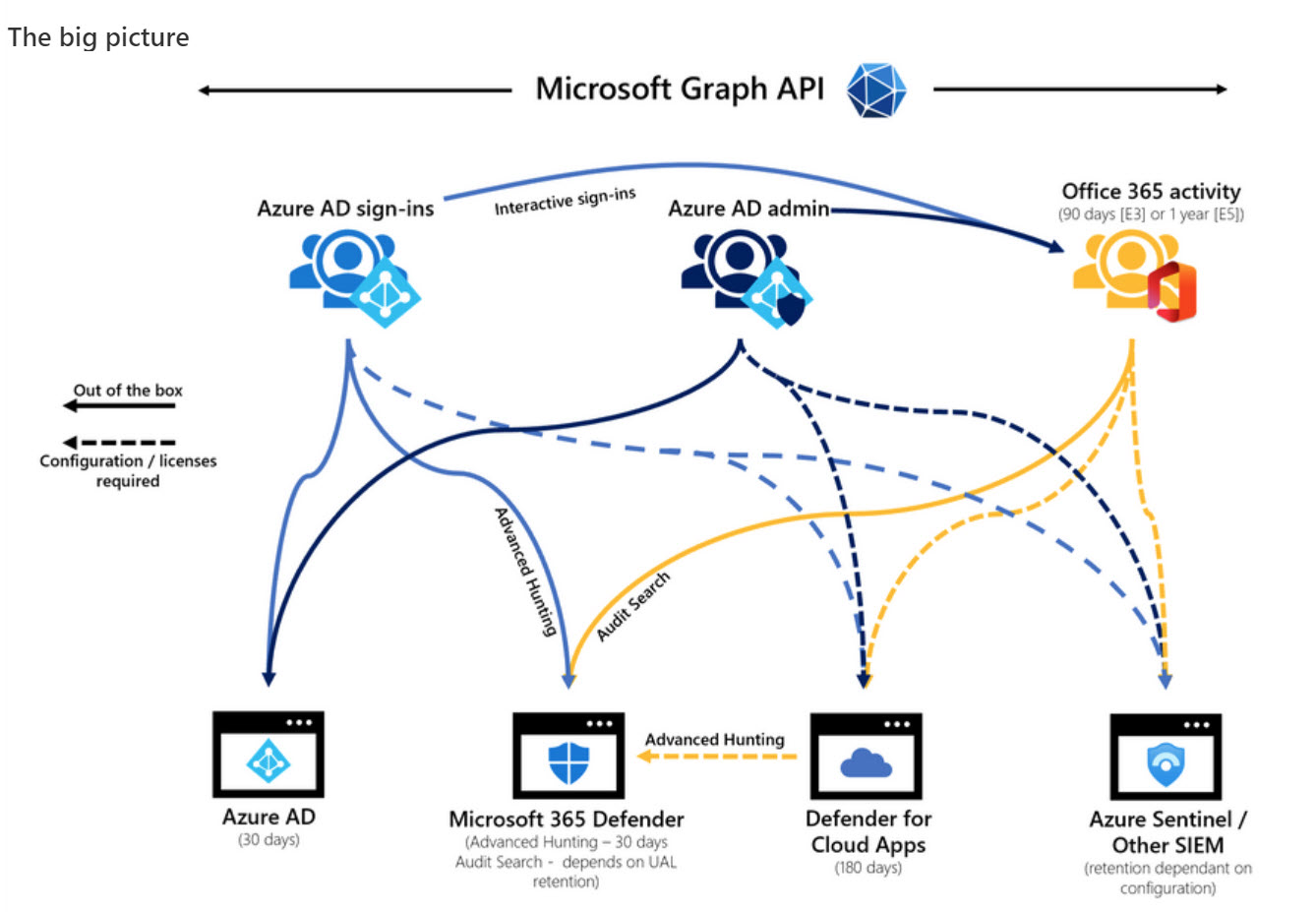
Microsoft Purview and the Exchange Online Search-UnifiedAuditLog cmdlet both perform searches of the Microsoft 365 unified audit log. Both mechanisms support the concept of scoped searches to limit audit records returned by searches to the administrative units an account can manage. But the permissions assigned by the two mechanisms aren’t synchronized, which can lead to complications.
