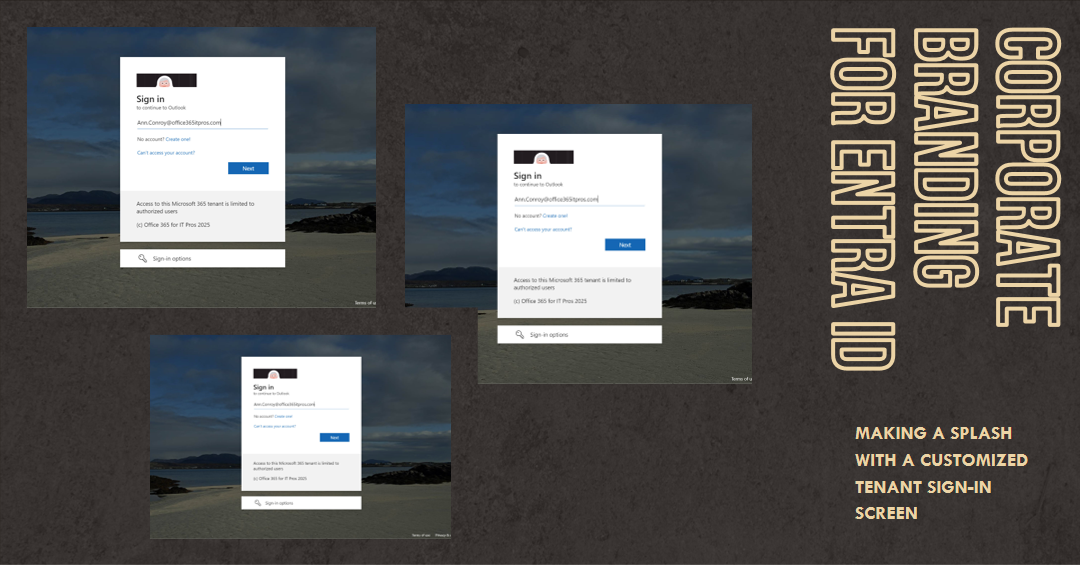
The ability to apply custom corporate branding for Entra Id screens has existed since 2020. You can update elements through the admin center or PowerShell. This article explains how to use the Microsoft Graph PowerShell SDK to customize the sign-in text and background image for the sign-in screen.
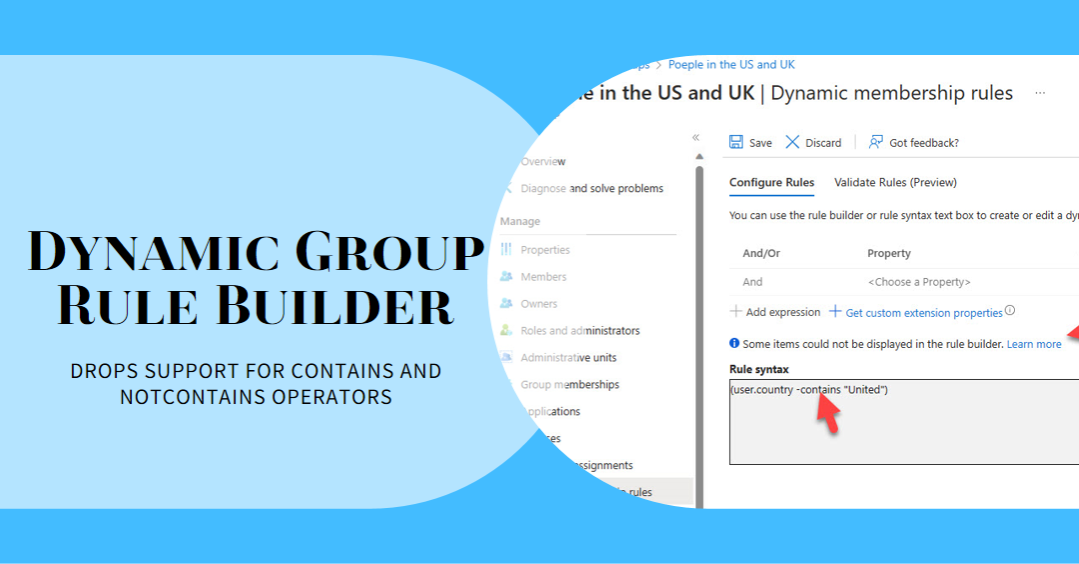
MC705357 (9 Jan 2024) says that the dynamic group rule builder in the Entra ID and Intune admin centers no longer supports the contains and notContains operators. There’s no real cause to worry because existing rules continue to work and if you need to use contains or notContains in a membership rule, you can edit the rule manually.
