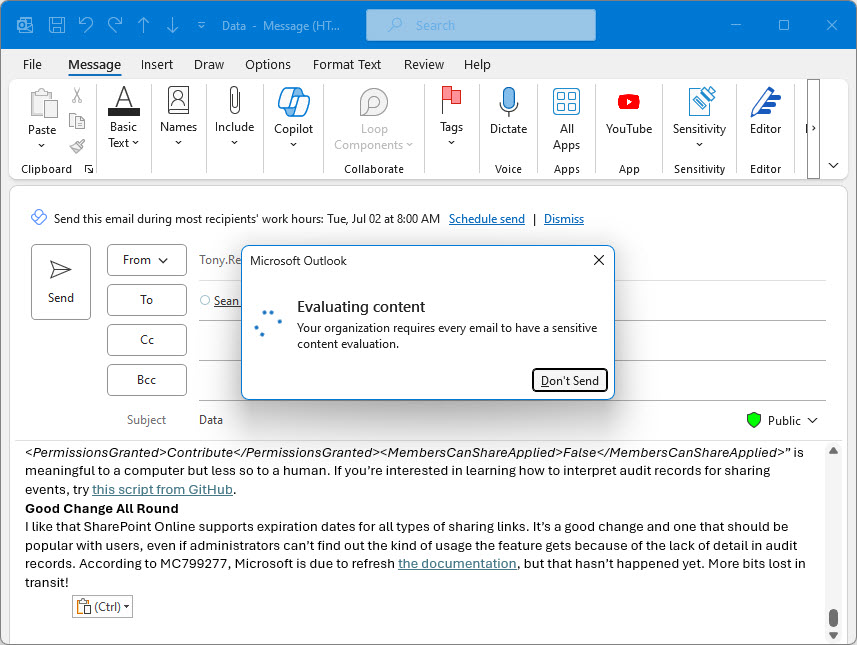
A cloud policy setting enables a delay for evaluating message content and allows Outlook DLP Policy Tips to be displayed after detection of a policy violation. The setting works by pausing message sends until Outlook has had time to check the content for DLP policy violations Pop-up messages inform users about the pause and the result of the check.
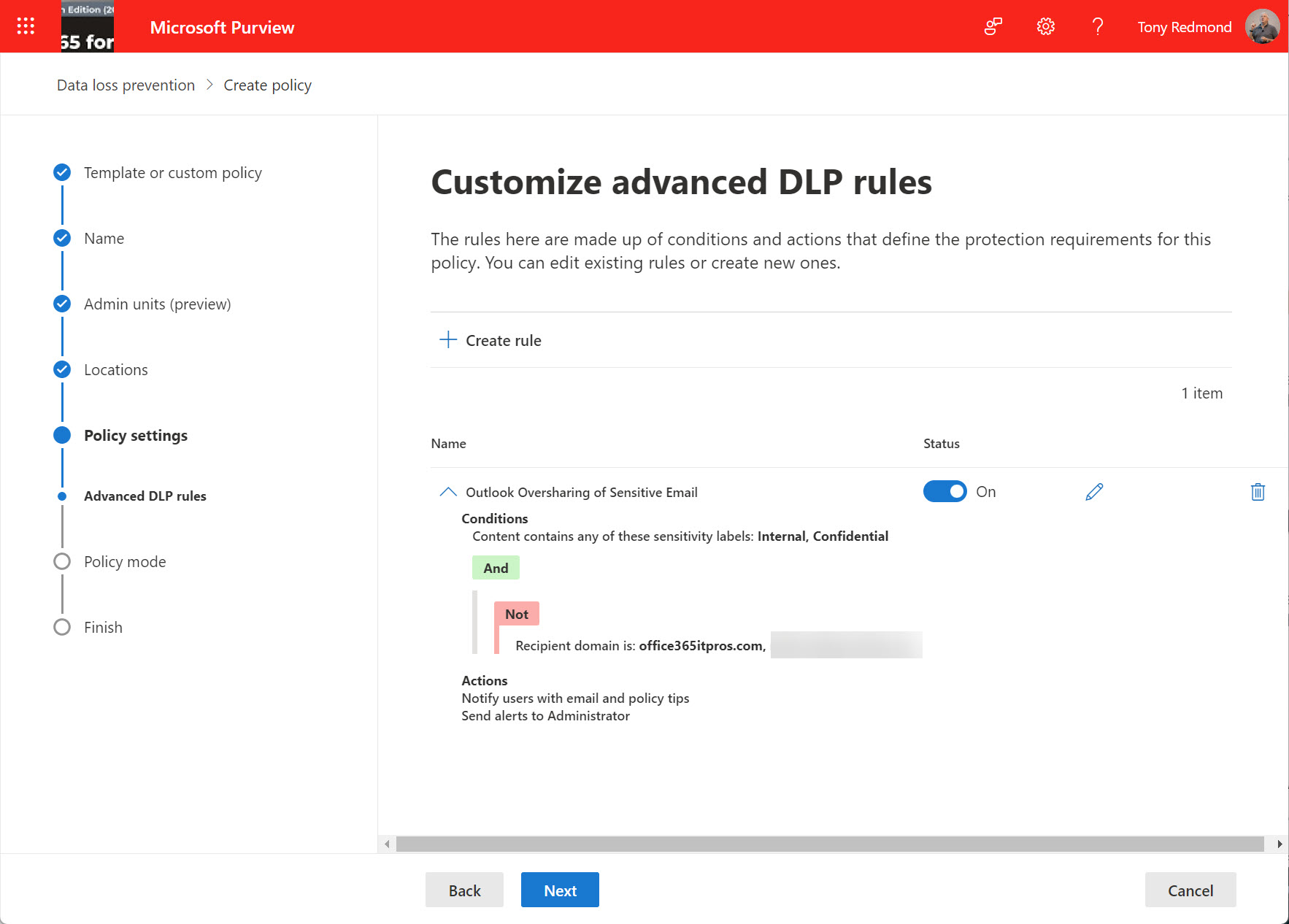
An update for Microsoft 365 Data Loss Prevention policies supports the configuration of oversharing popups for Outlook shown when a user composes email with specified sensitivity labels for either the message or any attachment. The idea is that the popup (a policy tip) helps the user to understand the problem and why they are violating a DLP policy so that they can address the problem before attempting to send the message.
