Shared mailboxes have Entra ID accounts. No one needs to sign into the accounts because Exchange Online manages connections using mailbox permissions. But it can happen that people do sign into shared mailboxes and if the accounts aren’t licensed, they don’t comply with Microsoft licensing requirements. As explained here, some PowerShell can check for potential licensing violations.
The question of how best to block PowerShell access for Microsoft 365 user accounts deserved some consideration. The answer lies in service principals for the enterprise accounts created by Microsoft to allow PowerShell modules to authenticate with Entra ID. By restricting access to an assigned security group, you effectively block access to anyone outside that group.
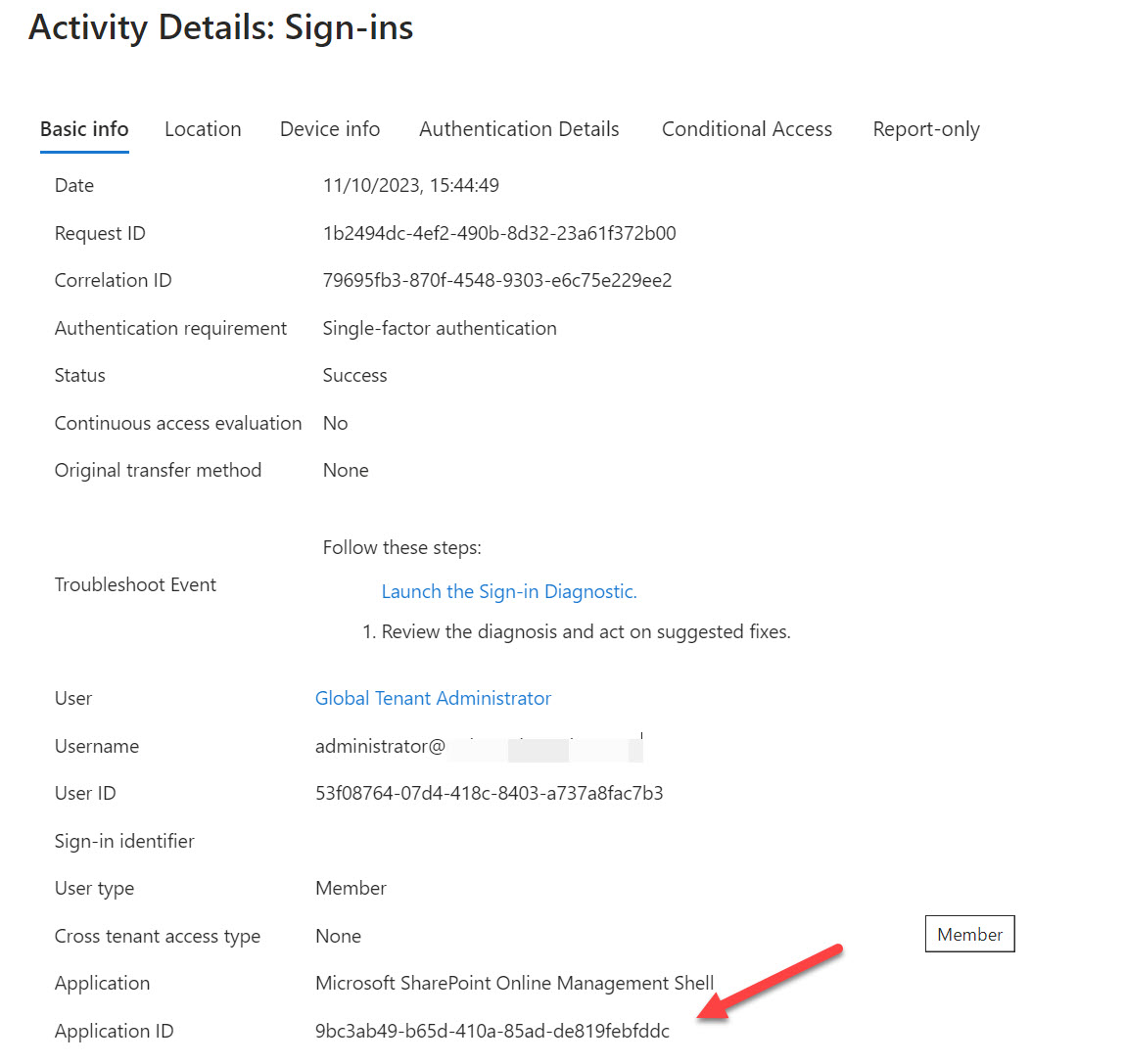
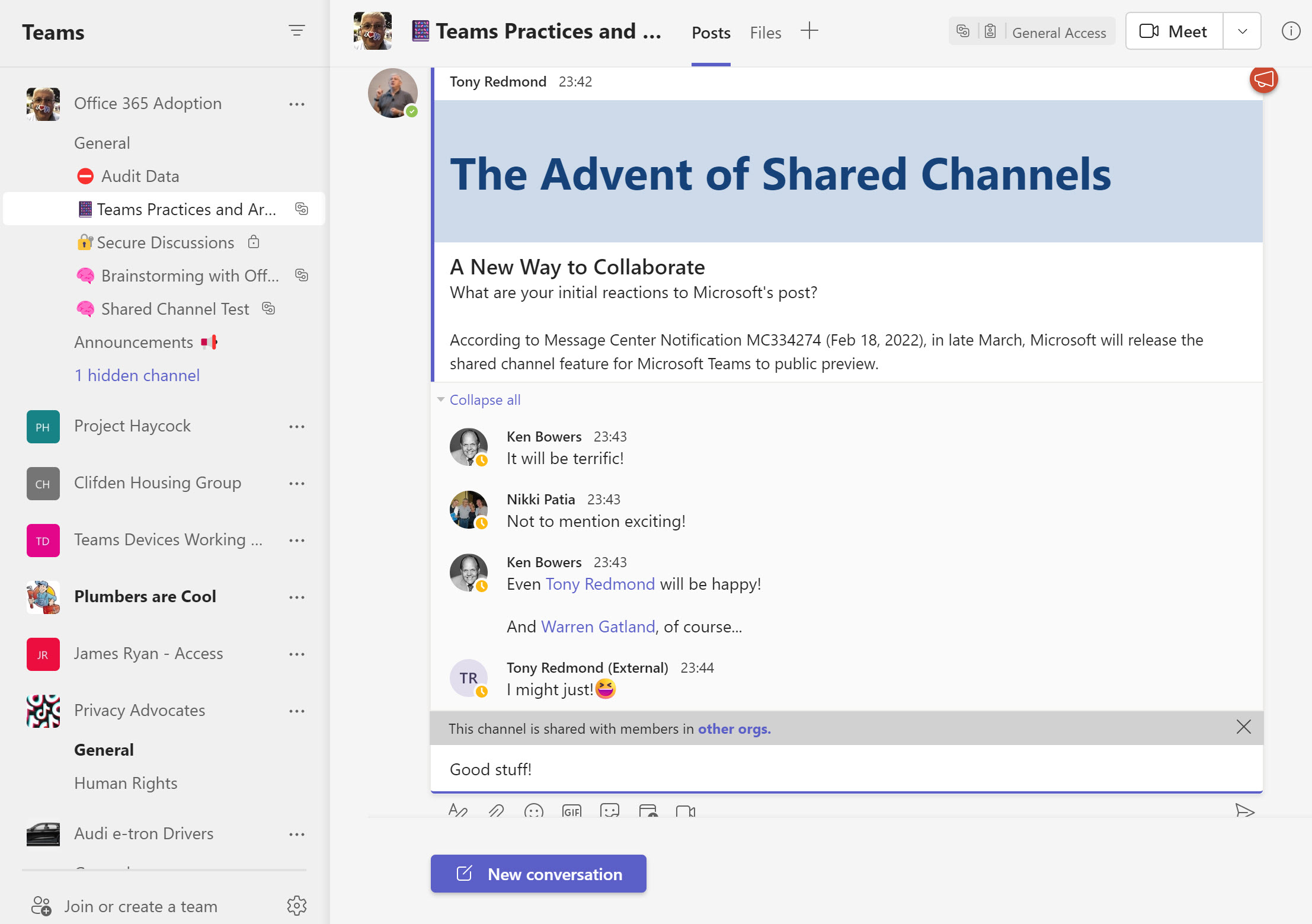
Teams shared channels are now in public preview, meaning that many organizations are trying them out to see how effective a means of collaboration these channels are. One of the administrative challenges of implementing shared channels for cross-tenant collaboration is knowing who uses the channels. An answer can be found in the Azure AD sign-in logs, but only after you go looking.