Entra ID registered apps can authenticate using app secrets and certificates. These credentials expire over time, so it’s good to review app credential expiration dates periodically. This article explains how to use the Microsoft Graph PowerShell SDK to generate a report about app credential expiration dates to allow tenant administrators to manage registered apps a little better…
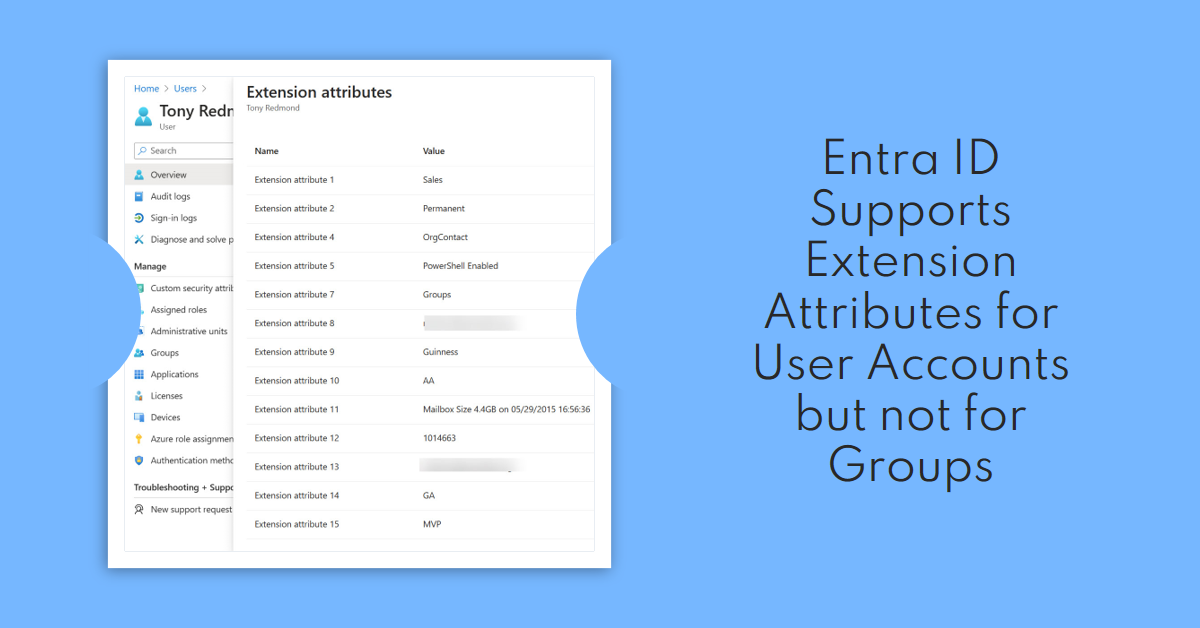
Entra ID supports user extension attributes but the same facility is unavailable for group objects. That seems strange, but it might be due to the way that Entra ID thinks about group object. In any case, it’s an inconsistency that Microsoft should address. Also covered is how to report problems with Graph SDK cmdlets and a new function to help you understand the permissions needed to run a script.
Password profiles store the password settings for Entra ID user accounts. By updating the password profile, you can update an account’s password and force actions like force the user to change their password on the next sign-in or force the user to enable multifactor authentication for the account. All done with cmdlets from the Microsoft Graph PowerShell SDK.
A question came in about how to report admin consent requests as viewed through the Entra ID admin center. PowerShell does the trick, once you know how. The key thing is to find the right cmdlet to use. Once you know that, the rest is pretty easy as we explain in this article.
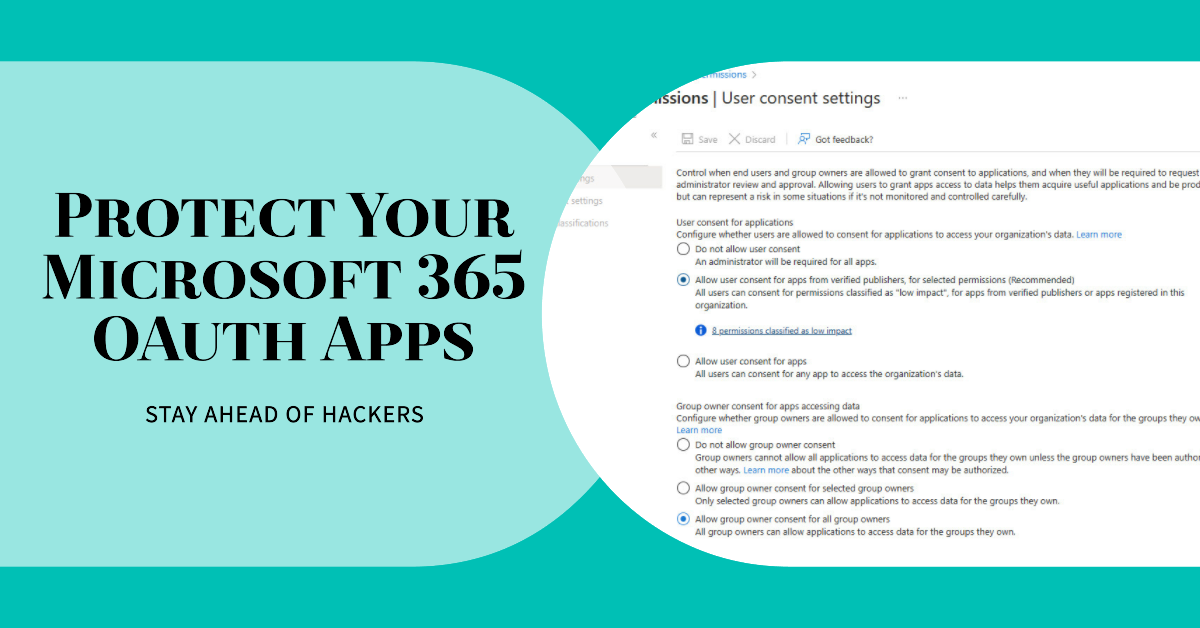
OAuth apps are a big part of the extensibility picture for Microsoft 365 tenants. As such, they are targeted by attackers as a good way to gain access to data. In a recent security blog, Microsoft recommends some steps to secure tenants. We’ve covered most of them in other articles, but it’s always good to pull the story together and rewrite a script to make it easier to report consent grants for apps.