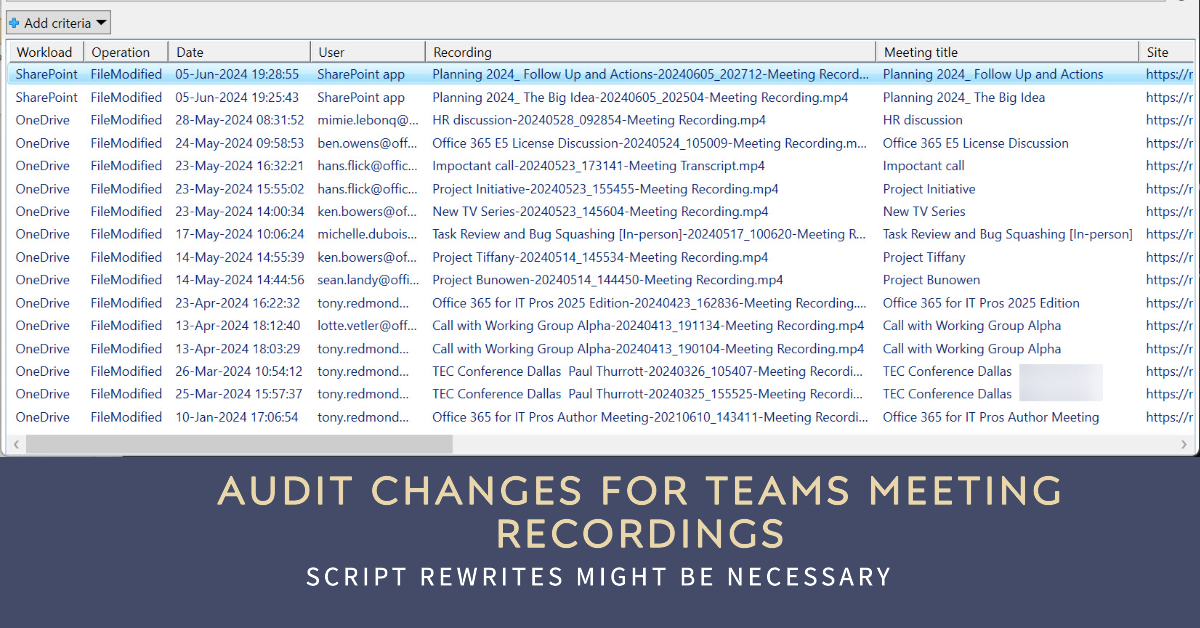
Three years ago, I wrote a script to analyze the audit records generated for Teams meeting recordings. Then things changed in terms of how the audit records were generated and how the Search-UnifiedAuditLog cmdlet returns audit search results. All of which meant that considerable work was needed to revamp (rewrite) the script. Maybe you need to check any script that uses the Search-UnifiedAuditLog cmdlet too?
A new preview feature supports high completeness audit log searches. These searches are optimized to make sure that they find every matching audit instead of finishing as quickly as possible. High completeness audit log searches do take more time but their results are accurate and they find more records than Search-UnifiedAuditLog was able to in the past. Looks like a good new feature.
A January 26 post announces the deprecation of four old Exchange audit cmdlets in favor of the Search-UnifiedAuditLog cmdlet. Removing old cmdlets is fine, but it would be nice if Microsoft took the opportunity to make Search-UnifiedAuditLog work better. Too many inconsistencies exist in how workloads provide information in audit events and Microsoft has made some recent unannounced changes.
