Microsoft’s project to impose a mandatory MFA requirement for access to Azure management tools and sites will start enforcement on or after October 15, 2024. The new requirement will only affect administrator accounts who access Azure sites and tools (like PowerShell). Normal users shouldn’t notice any difference. The Azure MFA requirement is a great way to drive home the need for MFA to protect Microsoft 365 administrator accounts against attack. Prepare now!
HVE and ECS are two competing Microsoft Cloud Email Services. At least, they seem to compete. In reality, HVE and ECS serve different target audiences. HVE is all about internal email services for apps and devices while ECS is for high volume external mailings like customer newsletters. We tested both services by sending subscription reminder notifications to Office 365 for IT Pros readers.
On May 14, Microsoft announced that they will require Azure MFA for connections to services starting in July 2024. No details about the implementation are available, so it’s difficult to measure the likely impact on Microsoft 365 tenants. Given that very few people access services like the Azure portal, it’s probable that the impact will not be large, but it would be nice to hear more precise details from Microsoft.
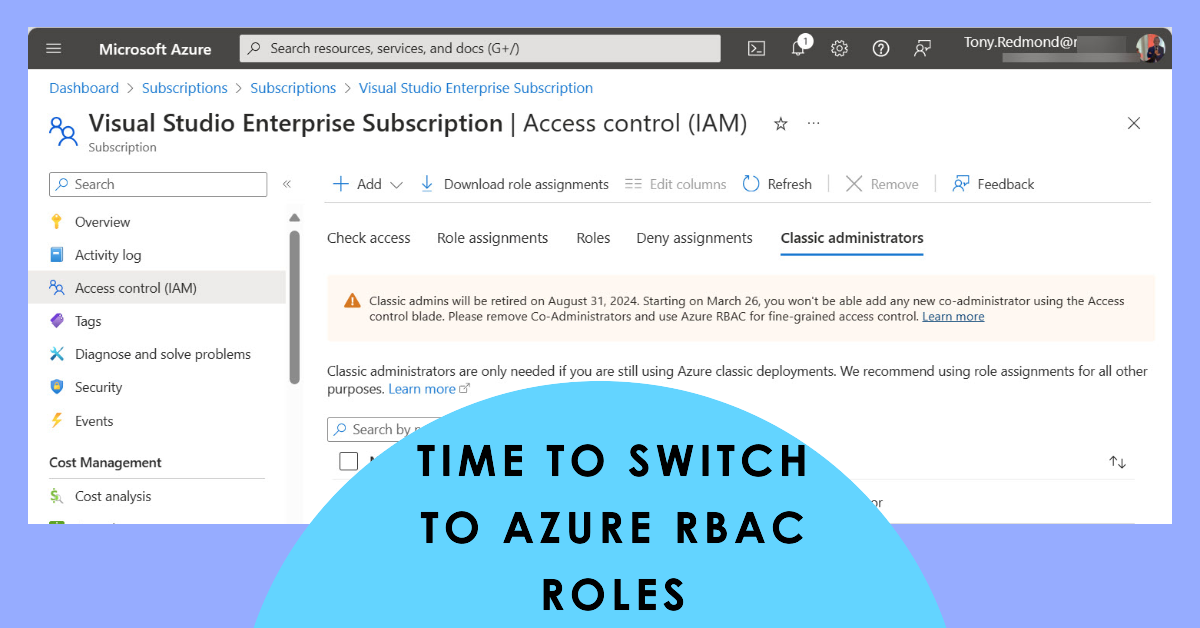
A recent note from Microsoft advised that if your tenant uses classic Azure administrative role, you need to switch to Azure RBAC roles by 31 August 2024. This forced me to think about how many Azure services does my tenant consume. The number was surprising and it’s grown over time, which is why Microsoft 365 tenant admins should pay attention to Azure.
Microsoft plans to retire Azure Automation Run As Accounts on September 30, 2023 and replace them with managed identities. I don’t have any issue with the proposal because managed identities are more secure and a better overall solution. It would have been nice if Microsoft had communicated the change more broadly. I guess if you were in the know, you found out about this development, but maybe the average Microsoft 365 tenant administrator might have struggled to discover what’s happening.
Before an app or an Azure Automation account can use the Teams PowerShell cmdlets in a script or runbook, it must have the permission to act as an administrator. In this article, we cover how to assign the necessary role to a service principal.
I’ve spent some time investigating Azure Automation PowerShell recently. In this article, I discuss three learnings that might be of interest to others. Debugging, cost, and tracking the use of Azure Automation PowerShell might not interest everyone, but they’ve certainly helped me to understand how the platform works.