The preview app instance property lock feature designed to improve the security of Entra ID registered apps is becoming the default for new apps. In this article, we describe how to update the app instance property lock to reflect the new default setting using cmdlets from the Microsoft Graph PowerShell SDK, including a script you can download and run.
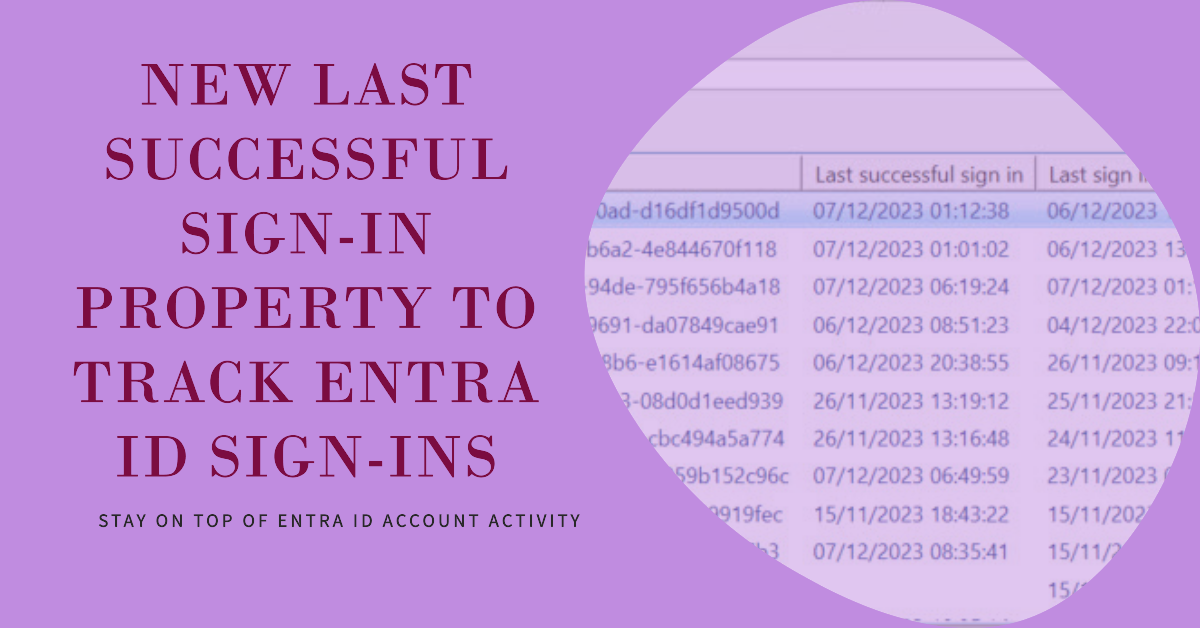
Entra ID captures the lastSuccessfulSignInDateTime property to record the last successful sign-in action against user accounts. The new property is available through the Graph beta endpoint. Quite a difference can exist between the last successful sign in and the last sign in, as explored in this article.
Conditional access policies control access to Entra ID connections. Policies should have exclusions for breakglass accounts, but sometimes this doesn’t happen. This article explains how to use cmdlets from the Microsoft Graph PowerShell SDK to check conditional access policies and update policies with exclusions where necessary.
A year ago, I wrote about the ability to pause membership processing for dynamic Entra ID groups. Now we return to consider the reasons for pausing processing. Mostly suitable circumstances occur when the directory is in a state of flux, often caused by corporate restructuring or similar scenarios. When this happens, you can pause processing for all dynamic groups and restart once the directory stabilizes.