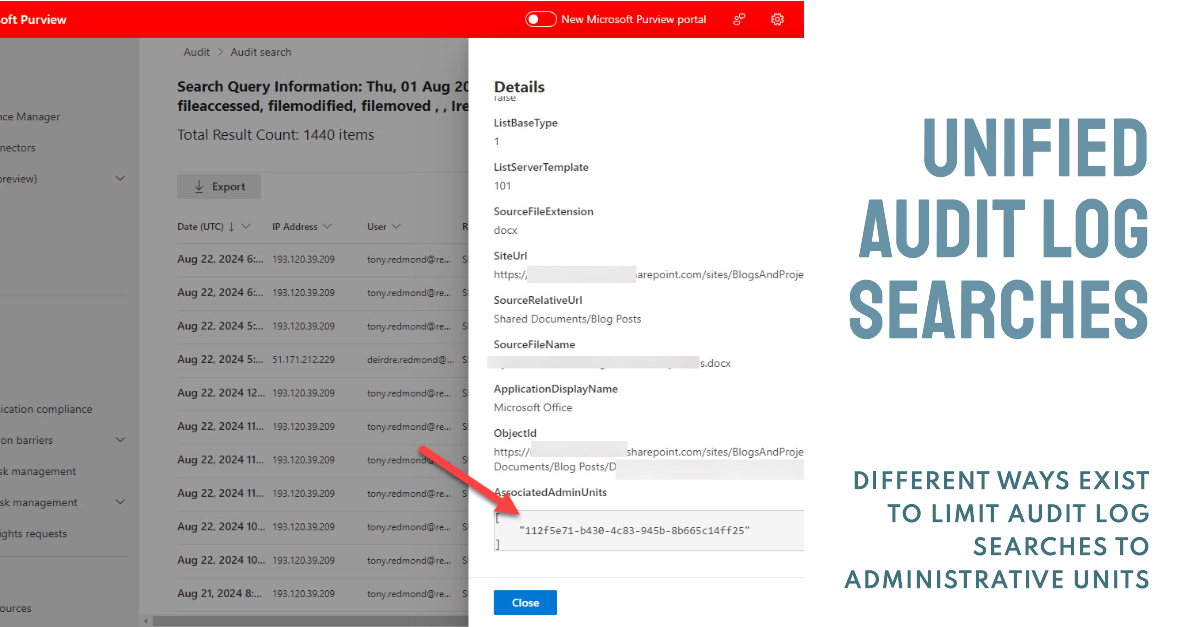
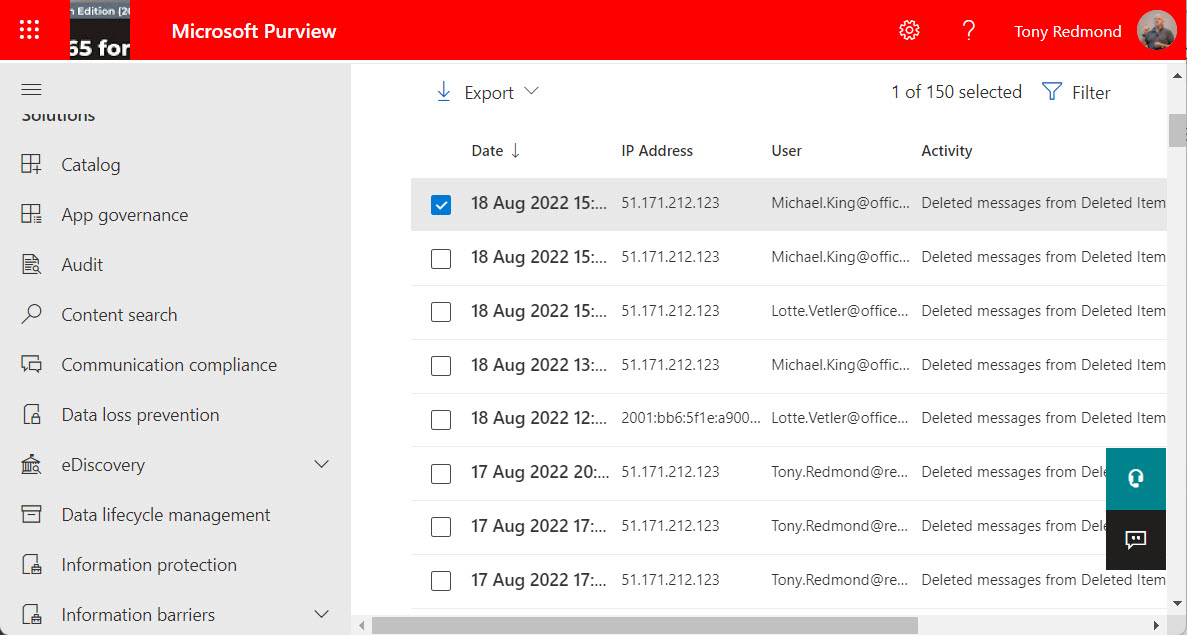
Entra ID administrative units are supported for granular access to the Microsoft 365 audit log. Exchange Online manages the audit log so it’s core to the support. This article reviews how to restrict access to the audit log using compliance roles and RBAC and how administrative unit data is stamped onto audit events during ingestion to support restricted searches based on administrative units.
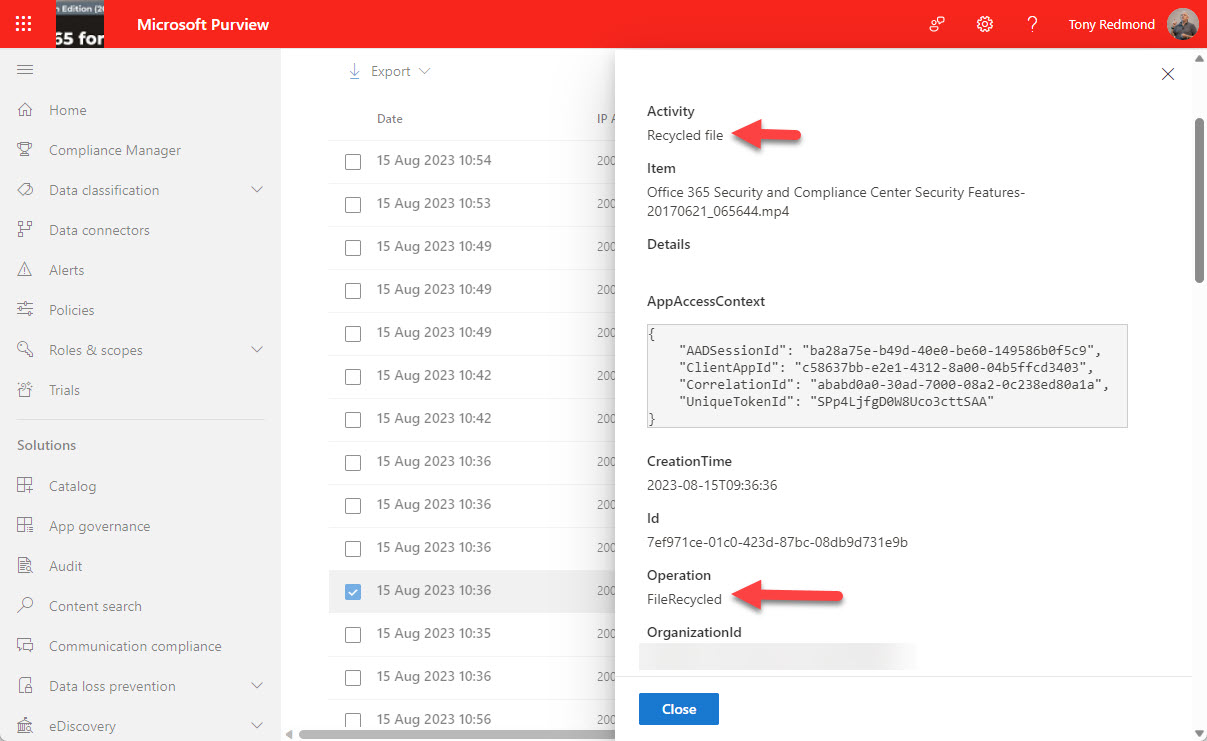
For years, I have scanned the audit log to find FileDeleted events to report deletions of SharePoint and OneDrive documents. Now, FileRecycled audit events are used instead. This wouldn’t be a problem if Microsoft had told customers, but not a trace can be found to let organizations know that the audit data they use for compliance operations has changed. I don’t know if this is the only activity name change, but given that one update has happened (and for a relatively important audit event), it’s likely that others lurk in the undergrowth.