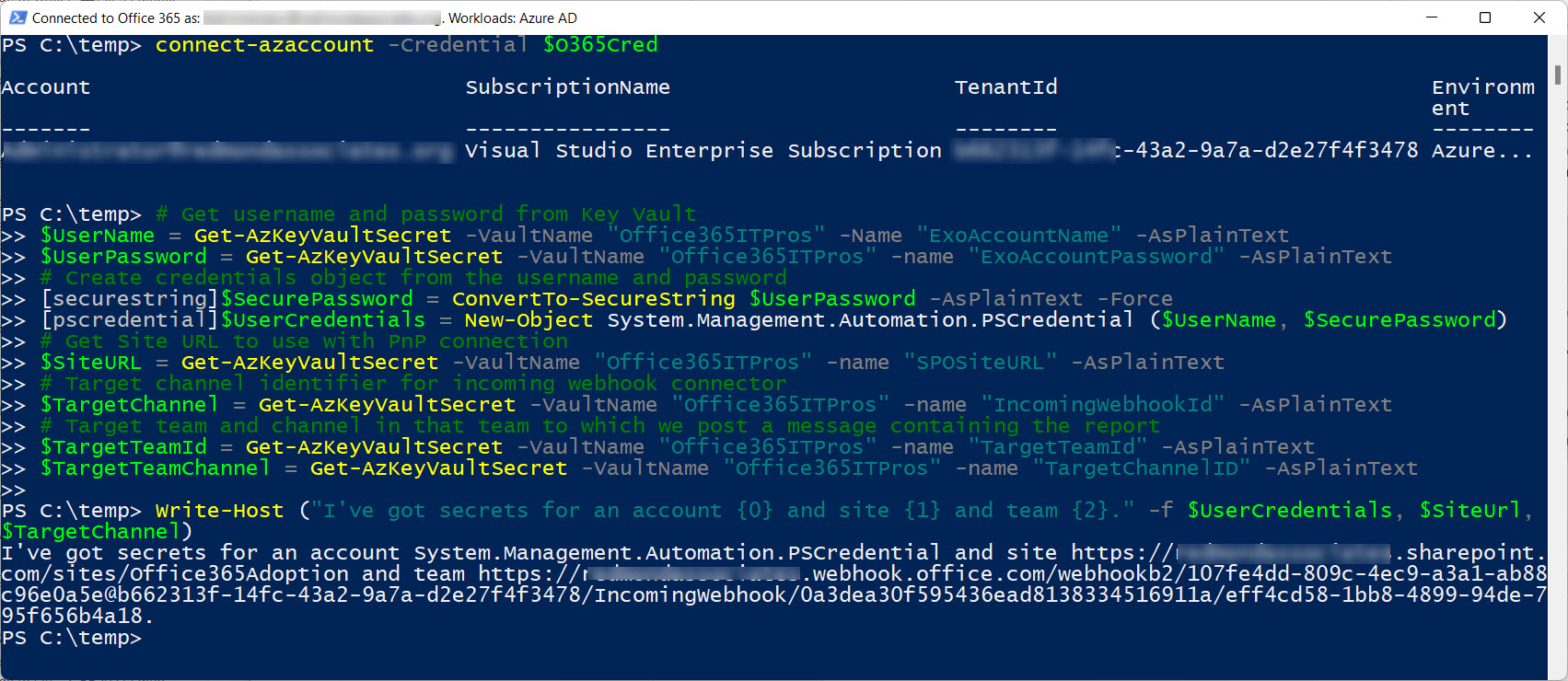
A previous article explains how to use an Azure Automation runbook to write information to a SharePoint Online site and Teams channel. At the time, I used a stored credential to authenticate and access SharePoint and Teams. Azure Key Vault offers another way to store secrets (bits of information) securely. This article explores how to store secrets in Azure Key Vault and retrieve and use the secrets in a runbook script and interactive PowerShell.
Office 365 tenants using Entra ID external identities (like Entra ID B2B Collaboration guest accounts with apps like Teams) are moving to a monthly active users (MAU) billing model. The new model replaces the 1;5 ratio for Entra ID premium licenses used up to now. Microsoft allows tenants to have the first 50,000 unique external identities free of charge each month and bills for access thereafter. If you don’t already have an Azure subscription, you’ll need one to link to Entra ID. Linking the subscription should be an easy task, until it’s not…
A recent report puts the availability of Azure behind Google and Amazon Web Services (AWS). Office 365 tenants depend on Azure in a variety of ways. The recent problems occurred in a variety of places and there’s no common thread connecting the different issues. It seems like Azure has had a run of bad luck, so let’s hope that the bad days have passed and reliability improves.