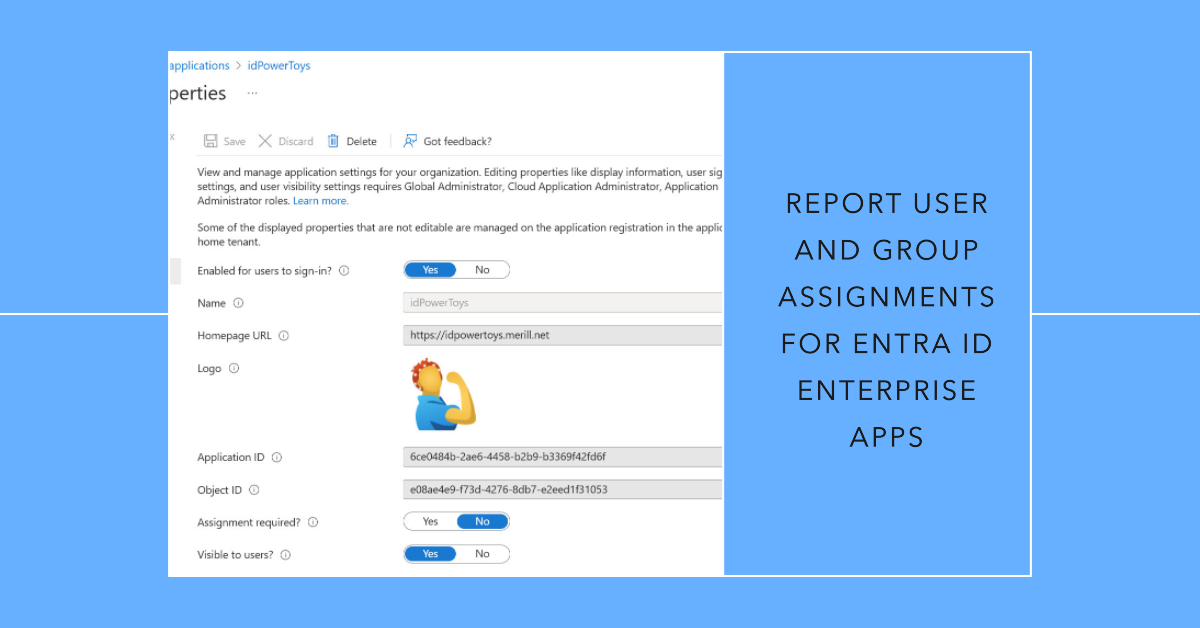
A reader asked how to report user and group assignments for enterprise apps. As it turns out, this isn’t particularly difficult, if you know where to look. Our script uses the Graph SDK to check service principals, filters out the apps to check, and extracts the user and group assignments before reporting what it finds.
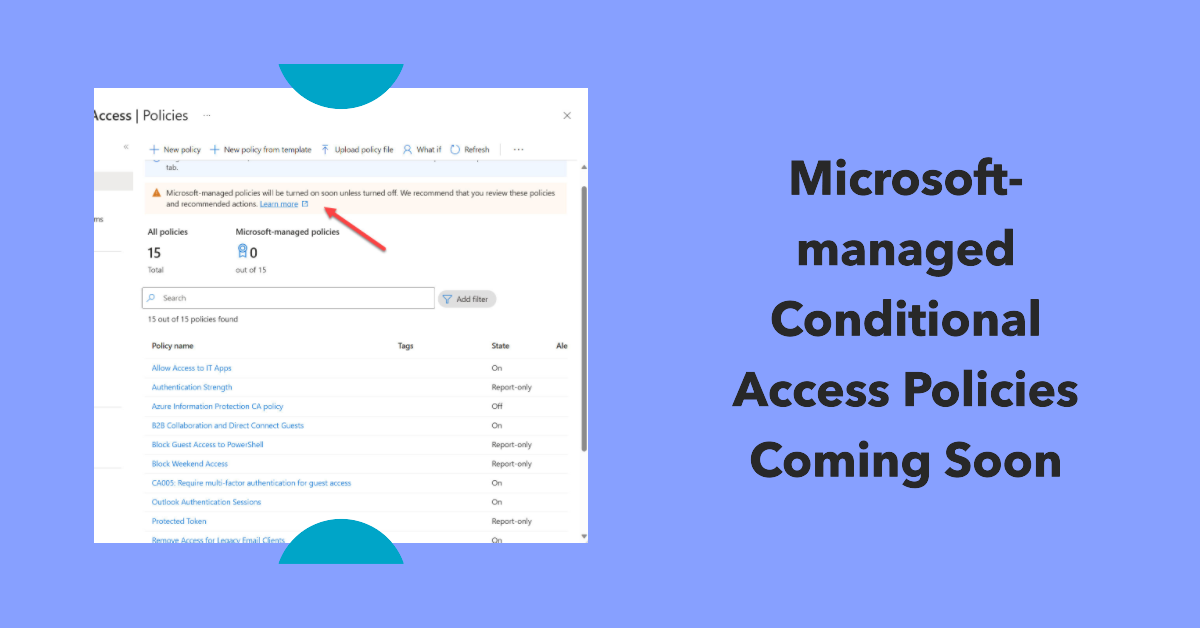
On November 6, Microsoft announced that they will deploy Microsoft-managed conditional access policies to eligible tenants. A conditional access policy controls the connections users want to make to apps or data by setting conditions. In this case, the Microsoft policies will require MFA before access is granted to apps like administrative portals.