A reader asks how to monitor membership changes for some specific high-profile groups. You can buy a commercial product to do the job or use PowerShell to exploit the information held in the Office 365 audit log. A combination of a custom attribute assigned to the sensitive groups and an audit log search does the job.
Microsoft DART (cybersecurity response team) published an interesting article about the essential sources of Microsoft 365 audit data used for forensic investigations. The Office 365 audit log gets a big mention and DART seems pretty impressed by the new audit log search that’s available in preview in the Purview Compliance portal. I’m not impressed by the performance of the new interface and will continue to use PowerShell. As it turns out, so will DART.
In March 2020, I wrote about mailbox audit events for Office 365 E3 accounts not showing up in the Office 365 audit log. As far as I can tell, Exchange Online deals with new mailboxes properly now. However, there might be some mailboxes in your organization that aren’t generating the audit records you thought they are… so it’s time to check.
It’s a good idea for administrators to know when people archive or restore teams, just in case users lose access to private or shared channels. This article explains how to search the audit log to find records for these actions, extract the relevant data, find information about channels belonging to the teams, and create a report.
The Microsoft 365 audit log holds all kinds of useful data, including events logged for SharePoint Online and OneDrive for Business file deletions. It’s easy to use PowerShell to search the audit log to find and interpret the events and create a report. Large tenants might need to export the audit data on a regular basis to an external repository to allow for long-term retention and analysis. We explain the principles of the process in this article.
When SharePoint users share information, Office 365 captures events in its audit log. By analyzing the events, we can build a picture of how people share information. The sad thing is that the audit events logged when someone extends the validity of a sharing link doesn’t contain as much information as you might like. Even so, we can still analyze the sharing events to build a picture of what happens in an Office 365 tenant.
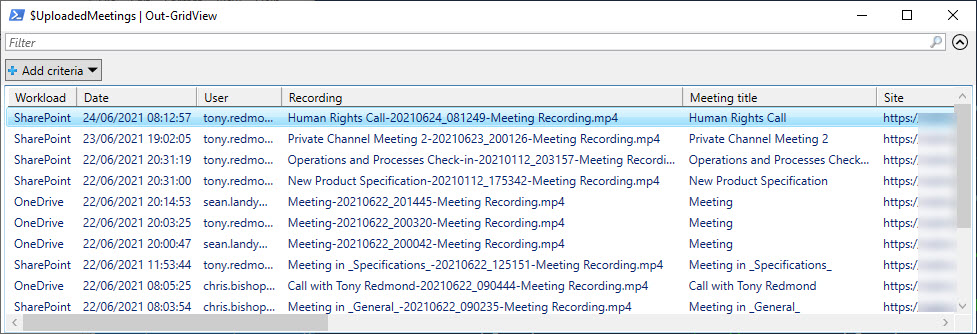
After writing about auto-label policies for Teams meeting recordings, we were asked about how to track the creation of the recordings. The key to be able to report the data us events in the Office 365 audit log. Once you know where to look, it’s easy to find the audit records and extract data about the creation of Teams meeting recordings.
Auto-label policies are a good way to assign retention labels to important files stored in SharePoint Online and OneDrive for Business. The big problem is tracking the progress of auto-labeling. In this article, we explore how to use events logged in the Office 365 audit log to figure out what files are labeled and how long it takes the auto-label policies to process the files. The example explored here is an auto-label policy for Teams meeting recordings.