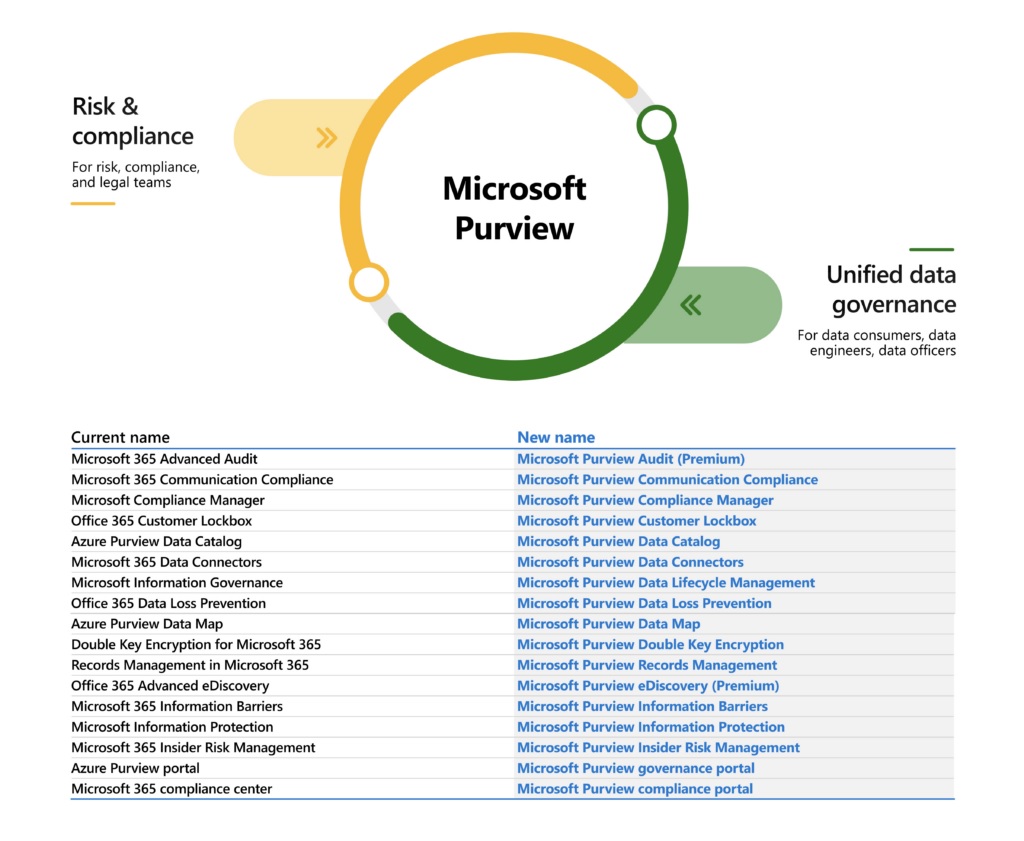
Microsoft marketing folks are no doubt very pleased with their latest branding success in introducing the Microsoft Purview suite. Others aren’t quite so thrilled, especially anyone who writes about technology and now has to update text to match the desires of the brand police. On the upside, there’s some good new functionality coming for different products in the suite.