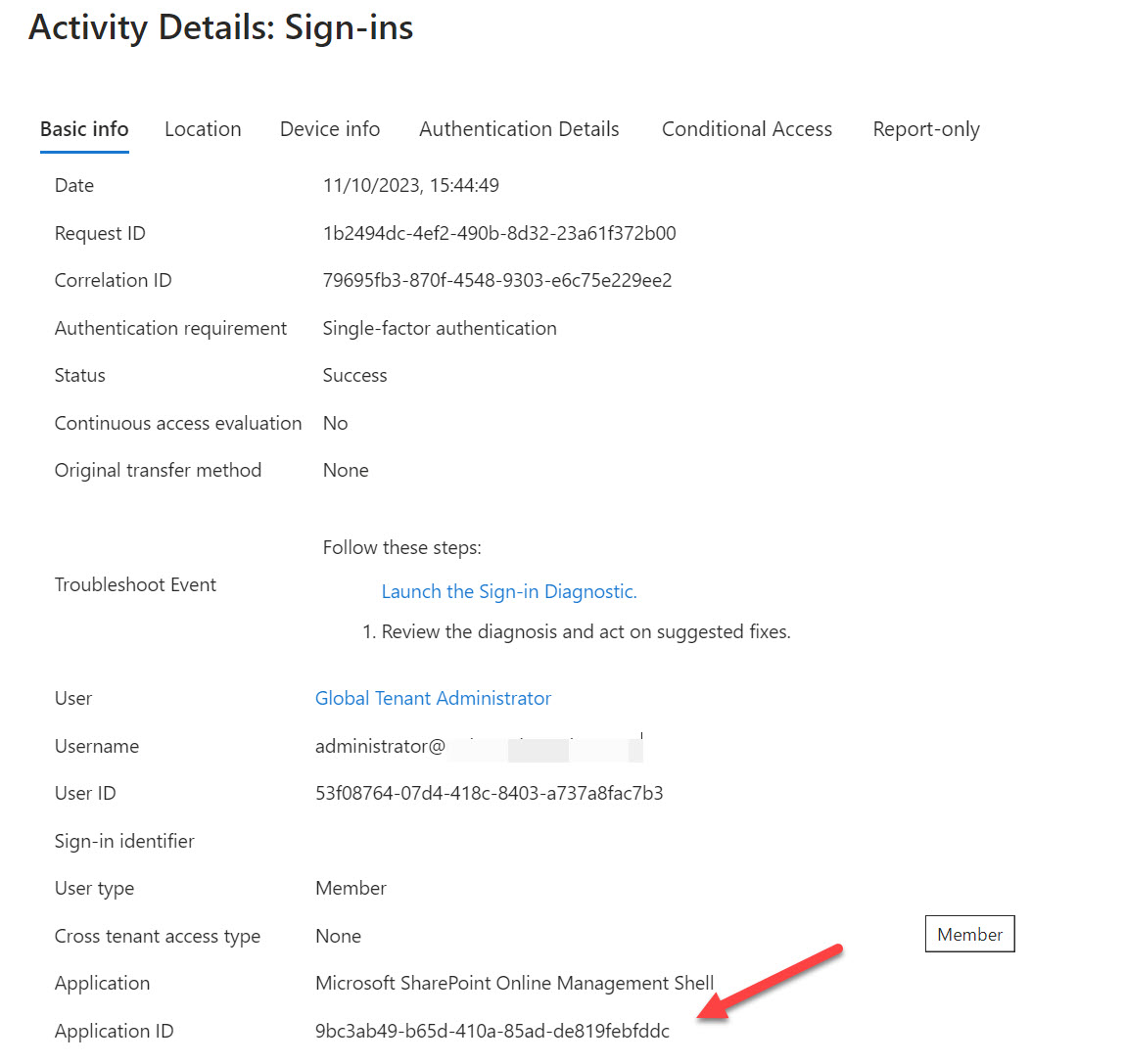
The question of how best to block PowerShell access for Microsoft 365 user accounts deserved some consideration. The answer lies in service principals for the enterprise accounts created by Microsoft to allow PowerShell modules to authenticate with Entra ID. By restricting access to an assigned security group, you effectively block access to anyone outside that group.