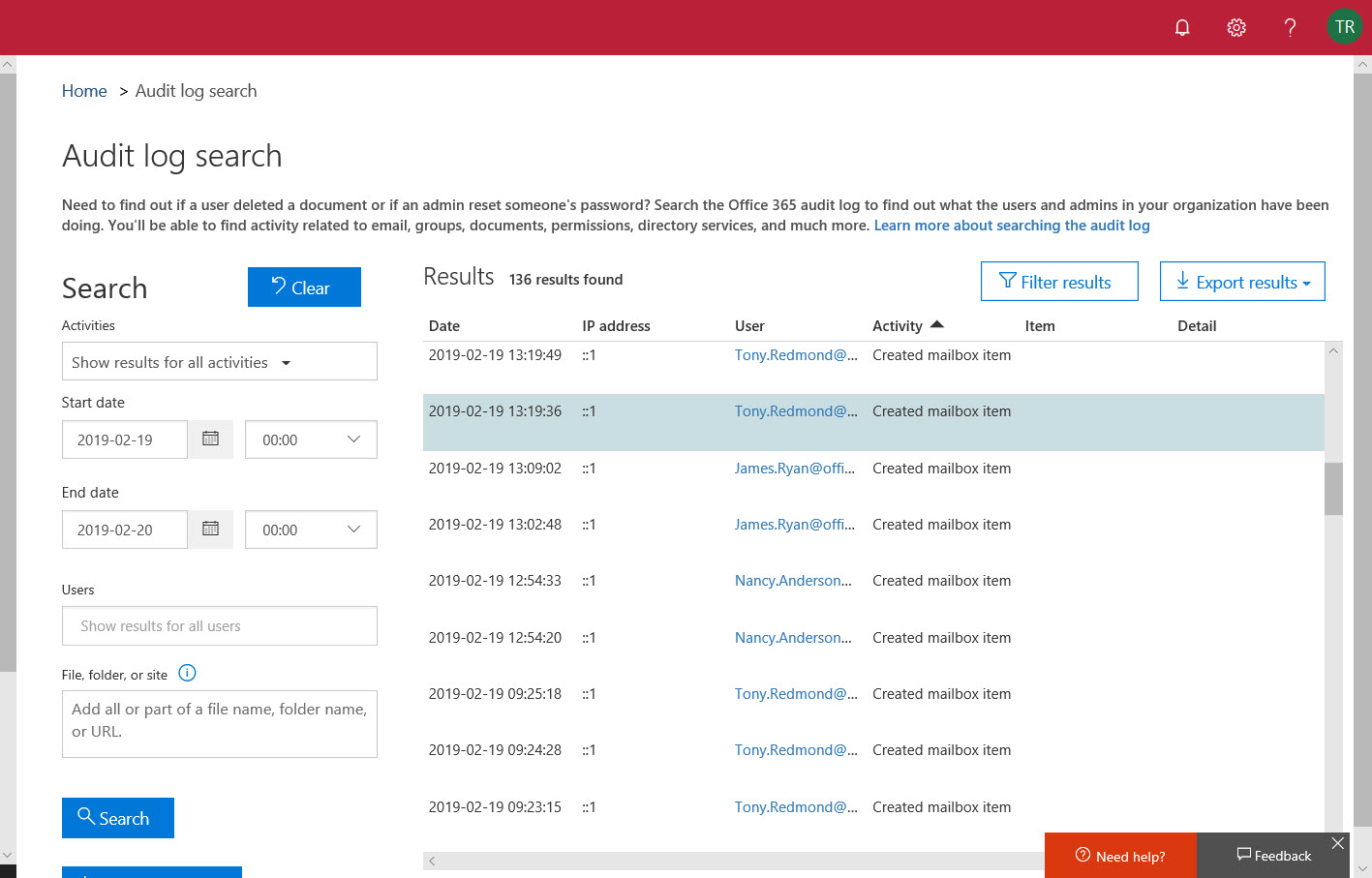
The Office 365 audit log is a great source of information about what happens inside a Office 365 tenant. Searching the audit log takes practice, but it turns up lots of insight. This article covers how to use the ObjectIds and FreeText parameters to find information about what happens to an object,
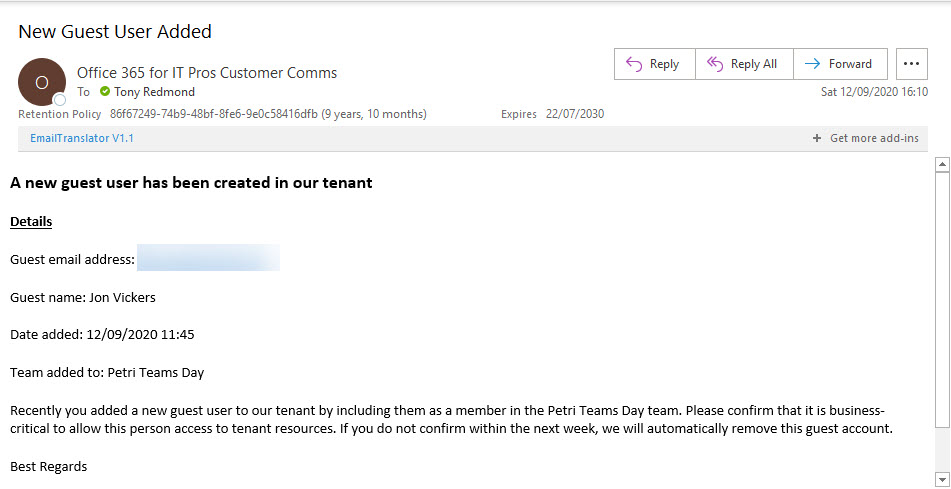
You can easily add people from outside your Office 365 tenant to the membership of Teams, but some oversight of who those people are and what teams they join is probably needed. This PowerShell script shows how to find records in the Office 365 audit log and figure out if they relate to the creation of new guest accounts before sending email asking to justify the addition of the new account.
