Table of Contents
Pondering the Right Way to Delete OneDrive for Business Accounts
The July 22 article about choosing between shared and inactive mailboxes to preserve ex-employee content created a lot of discussion. I guess the possibility of exposing PII data inadvertently through access to mailboxes converted to shared mailboxes hadn’t been considered by many. In any case, this is a real concern because no organization wants to open itself up to potential lawsuits.
As I chatted with people, it became clear that some tenants don’t have an automated account preservation process. It might be acceptable in a small organization to rely on the account deletion wizard in the Microsoft 365 admin center (Figure 1) because it takes care of the essentials, like offering the option to convert the deleted user’s mailbox into a shared mailbox and giving another user access to their OneDrive for Business account.
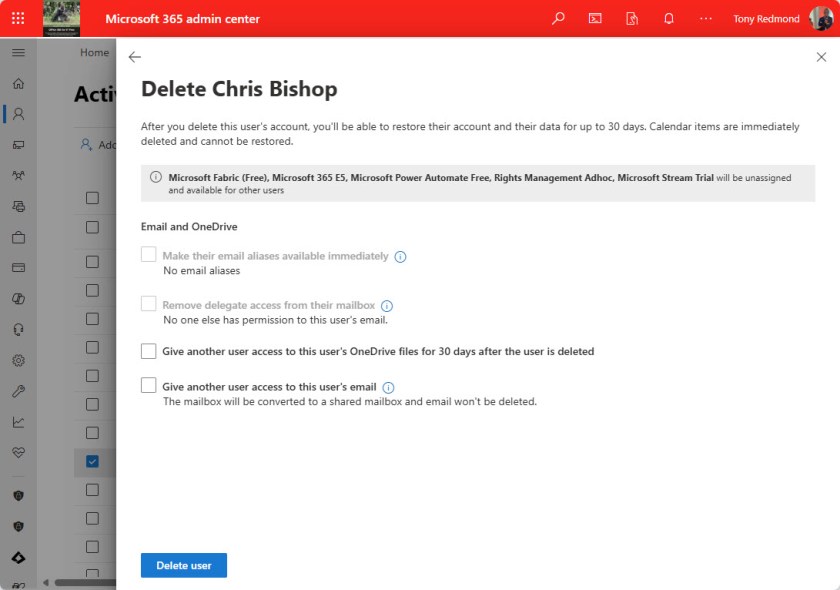
The Other Bits Surrounding Microsoft 365 Account Deletion
Deleting a user account through the Microsoft 365 admin center is a swift and certain way to stop access. However, sometimes a little more subtly is needed. For instance, you might want to:
- Add the user to a special retention policy so that their mailbox becomes inactive rather than being made shared.
- Force sign-outs from the account by revoking access. Instead of immediately deleting an account, I usually revoke access, disable the account, and change its password. All are continual access evaluation (CAE) events monitored by Entra ID that cause a user to loose access to apps.
- Issue wipe commands to mobile devices. The process depends on the devices in use and the management software with the aim to remove corporate data from the devices. For instance, if you use Exchange Online mobile device management, Outlook clients support a Wipe Only command, meaning that only mailbox data is covered. Other clients use the Account Only Remote Wipe Device command to do the same thing. Don’t use a Wipe Only command with something like the Apple iOS mail client, as this will wipe all device data.
All these steps are very scriptable. The basics of revoking access from an account are covered in this article and you can find an example account removal script in GitHub to use as the basis for development to cover the requirements of your organization.
The OneDrive for Business Account Deletion Issue
Dealing with OneDrive for Business accounts owned by deleted users pose two issues. First, OneDrive for Business is the designated repository for personal information, so the likelihood of PII data being present is very high. Microsoft has done as much as possible to force applications to save files in OneDrive for Business. The upshot is that files containing personal information are now more likely to be in the cloud than on a local hard drive.
Second, the sheer volume of files stored in OneDrive for Business grows steadily. Office documents, PDFs, Loop components shared in Teams and OneDrive, Teams meeting records, Whiteboards, Stream videos, and even PowerShell modules can end up in a person’s OneDrive for Business account. Parsing out what’s there and what needs to be recovered for future use by the business is a difficult task.
Organizations can configure automatic access delegation, which means that a user’s manager is automatically made a site administrator of the user’s OneDrive for Business account when a user is deleted. A secondary owner can also be defined in case a manager is not defined for the account (Figure 2).