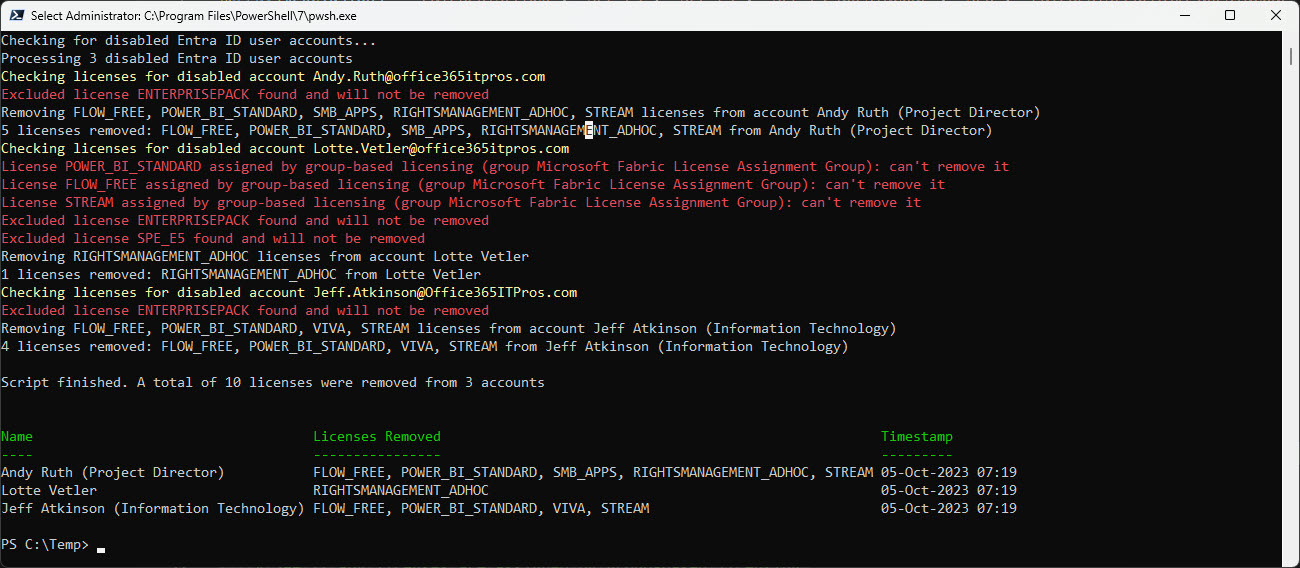
This article explains how to use PowerShell to remove licenses from disabled accounts, including some caveats such as not removing Exchange Online licenses. Organizations might want to do this to save money on Microsoft 365 license fees while an account is temporarily unused. Removal of Exchange Online licenses can result in the loss of a mailbox, and you don’t want that to happen if you’re disabling accounts just because someone is on a long-term sabbatical or other leave of absence.
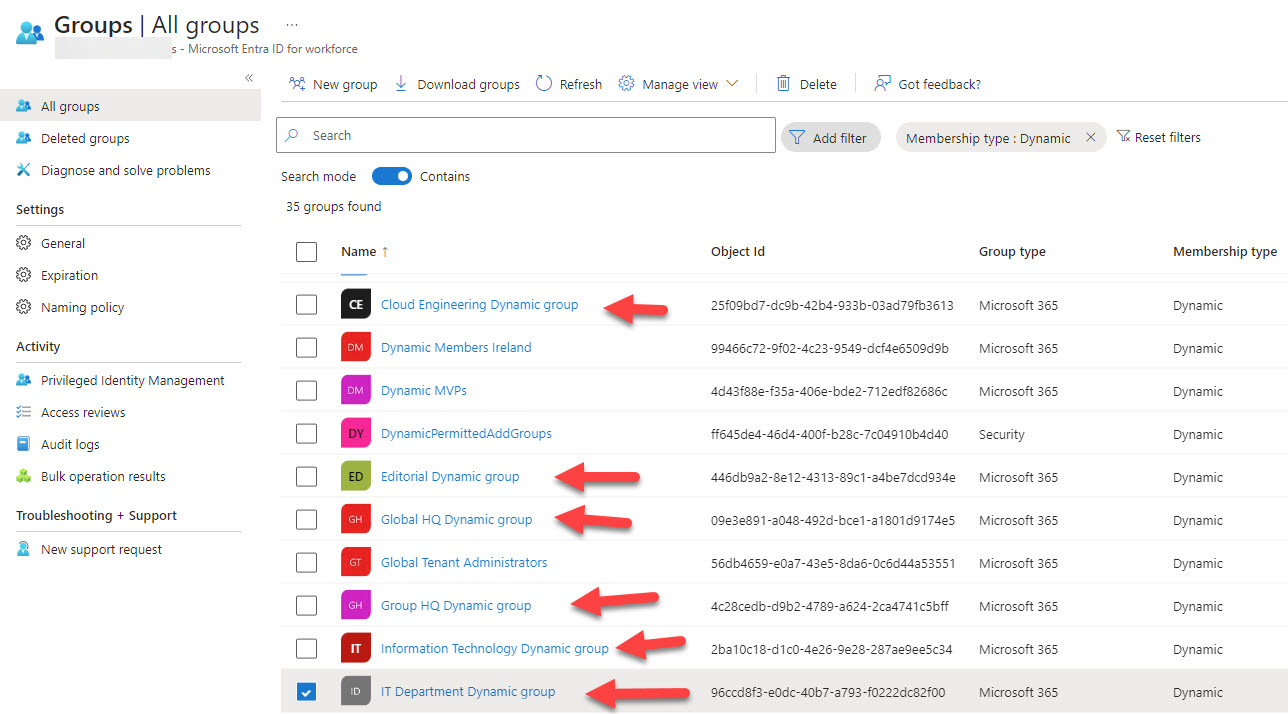
