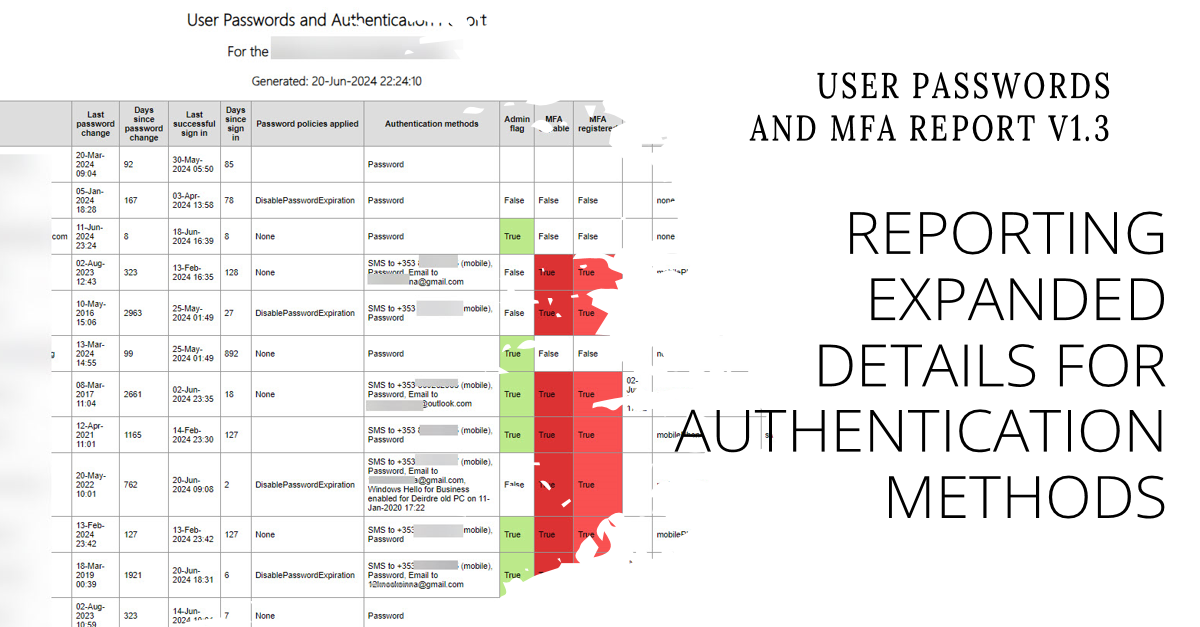
V1.2 of the User Passwords and MFA report includes the names of authentication methods registered for user accounts. V1.3 expands the amount of detail reported for each method, such as the phone number used for SMS challenges, or the email address used for SSPR. It’s a small but important detail that’s useful to administrators. However, it also comes with a potential privacy issue, so the script must handle that too.
Microsoft has moved retention processing for SharePoint Online, OneDrive for Business, Teams, and Yammer from the Managed Folder Assistant to a new retention assistant. (background processing job). It’s part of an effort to use workload-agnostic processing whenever possible to perform retention actions across Microsoft 365.
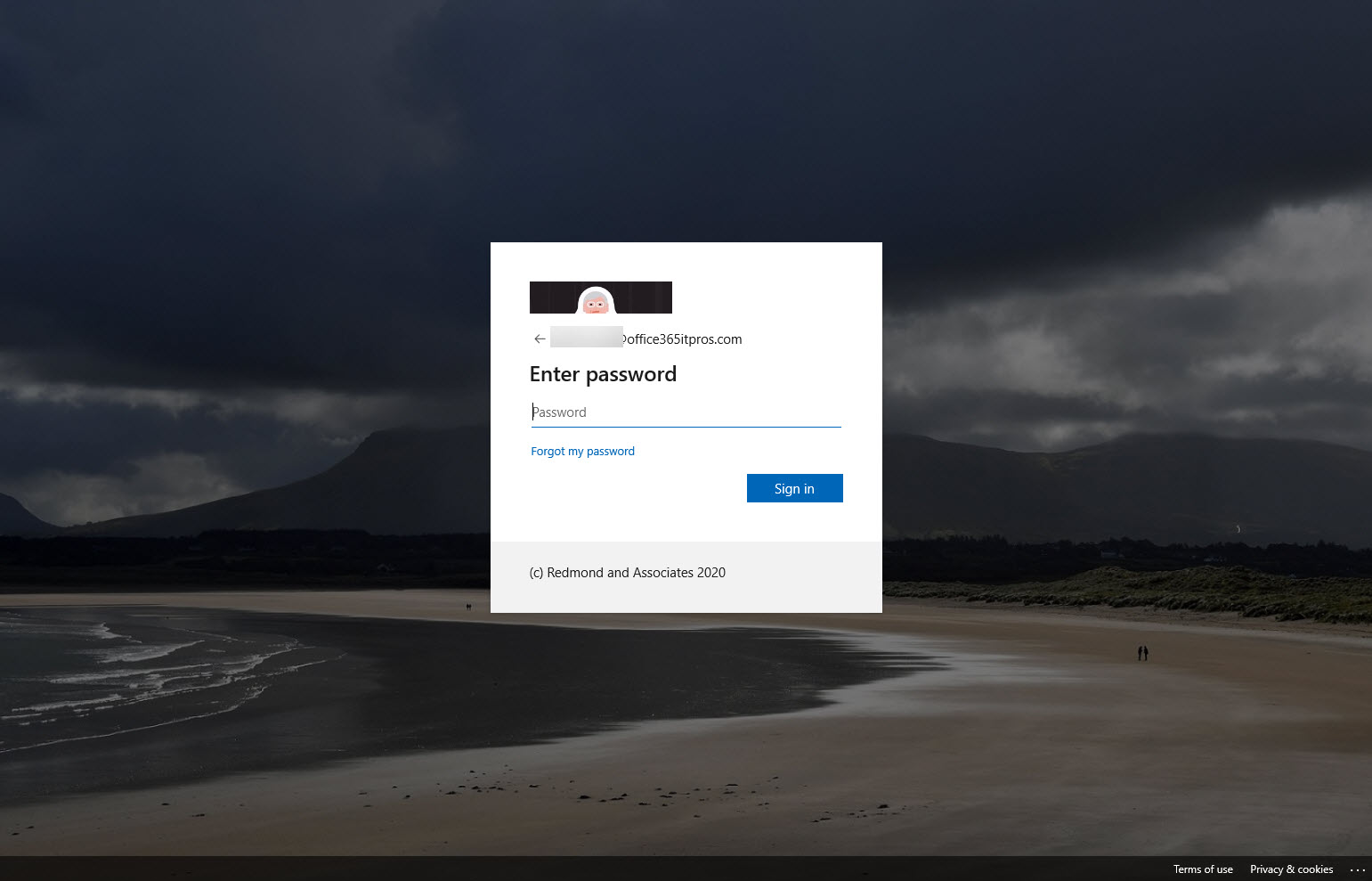
Azure Active DIrectory is getting a slimmed-down background image to help with bandwidth-constrained locations. Office 365 tenants with custom backgrounds