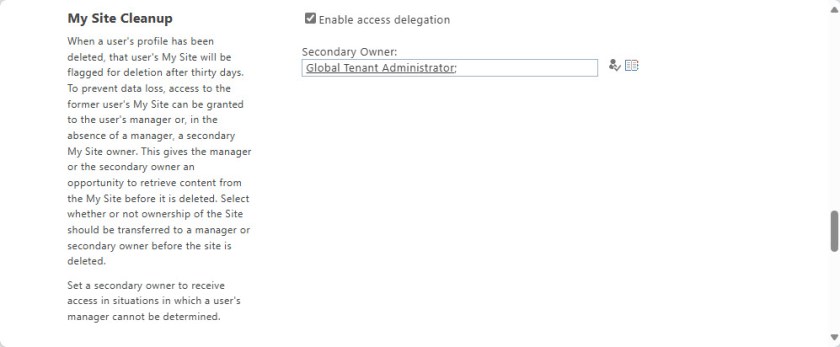
I don’t think I have changed the settings shown in Figure 2 for years. Nominating the Global tenant administrator account as a secondary owner is not a great idea. It’s better to use a designated account with no administrative roles to act as the backstop for access to the OneDrive for Business accounts owned by deleted users.
Two other questions arise here. First, it’s important to keep manager information updated and accurate to have any chance that access delegation will work. Some form of automated processing is likely required on a periodic basis to ensure that user accounts are linked to the correct managers. Second, even if the right person is known, will 30 days be enough to review and extract all the relevant information from the OneDrive for Business account?
Thirty days is the default, and you can set a tenant-wide retention period of up to 10 years through the settings section of the SharePoint admin center (Figure 3).
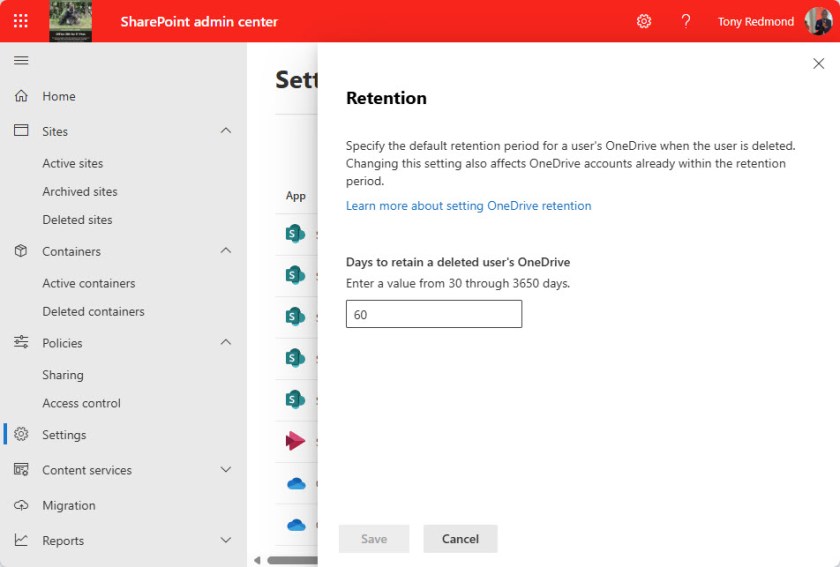
The Time Conundrum
Thirty days is too short to allow a stressed manager the time to conduct a full review of what could be gigabytes of data created by multiple applications. Ten years is obviously too long to keep the OneDrive for Business account for a deleted user in place. Somewhere in the middle might suit, but the organization still depends on the manager to perform a full review of the account contents before the retention period ends.
The trick is to have enough time use the 30-day default retention period for a quick review of contents and then store the OneDrive for Business account somewhere safe from where information can be retrieved if necessary. I already mentioned adding the user’s mailbox to a special retention policy before deletion to force Exchange Online to make it into an inactive mailbox. I also add the OneDrive for Business account to the same retention policy. The retention period is six months, which is enough to allow information recovery by running an eDiscovery content search against the account and exporting the results. Yes, it’s a pain to ask the compliance team to run a search, but this approach avoids problems with PII because the organization can demonstrate controlled access to the data and the retention period can be as long as required.
This issue is not going to get any easier. Microsoft designed the current OneDrive for Business retention and deletion implementation years ago (just look at the old-style UI in Figure 2). OneDrive for Business was simple then. It’s not now. The basic idea about keeping an account around for a period after the deletion of its user’s account is fine. It’s determining what’s in the account and what needs to be kept that’s the most difficult task, even with a nice print-out of the account’s files.
Insight like this doesn’t come easily. You’ve got to know the technology and understand how to look behind the scenes. Benefit from the knowledge and experience of the Office 365 for IT Pros team by subscribing to the best eBook covering Office 365 and the wider Microsoft 365 ecosystem.
One Reply to “The OneDrive for Business Problem Created When Deleting User Accounts”