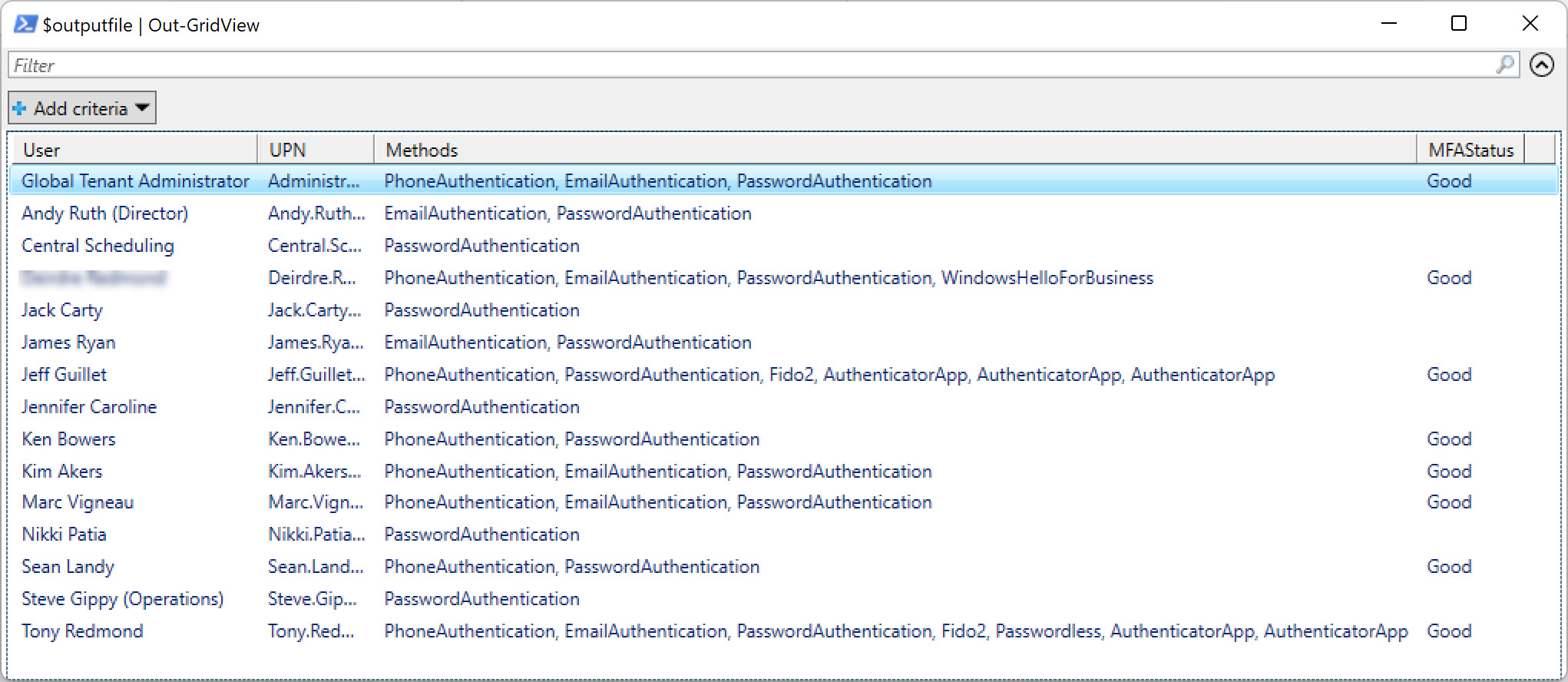
With the upcoming deprecation of the Azure AD and Microsoft Online Services (MSOL) PowerShell modules, it’s time to upgrade scripts which depend on the cmdlets from these modules. In this example, we use the Microsoft Graph SDK for PowerShell to create a report for Azure AD accounts showing the authentication methods each account uses. The idea is to highlight accounts not protected by strong authentication so that administrators can help users to upgrade their protection against attack.