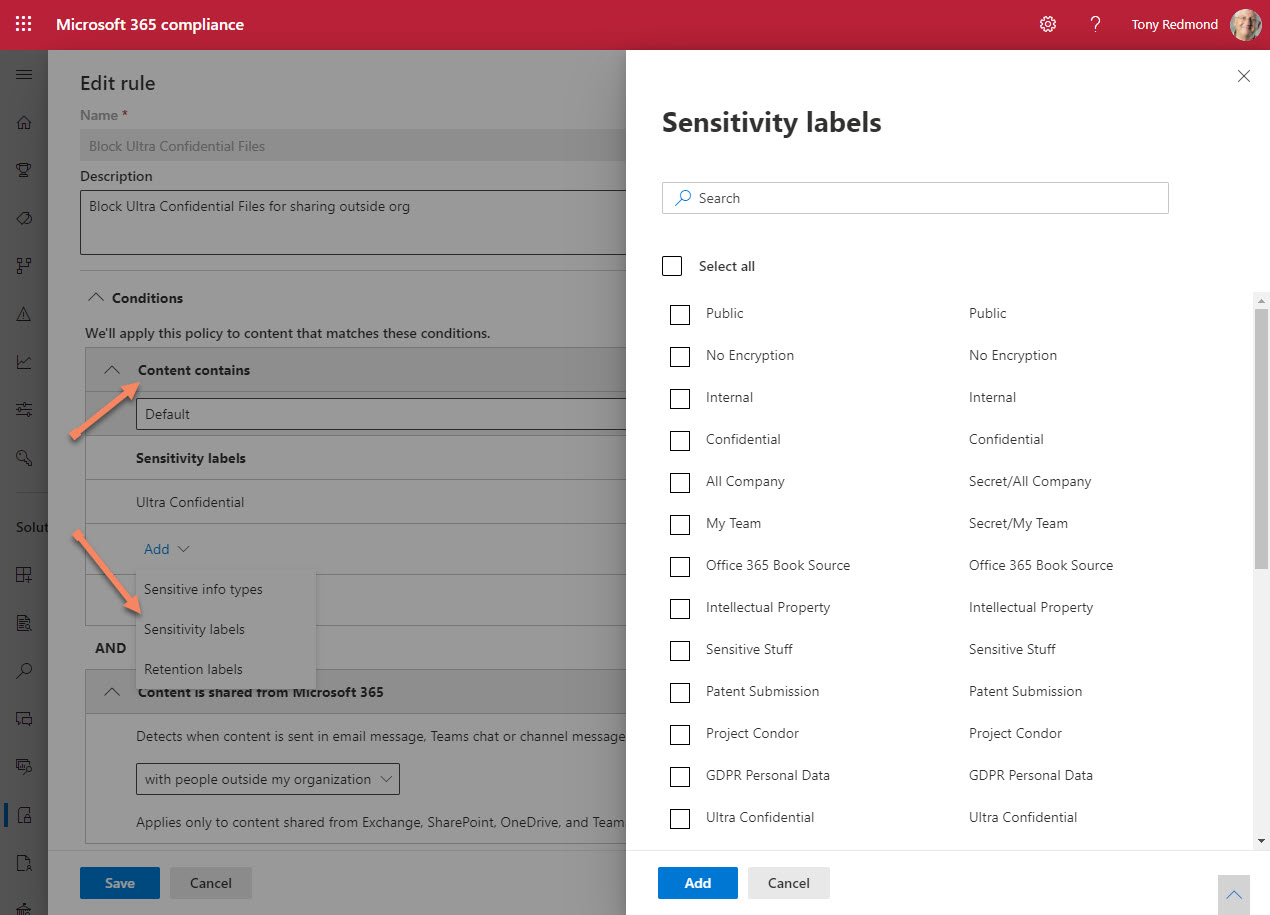
Microsoft 365 Data Loss Prevention (DLP) policies have wide-ranging capabilities when it comes to rules and exceptions. One exception covers the various types of encrypted email that can pass through the Exchange Online transport pipeline. As it happens, three message types are supported, but who could have guessed that permission controlled means rights management?
To make Microsoft 365 DLP policies work like Exchange transport-rule based DLP, a January change will switch evaluation of sender conditions away from envelope information to message headers. Although this change might seem to be something beloved of email geeks, it’s actually an important update for organizations who want to move away from ETR-based DLP to Microsoft 365 DLP policies.