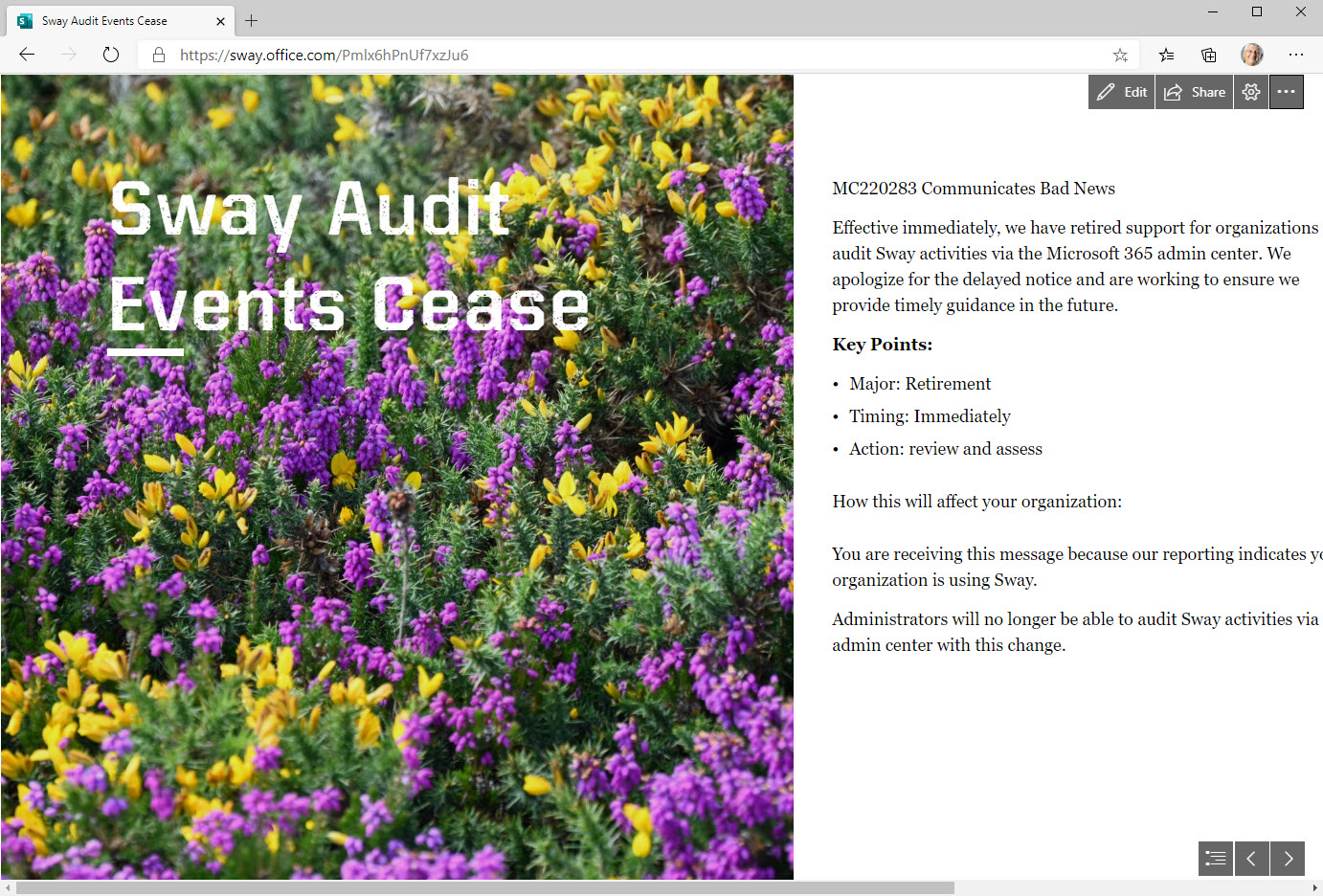
Office 365 notification MC220283 says that Microsoft has retired support for organizations to audit Sway activities. In other words, no more Sway events in the Office 365 audit log. This might or might not be a problem for your tenant, depending on how much use you make of Sway and if you have the necessary licenses. But the real problem is the lack of communication before Microsoft removed the feature. That’s not good.
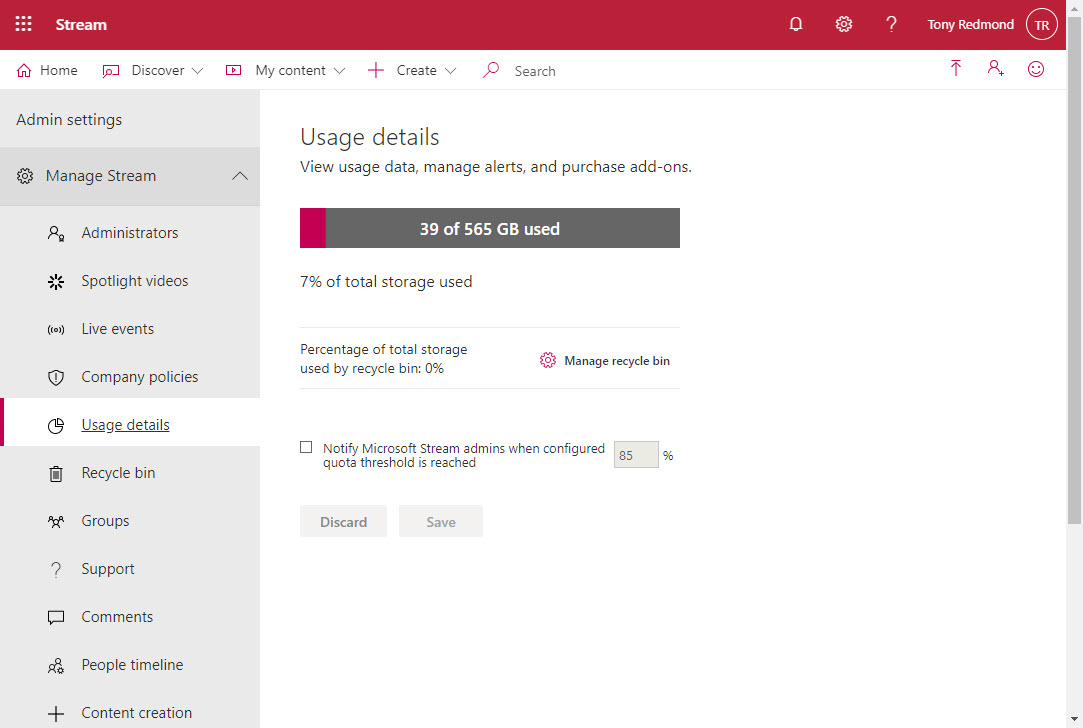
Microsoft Stream will tell you how much of the tenant storage allocation has been consumed by uploaded videos, but not who’s uploading the videos. You can find out by looking for video upload events in the Office 365 audit log. Once found, it’s a matter of processing the events to extract useful information!
