Table of Contents
Removal of Microsoft 365 Admin Center Option to Send Password in Email
In a change that surprises only because it took so long to be made, message center notification MC837081 (29 July 2024) announces that administrators will lose the option to send user passwords inemail after August 30, 2024. Although the detail in the post is hazy, I assume that this change refers to the email the sign-info info to me option after changing a user account password in the Microsoft 365 admin center (Figure 1).
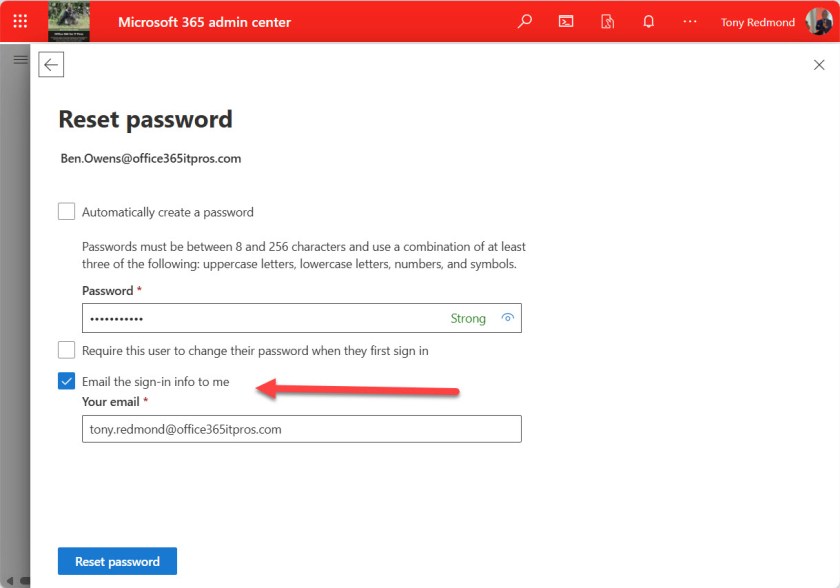
Sending Passwords in Email is a Terrible Idea
The option to send a changed password by email has always existed in Office 365/Microsoft 365, possibly because it’s difficult to remember system-generated passwords. Sending email to the administrator to remind them about the password is possibly a lesser evil than writing down a system-generated password.
Users should always be forced to change their password when they first sign in after an administrative process changes their password. Even if a secure system-generated password is used, it’s unlikely that the user will remember it and they’ll either write the password down on a sticky note or request another password change. It’s better to let the user use the self-service password reset (SSPR) feature to choose their own password, providing it meets password complexity requirements.
An argument can be made that passwords don’t matter all that much anymore. This might be true if strong multifactor authentication (like the authenticator app or passkeys) protected every Microsoft 365 account and we had reached the stage where passwordless operation was possible everywhere, but there’s more work to be done before Microsoft 365 gets to that point.
Overall, sending password information in unencrypted email is a terribly bad idea that encourages people to treat passwords with less respect than they should. Purview Data Loss Prevention (DLP) includes sensitive data types for Azure AD (Entra ID) user credentials, User login credentials, and All credential types to help organizations block emails and Teams messages containing usernames and passwords.
The Print Option
Microsoft’s suggested replacement is to use “the new Print option in the Microsoft admin center to save the user account details and share them in a secure manner with your users.” I don’t see any trace of a new Print option in the Microsoft 365 admin center and the advice in the documentation is to use the print to PDF feature (CTRL/P). This works, even if it creates too many pages in the output PDF, and the method has the advantage that the PDF can be protected by a sensitivity label. I imagine that in most cases the PDF will be sent as an email attachment to someone like the user’s manager instead of being printed off and carried by an administrator direct to the user.
How best to get a new password to a user in a secure manner is a good discussion for tenant administrators to have. Given that many users work from home, it seems like making a phone call to communicate the new password is the most practical method. That is, if you can reach the user. Another idea I have heard include using Azure Key Vault to store updated credentials that a user can access through an Azure function.
Moving On
I doubt that many will mourn the passing of the option to send a user’s password to administrators via email. It’s a legacy artifact from a simpler time when passwords weren’t treated with as much respect as they deserve. It’s time to move on toward a future where user passwords are less important than they are now.
Learn how to exploit the data available to Microsoft 365 tenant administrators through the Office 365 for IT Pros eBook. We love figuring out how things work.
One possible alternative option is to share the password via an otp link.
how would this be setup?