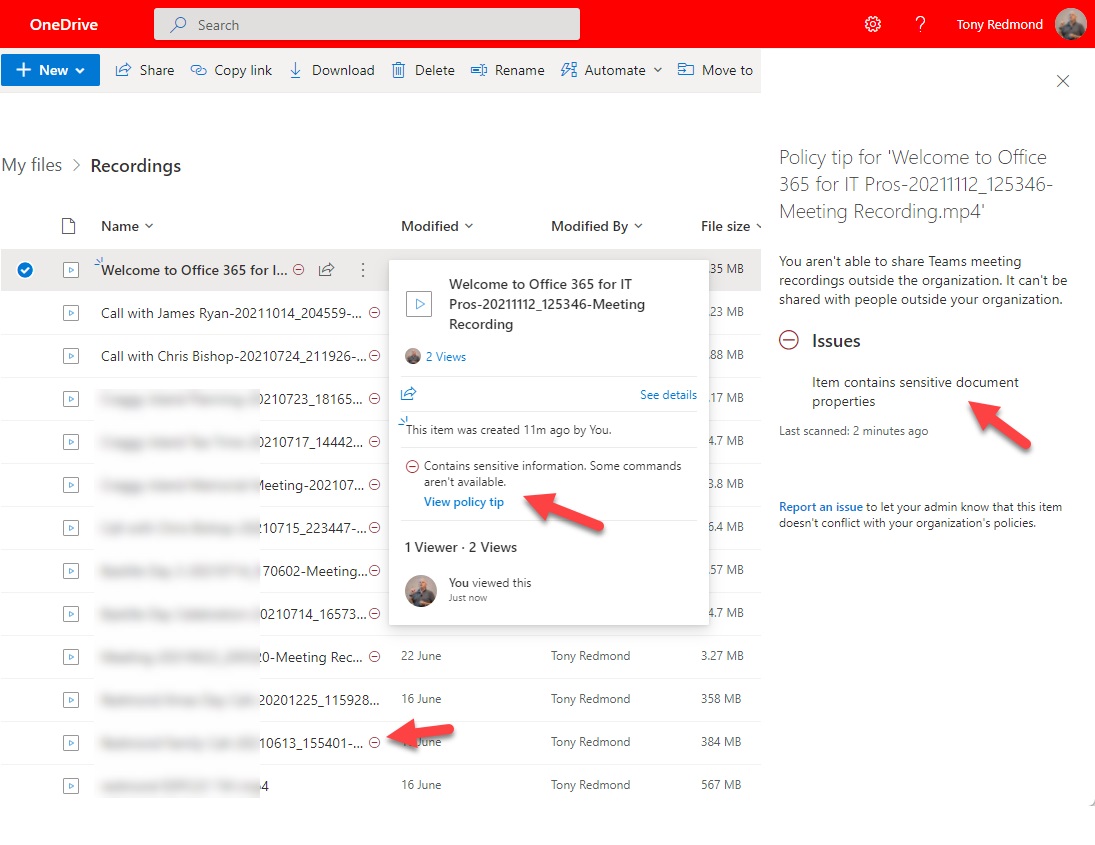
Teams meeting recordings can contain a lot of confidential information. It’s a quick and easy task to create a Data Loss Prevention (DLP) policy to stop people sharing these files externally, In this post, we show just how simple the required policy is, and just how effective it is at stopping external sharing.
Microsoft plans to surface recommendations to use communications compliance policies as part of its DLP workflow. That sounds acceptable, but it’s the second example of how Microsoft pushes high-priced premium features to Office 365 tenants through DLP. Apart from the undesirability of pushing features to customers through software, communications compliance is not something that you implement on a whim, so why does Microsoft think this is a good idea?
Microsoft 365 organizations which use Teams but don’t have a Teams DLP policy will see a Compliance Center widget recommending the creation of a DLP policy. Sounds good, and the policy covers the most common sensitive data types that people worry about. The downside is that Teams demands Office 365 E5 licenses for DLP policies. You might not know that, but you will if you accept the recommendation.
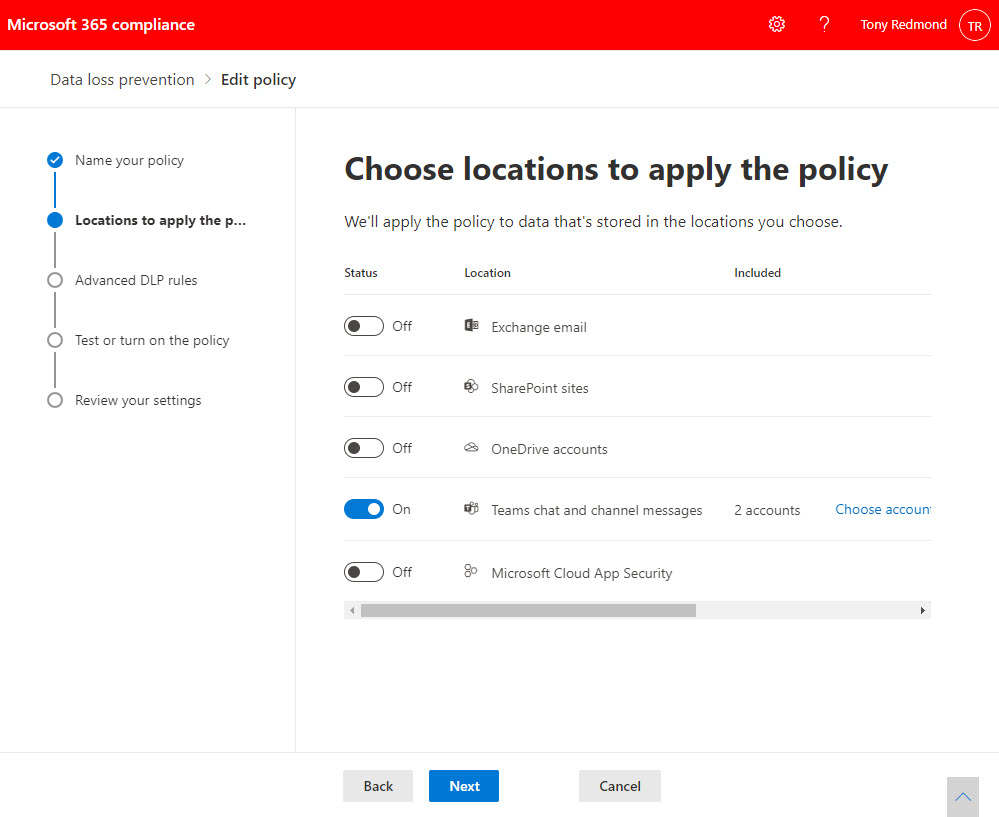
Teams Data Loss Prevention (DLP) policies help to stop users sharing confidential information through chats and channel conversations. A recent update means that accounts to be included or excluded in DLP policies can be specified using distribution lists or mail-enabled security groups. While this doesn’t sound very exciting, it is if you need to deploy DLP policies to targeted sets of Teams users.