SharePoint Online generates a lot of events in the Office 365 audit log. You can interrogate the log with PowerShell to create per-user reports of their activities. The Search-UnifiedAuditLog cmdlet finds all the necessary data; after that it’s just a matter of filtering and refining the data and then creating the reports.
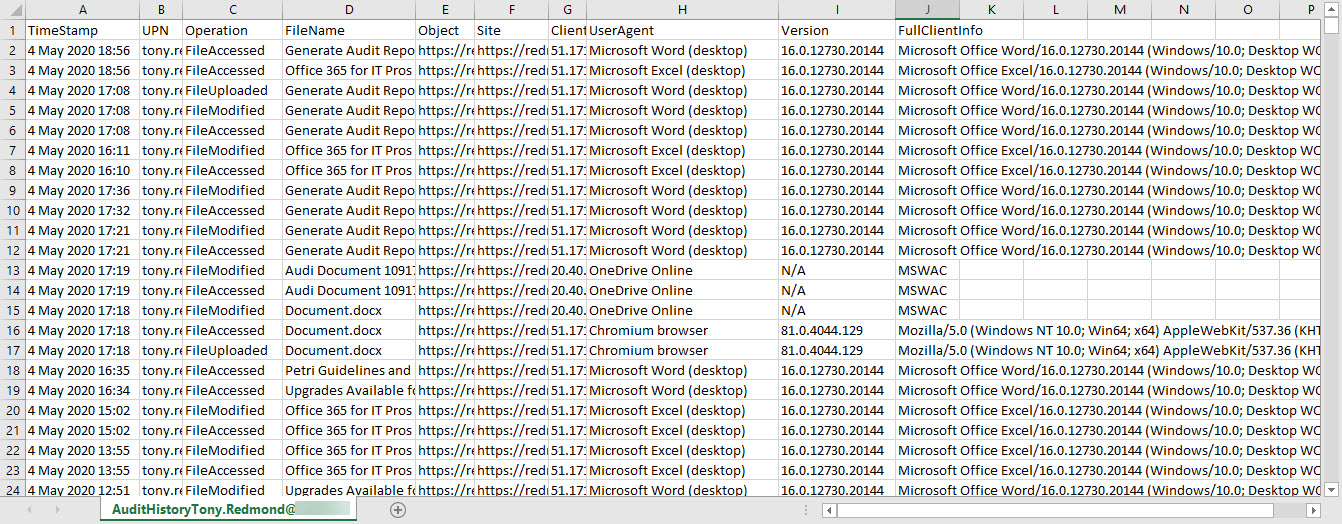
Do you need to find out who updated a SharePoint Online or OneDrive for Business document? Use PowerShell to search the Office 365 audit log for document events and the complete history is available. Well, at least the last 90 days’ history – or 365 days if you have the necessary licenses.
The SendAs audit event is logged when someone uses the send as permission to send a message from an Exchange Online mailbox. The events are stored in the Office 365 audit log and can be found there with an audit log search. However, things aren’t as straightforward as they are on-premises because some other types of delegated messages turn up in searches. Fortunately, we have a script to help.
Microsoft has released information about high-value Office 365 audit events and audit event retention policies. Both are part of a Microsoft 365 Advanced Audit offering. The MailItemsAccessed event is the first high-value audit event (we can expect more) and the retention policies are used to purge unneeded events from the Office 365 audit log.
The email addresses for Teams channels are interesting objects. Messages sent to channels start conversations in the target channel and are also captured in SharePoint. Any team member can enable or disable the ability of a channel to receive email by creating or removing email addresses and no admin control exists to stop this happening. Events captured in the Office 365 audit log reveal when email addresses are created or removed, meaning that you can at least know what’s going on.
Office 365 Groups (and their underlying teams and sites) can be removed by user action or automatically through the Groups expiration policy. By examining records in the Office 365 audit log, we can track exactly when groups are soft-deleted followed by permanent removal 30 days later. All done with a few lines of PowerShell and some parsing of the audit data held in the records.