This article explains how to use PowerShell to create dynamic Microsoft 365 groups (and teams) based on the departments assigned to Entra ID user accounts. Creating a new group is easy. The trick in team-enablement is to wait for the synchronization between Entra ID and Teams to finish before you go ahead. After that, it’s plain sailing.
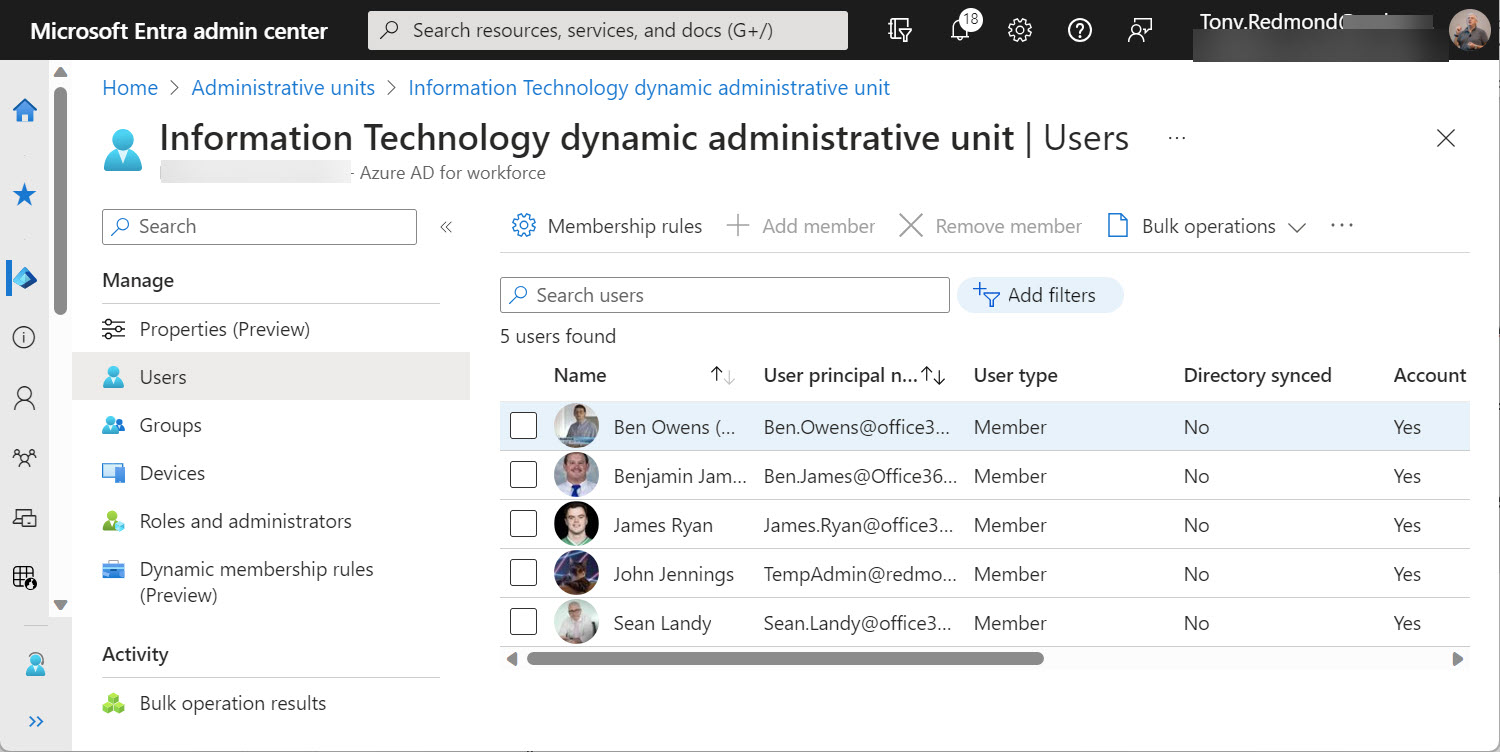
A reader asked how they could create dynamic administrative units for every department in their directory. A PowerShell script does the job, even if some constraints in how Entra ID processes membership rules means that the rules can’t be quite as precise as I would like them to be.