Feb 24 2021 Update: The picker used for OneDrive for Business accounts will support distribution lists and security groups in March.
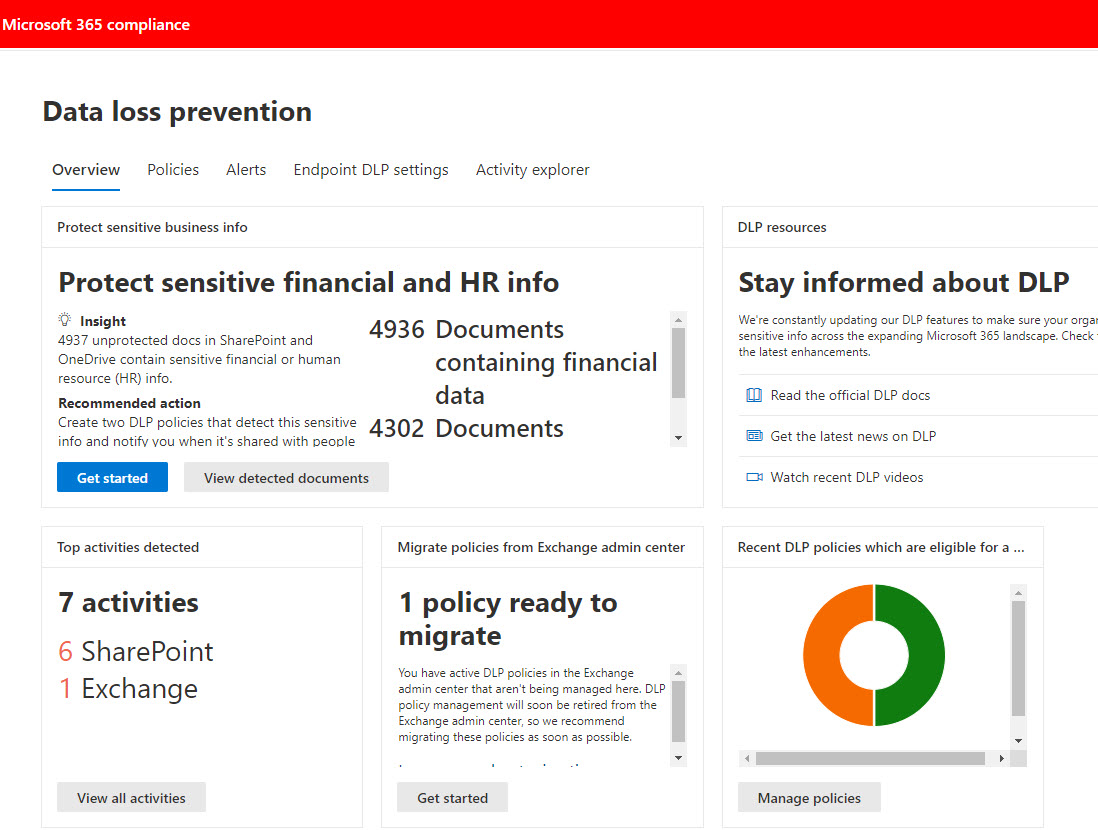
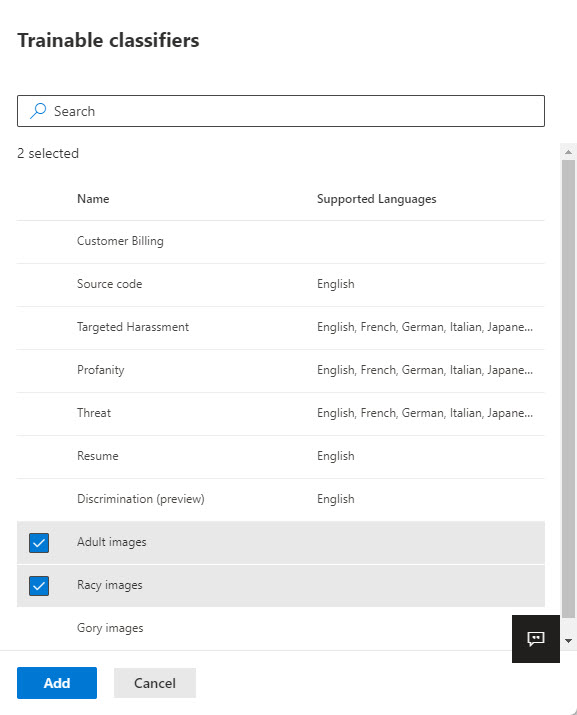
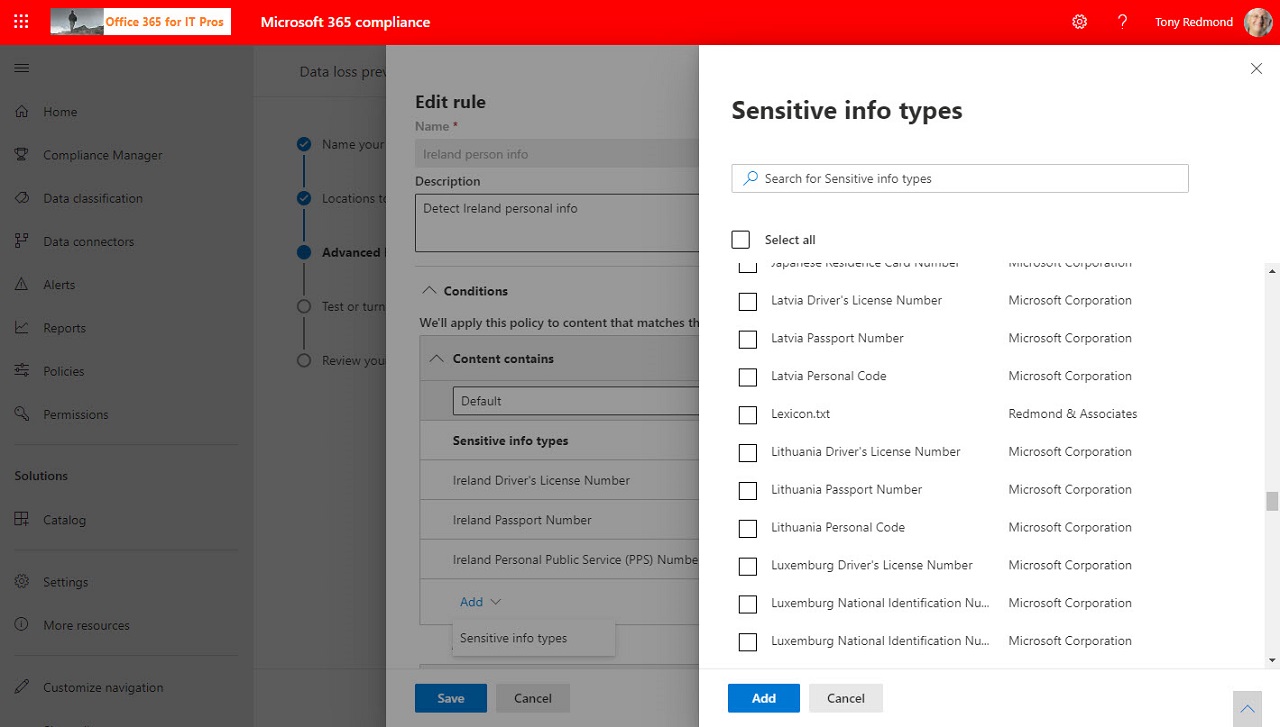
Microsoft has released a set of new sensitive information types, used to locate sensitive data by Microsoft 365 DLP policies. Many are country-specific versions of previous generic types (like passports or identity cards). The recommendation is to consider upgrading DLP policies to use the new types to get better (more accurate) matching.