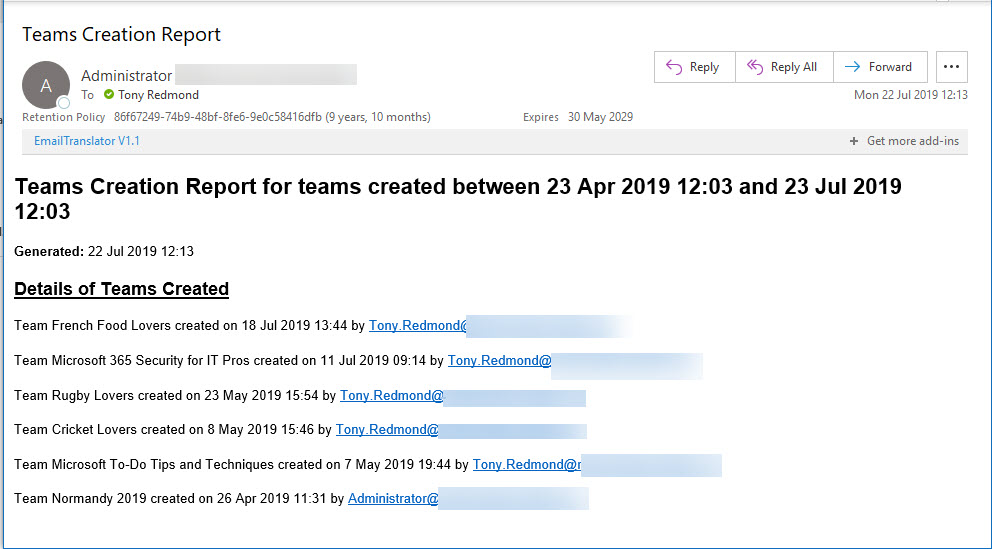
Office 365 Activity Alerts don’t seem to be working too well these days. At least, that’s what we found when we tried to create an alert for Teams creation events. Never mind, PowerShell will do the job as we can quickly whip up a PowerShell script to find audit records for team creations and put them into an email.
Exchange Online writes audit records into the Office 365 audit log when messages are deleted by delegates and administrative action. We can analyze the audit records to find out who deleted a specific message. Some challenges exist to interpret the audit records for admin-generated deletions (for example, when you run Search-Mailbox), but it’s easy enough to code the necessary checks in PowerShell.
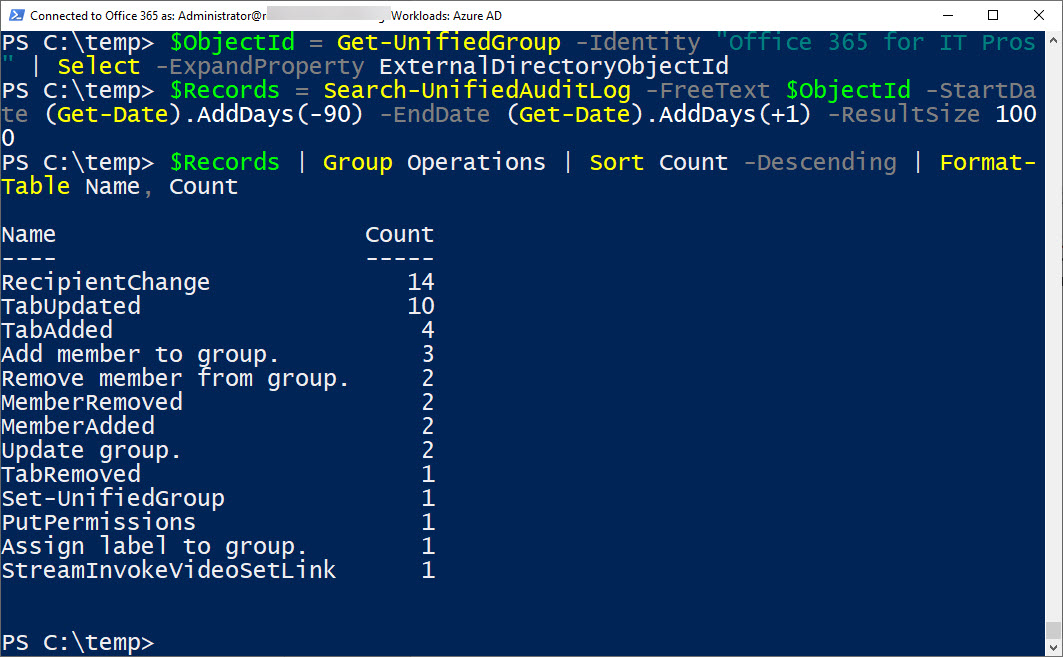
On May 7, Microsoft eventually fixed a truncation bug that affected group events (creation, add member, etc.) ingested into the Office 365 audit log. The fix took far too long coming and the overall response is certainly not Microsoft’s finest hour. Audit events, after all, are pretty important in compliance scenarios and it’s not good when those events are incomplete.
The modern SharePoint Admin Center introduces the ability to rename the URLs for SharePoint site names. This responds to a longstanding customer request and makes it possible for site names to reflect what users see elsewhere in Office 365 groups or Teams. It’s a small but welcome change in the fit and finish category.
In one of those interesting (but possibly worthless) facts discovered about Office 365, we find that audit records are captured for Teams compliance records written into Exchange Online group mailboxes. The Search-UnifiedAuditLog cmdlet reveals details that we can interpret using some techniques explained in Chapter 21 of the Office 365 for IT Pros eBook.
Security alerts from Office 365 Cloud App Security now flow into the Office 365 Audit Log, which means that you can run the Search-UnifiedAuditLog to find the alerts. Unhappily, more work than should be needed is necessary to extract the interesting information from the alert records.