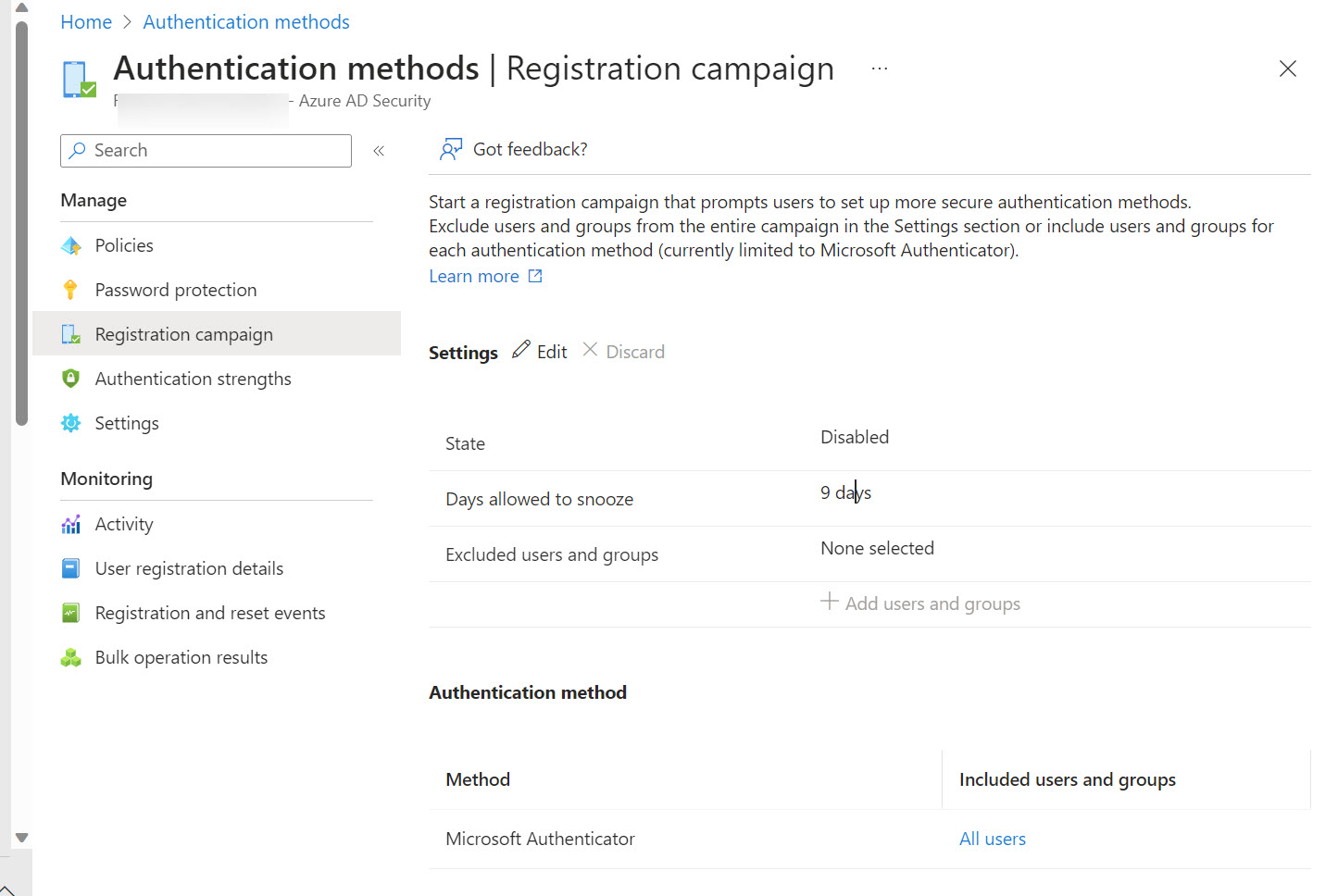
Entra ID includes a registration campaign feature to help organizations move users to stronger authentication methods like the Authenticator app. Running campaigns is a good thing, unless you decide to do it when the administrators are away from the office (like me) or users are unprepared. But it is time to get rid of SMS and voice responses to MFA challenges, so maybe you should schedule a campaign soon?