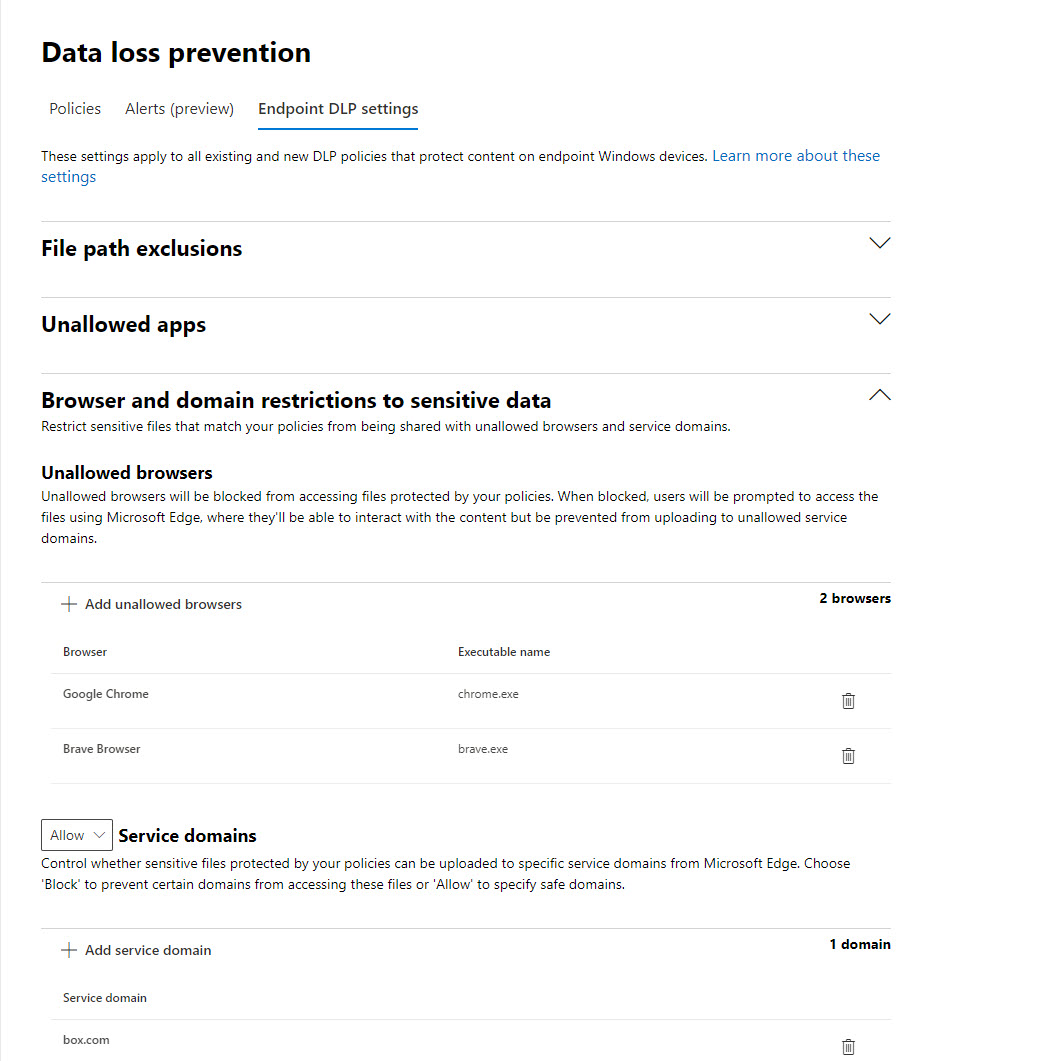
Microsoft has made Endpoint DLP generally available. Leveraging Windows 10 workstations and the Edge browser, Endpoint DLP sends signals for evaluation to detect possible violations. The solution requires Microsoft 365 licenses and only supports Windows, so it’s not for every tenant. But those who have Microsoft 365 licenses will find this an attractive solution.
When you need to block external access to your most sensitive documents, Office 365 Data Loss Prevention policies and sensitivity labels combine to find and protect the documents. A really simple policy is enough to detect and block external access, and is covered by Office 365 E3 licenses. If you have E5 licenses, you can consider auto-label policies to find and protect sensitive documents at scale.
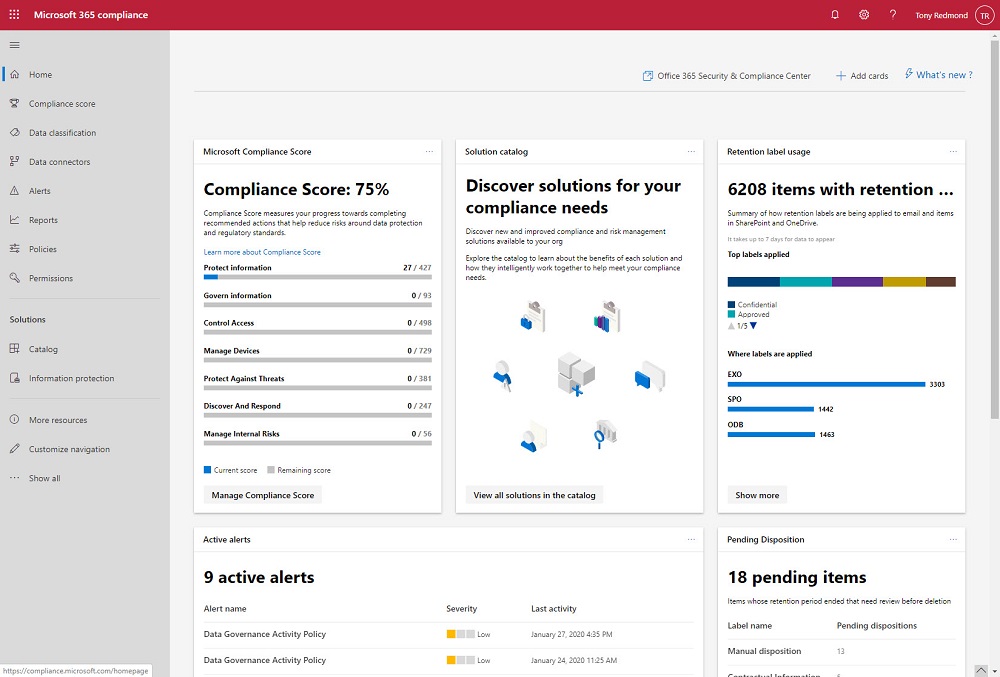
The Microsoft 365 Compliance and Security centers are roling out to Office 365 tenants where they’ll replace the old Security and Compliance Center over time. The new centers look fresher than the SCC, but looks can deceive and it’s much more important that the functionality exposed in the new portals work reliably all the time.