won’t see the change. Customizing the appearance of the sign-in screen is easy if you prepare. And to finish up, we have pointers to a set of videos about how Azure Active Directory authentication works.
Microsoft makes a strong case that all Azure Active Directory accounts should be protected with multi-factor authentication (MFA). That’s a great aspiration, but the immediate priority is to check accounts holding administrative roles. This post explains how to use PowerShell to find and report those accounts.
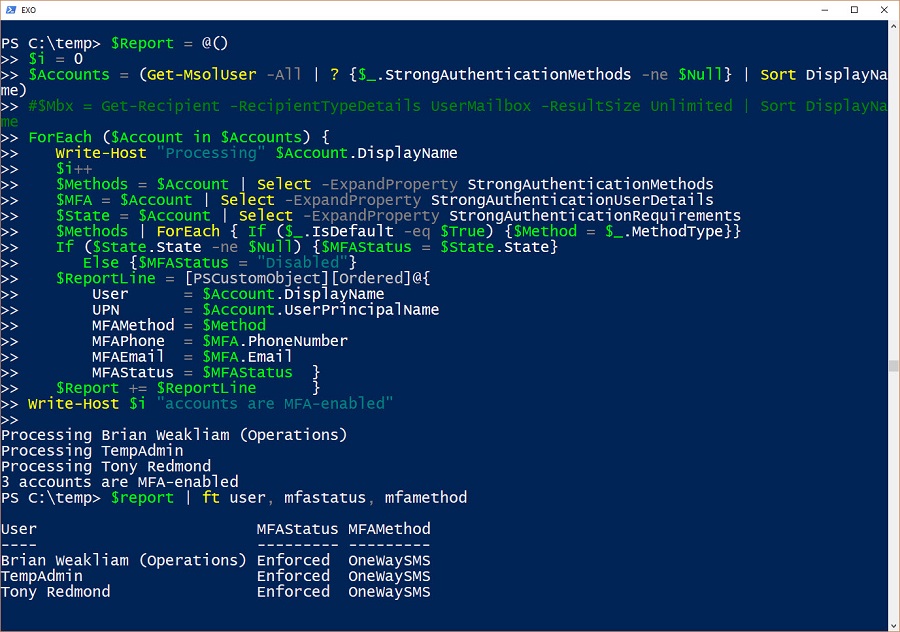
When a problem arises, it’s good to know what user accounts are affected. In the case of the recent MFA outage, the need existed to report the list of accounts that were MFA-enabled. Here’s how to do the job with PowerShell.
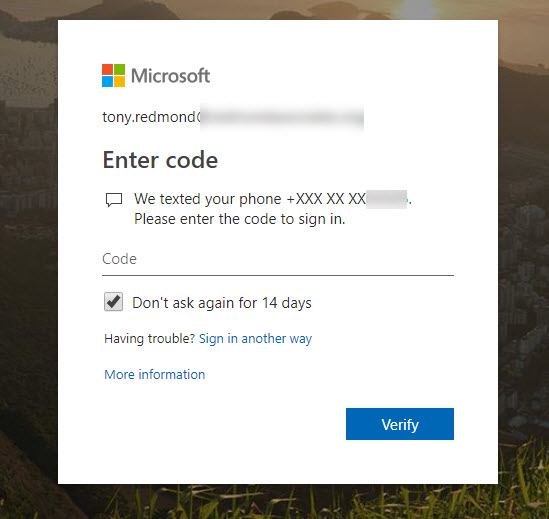
Microsoft’s Azure-based multi-factor authentication (MFA) service experienced a service outage on November 19. Does this mean that we should disable MFA for accounts?