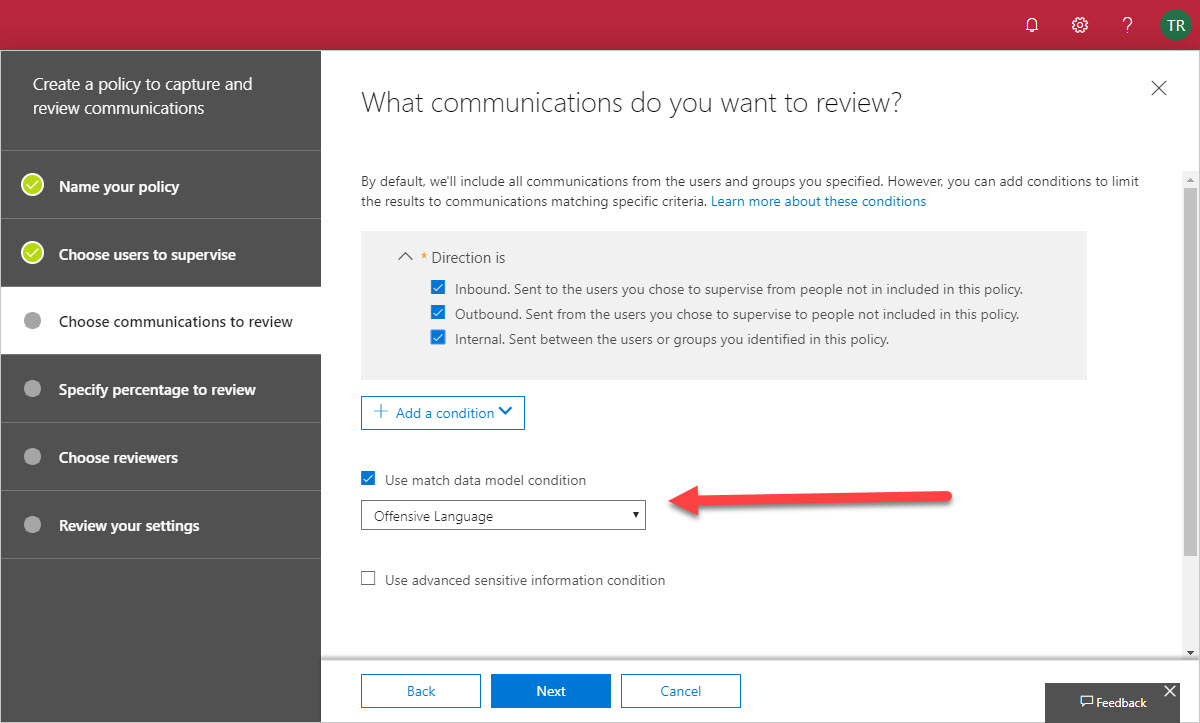
Office 365 supervision policies can now make use of artificial intelligence and machine learning to detect offensive language in email and Teams communications. The data model covers a wide range of problematic language, but only in English. You can go ahead and cheerfully continue to swear in French, German, and other languages with no danger of being detected by policy.
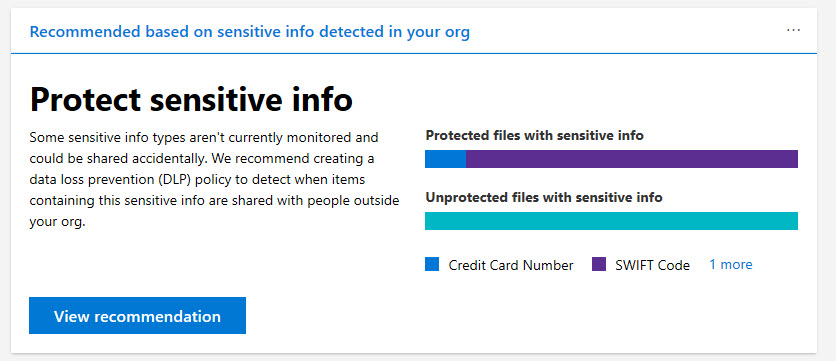
In a sign of how automation based on signals gathered by Office 365 will emerge to help administrators do a better job, the preview of the new Admin Center offered to create a DLP policy to protect some sensitive information that I had clearly overlooked. Well-intended as the portal was, its efforts to create the new policy failed. That’s not really important – it’s the glimpse into the future which is.
Office 365 offers different ways to apply encryption to important messages. When those messages hold sensitive data known to Office 365, like credit cards or passport numbers, we can define a transport rule or DLP policy to protect outbound email automatically. And while you can define rules and policies through the GUI, PowerShell is available too.
Microsoft thoughtfully provided Office 365 tenants with a Data Loss Prevention template for GDPR personal data. The only problem is that the rules in the template were too sensitive and started to block email.